On the heels of the recent announcement that medical insurance firm Anthem was breached, we look at the nuance and impact of a medical record breach versus a medical data breach. They are certainly related, but digging through troves of data containing primarily identity information is significantly different to an attack that focuses on specific treatment of a specific patient.
If an attacker can harvest name, social security number, phone, address, email and the like, that haul has a much wider potential audience than, say, whether or not a patient underwent a specific medical procedure. A stolen medical record containing a lot of detail may sell for a lot of money, but that market is more specialized than the broader market for general identity data.
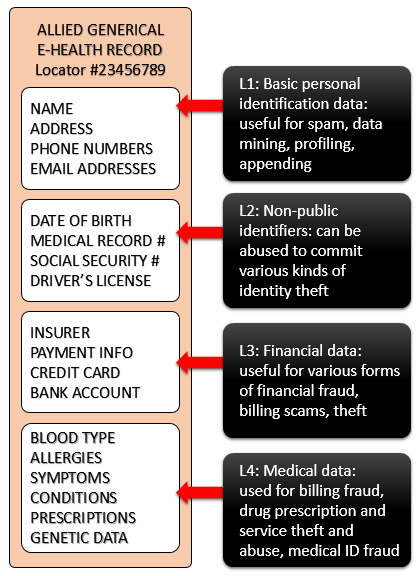 To help folks visualize the different levels of data that thieves might want to swipe from a medical facility, and then abuse, my colleague, Stephen Cobb, created this diagram of a generic electronic health record.
To help folks visualize the different levels of data that thieves might want to swipe from a medical facility, and then abuse, my colleague, Stephen Cobb, created this diagram of a generic electronic health record.
Level one is pretty basic info, things that are fairly easily knowable about you without any hacking, normally sourced through Open Source Intelligence (OSINT) gathering. However, grabbing a big fat collection of such data might still earn a bad guy some black market bucks, say if a spammer needed fresh targets.
The illegal earnings potential goes up a notch if you can grab Level 2 data. Scammers can use that to carry out several kinds of identity theft, creating fake IDs, opening credit card accounts, committing tax fraud (filing fake returns to get a refund) or even use it to answer challenge questions to online accounts, thereby pivoting the attack to new digital beachheads. Even Level 2 data is enough to commit some types of medical ID theft, though the bad guys have no clue how healthy or sick you really are (here’s a pretty scary case of what can be done with just a stolen driver’s license).
Level 3 data just makes all of the above that much easier; plus, it enables new forms of badness. Some crooks prefer taking over an established account to opening a (fake) new one. the number of electronic records or EHRs that actually contain financial or payment data is not clear, but obviously a lot of healthcare entities do handle it at some point, making them a target for digital thieves who turn around and sell it on carder forums.
When you get to Level 4 data, the badness takes on a new dimension. If an attacker has a patient’s full (or partial) history, it's easy to imagine matching up a willing bidder who has a need for a similar medical procedure with a donor record to (roughly) match, in an attempt to get pinpointed specific services they would otherwise have difficulty receiving.
But the options for selling medical history-style Level 4 records may be much narrower in scope than, say, bulk repackaging and resale on the underworld markets of lower levels, appealing to any buyer who wants to assume an identity, spread a wider net and attack other properties, or engage in fraudulent activity which is then blamed on you (if it’s your record that was compromised).
Of course, the threatscape may well change as the EHR becomes more universal. With the proliferation and sprawl of third party providers who are somehow tapped into a cohesive health ecosystem, there will always be various specialized smaller providers whose business is targeted to a specific subset. That's not bad, it's just how the health segment does business; in many cases it leverages strengths of one organization to help another. But it does imply a larger potential attack surface, which has implications for security if the data sprawl is not carefully managed. For example, if an attacker can gain a beachhead in one of the providers in the ecosystem, will they then have an elevated trust relationship with other systems within this ecosystem?
And here's the rub: having instant digital access to all of a patient's medical data (or other sensitive information) wherever a doctor happens to physically be is a wonderful tool, but now we have many more endpoints in question with security environments to understand and corral. This implies an ongoing need, not just for really smart endpoint protection, but also strong encryption, and authentication, as well as sane network segmentation, vigilant network monitoring and reliable disaster recovery.




