 Superfish, an ill-conceived piece of software that breaks security on Microsoft Windows computers was shipped on some computers made by Lenovo. This has a lot of people worried, but in some cases without reason. In a well-intentioned rush to help consumers -- the affected Lenovo machines are generally consumer models, Thinkpads were not affected, see list below -- some people have put up web pages to detect Superfish. Several media outlets are directing people to these pages. Unfortunately, some of these pages may say that you have a Superfish problem when you do not.
Superfish, an ill-conceived piece of software that breaks security on Microsoft Windows computers was shipped on some computers made by Lenovo. This has a lot of people worried, but in some cases without reason. In a well-intentioned rush to help consumers -- the affected Lenovo machines are generally consumer models, Thinkpads were not affected, see list below -- some people have put up web pages to detect Superfish. Several media outlets are directing people to these pages. Unfortunately, some of these pages may say that you have a Superfish problem when you do not.
(Note: all ESET anti-malware products already detect Superfish. We also have a standalone cleaner you can download here)
False Positives
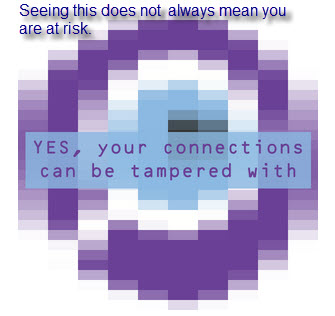 Because of this false problem issue, my advice if you have a Lenovo notebook is to go to this official Superfish Vulnerability page. Check your model number, and if it is on the list, follow the removal instructions here. The tools provided by Lenovo now remove both the Superfish code and the problematic self-signed certificate.
Because of this false problem issue, my advice if you have a Lenovo notebook is to go to this official Superfish Vulnerability page. Check your model number, and if it is on the list, follow the removal instructions here. The tools provided by Lenovo now remove both the Superfish code and the problematic self-signed certificate.
(If your model is not on the Lenovo list, or you have a different brand of Windows computer, you can check what Adware and other undesirable code may be installed on your Windows computer with a free scan that will detect Superfish.)
Also note that if you use ESET NOD32 or ESET Smart Security, then Superfish is already being detected. Furthermore, in addition to detecting Superfish, ESET has been blocking installation of the program across all makes and type of Windows machine because it is classified as Adware.
[Update: an earlier version of this article indicated that Superfish was blocked by ESET as a Potentially Unwanted Application or PUA. In fact, it is automatically blocked as Adware. However, you may want to activate the optional PUA feature anyway: it improves your control over what is installed on your system. Here is an ESET Knowledgebase article about using the PUA feature on Windows computers, and here on the Mac.]
Rage against the machine
So, how false are the Superfish false positives? Both of the "positive" images you see in this post are screenshots from the Lenovo Thinkpad that my company issued to me several years ago. Like many companies, ESET wipes the factory install off all new computers as soon as they arrive in the IT department. A company "image" is then installed -- containing only thoroughly vetted and approved applications -- before the employee gets the machine.
In many security conscious enterprises the employee gets the machine with only user account access, not administrator access. That means no new software can be added by the employee. In other words, Superfish has never been anywhere near my computer, yet two websites suggested by well-known online publications told me that I had a Superfish problem.
This erroneous detection of a problem highlights one of the great challenges in malicious code detection. Yes, you want to know if bad or unwanted software has made its way onto your system, but the waste of time and resources caused by a false positive can be hugely problematic in its own right.
Ironically, the Superfish false positive is likely caused by a type of enterprise security software. A more detailed explanation of this will have to wait for another blog post, but suffice to say many enterprise IT helpdesks are currently fielding calls from users upset about Superfish when in fact they are in no danger at all.
In closing, let me say that be clear: I fully understand the outrage over Lenovo shipping computers with broken security. Calling Superfish an ill-conceived piece of software as I did in my opening sentence is clearly an understatement; however, what is needed right now is a calm approach to fixing the immediate problem of insecure systems. There will be plenty of time to critique Lenovo's actions and the software business model used by Superfish. Hopefully, this incident will provide solid evidence to hardware and software makers that today's consumers thoroughly reject this type of business model.
Note: According to Lenovo, Superfish may have appeared on these models:
G Series: G410, G510, G710, G40-70, G50-70, G40-30, G50-30, G40-45, G50-45
U Series: U330P, U430P, U330Touch, U430Touch, U530Touch
Y Series: Y430P, Y40-70, Y50-70
Z Series: Z40-75, Z50-75, Z40-70, Z50-70
S Series: S310, S410, S40-70, S415, S415Touch, S20-30, S20-30Touch
Flex Series: Flex2 14D, Flex2 15D, Flex2 14, Flex2 15, Flex2 14(BTM), Flex2 15(BTM), Flex 10
MIIX Series: MIIX2-8, MIIX2-10, MIIX2-11
YOGA Series: YOGA2Pro-13, YOGA2-13, YOGA2-11BTM, YOGA2-11HSW
E Series: E10-30
Update: Since writing this, Aryeh Goretsky has written a piece on Lenovo's new approach to bloatware.




