ESET’s researchers recently encountered a piece of malware targeting the filling of the forms belonging to the Consulate of Poland. To understand why it is first necessary to have a brief look at the application process for visas.
Belarusians who wish to obtain a visa need to fill out a form to schedule an appointment at the consulate. The form needs to be filed on specific dates (for example, the applications for January 2015 were scheduled for December 20th and 21st) and the number of available appointments is very limited. According to multiple forum threads those appointments are quite difficult to obtain, so some people resorted to writing scripts to automate the process, reducing even more the odds of obtaining an appointment by filling out the form manually. To defeat those bots, the consulate added CAPTCHAs to their website and limited connections to the server to IPs in Poland and Belarus only.
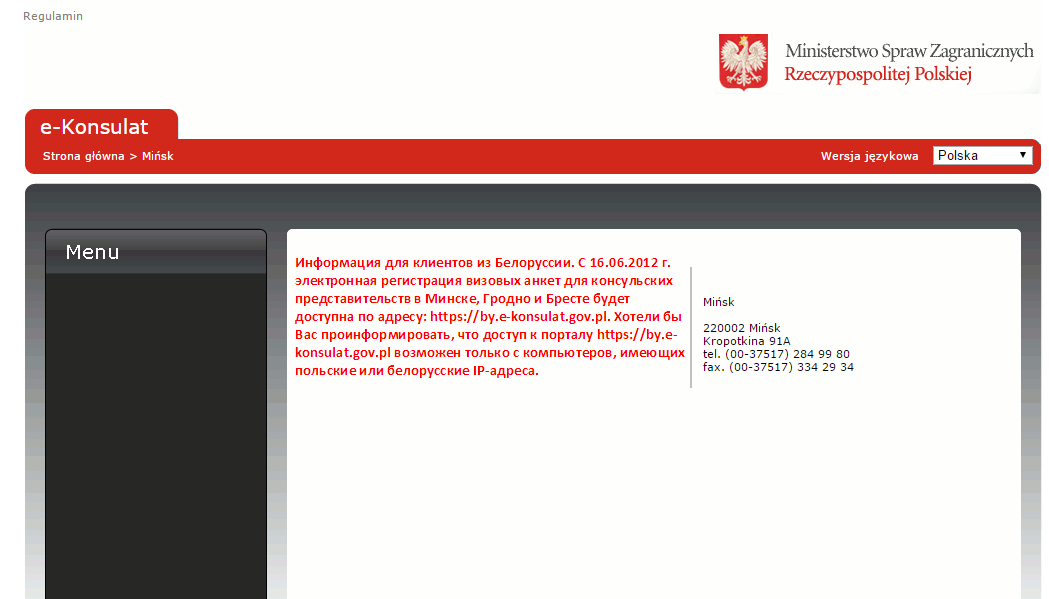
The text in red in the image below can be translated to "The electronic registration of visa applications for consular missions in Minsk, Grodno and Brest is available at: https://by.e-konsulat.gov.pl. We would like to inform you that access to the portal https://by.e-konsulat.gov.pl possible only with computers that have Polish or Belarusian IP-address."
Apparently someone decided to go a step further and build a botnet specifically for the purpose of filling out the forms. This is where a piece of malware, MSIL/Agent.PYO, enters our story. It is composed of multiple components: a downloader (we found 2 different versions being used, one written the C# and another in C++), an updater, and the main component for which the original name is “Konsulat.RemoteClient”.
The main executable is obfuscated with .NET Reactor but it also contains embedded modules that are not obfuscated.
The nice thing about .NET programs is that when unprotected they can easily be decompiled with tools such as JustDecompile, dotpeek or ILSpy, generating a source listing quite close to the original including function and variable names.
The program was neatly separated into different modules which also helped the analysis. For example, code for each step of the registration process is contained in a separate class.
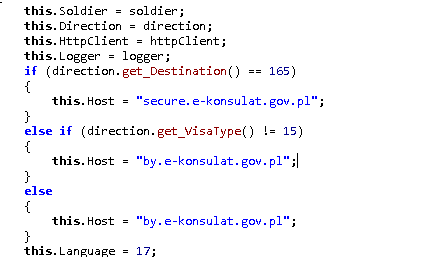
The code responsible for communication with the C&C server is built using WCF (Windows Communication Foundation), which is a framework used to build web services. The main executable contained the following endpoints.
| net.tcp://37.28.153.162:26900/control |
| net.tcp://37.28.153.162:26900/log |
| http://37.28.153.162:7425/ |
Four days before the opening of the registrations, the downloader component of MSIL/Agent.PYO was being distributed via the Nuclear Exploit Kit and only to computers located in Belarus. Statistics for a bit.ly link used in the redirection chain shows that more than 200,000 computers were redirected to the exploit kit in about 6 days.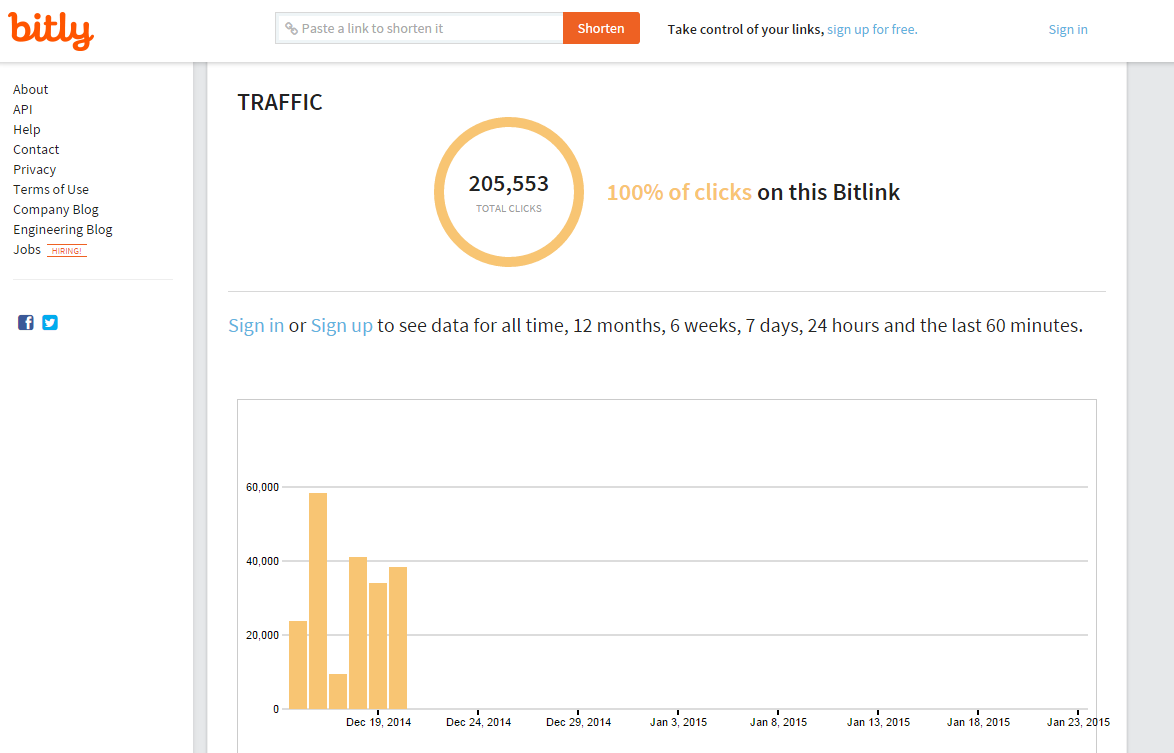 As expected, on December 20th and 21st, the bots started receiving commands to fill out the registration forms. Apparently the malware developer was also busy updating the botnet code at that time, as the version number changed 3 times in the next few days.
As expected, on December 20th and 21st, the bots started receiving commands to fill out the registration forms. Apparently the malware developer was also busy updating the botnet code at that time, as the version number changed 3 times in the next few days.
| Data | Version |
|---|---|
| 2014-12-20 | 1.5.24.0 |
| 2014-12-20 | 1.5.25.0 |
| 2014-12-22 | 1.5.29.0 |
| 2014-12-29 | 1.5.31.0 |
Analyzed samples
| SHA1 | Component | Detection name |
|---|---|---|
| 01baf70db10c506a5ff7629a4a8a30416835769f | Downloader | Win32/TrojanDownloader.Agent.AZM |
| 3a63b784b900688e55b8925cbead856f62535ada | Downloader | MSIL/Agent.PYO |
| 80e49d21e314e17c8d99230444f77820c67318cb | Updater | MSIL/Agent.PYO |
| 254e1ceaa44ce19570a6d4b0812d3b6081a48782 | RemoteClient | MSIL/Agent.PYO |