Today, we published our research on ransomware that emerged in 2014. We have posted blog articles about this threat before, to raise awareness when we realized the criminals were targeting the United Kingdom and Spain.
Win32/Filecoder.DI, also known as TorrentLocker, encrypts its victims’ valuable documents and demands that the victims pay a ransom so that they can download the decryption software that will unlock their files. Ransomware that encrypts files (also known as Crypto-Ransomware) is not something new. Back in 1989, the infamous AIDS trojan demanded US$189 to access your computer files again. More recently, CryptoLocker gained attention from the media after massive number of victims were observed and the criminals behind the threat were identified. Bromium recently published a report comparing recent crypto-ransomware families, in which TorrentLocker is mentioned.
TorrentLocker propagates via spam e-mail messages. It uses various tricks to persuade Internet users to execute the malicious code, which if allowed to run will lock their files. For example, the gang uses a personalized e-mail message, ransom page and payment page depending on the country of the victim. To try to hide their location, the ransom can only be paid in Bitcoins. TorrentLocker now uses a unique Bitcoin wallet for each infection. Prior to this, it used common wallets for multiple victims. The last two “common” wallets were:
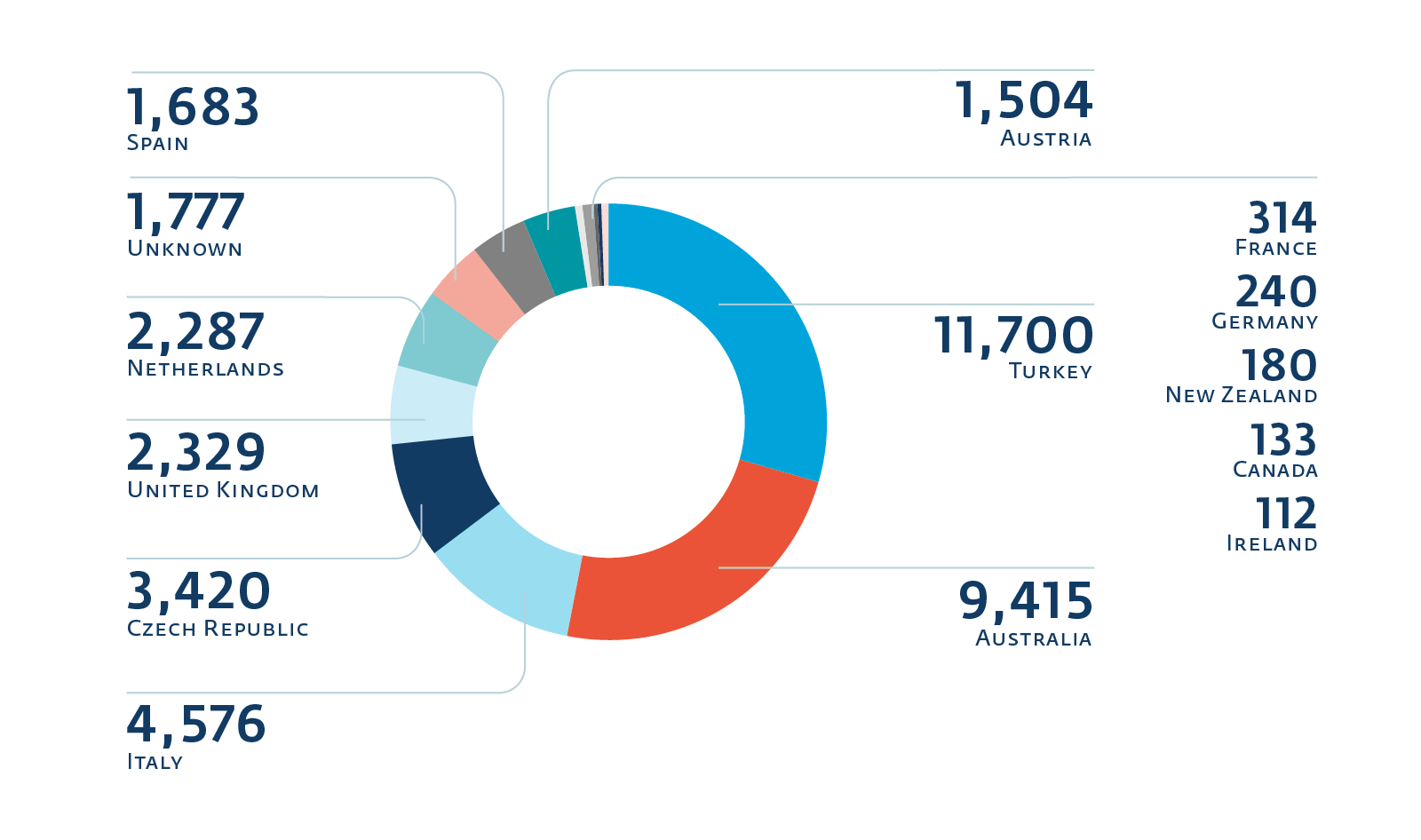
ESET researchers were able to gather a good deal of information from the TorrentLocker C&C servers after they reverse engineered how the servers generate URLs for the payment pages. Using this knowledge, it was possible to ascertain the targeted country (based on the language and instructions on how to buy Bitcoins), the number of files encrypted and the ransom demanded from each of the victims reporting to those C&C servers. We encourage you to read our report if you’d like more information about how this was possible. In the following images you can see how does it spread across countries and how many users paid for the rescue:
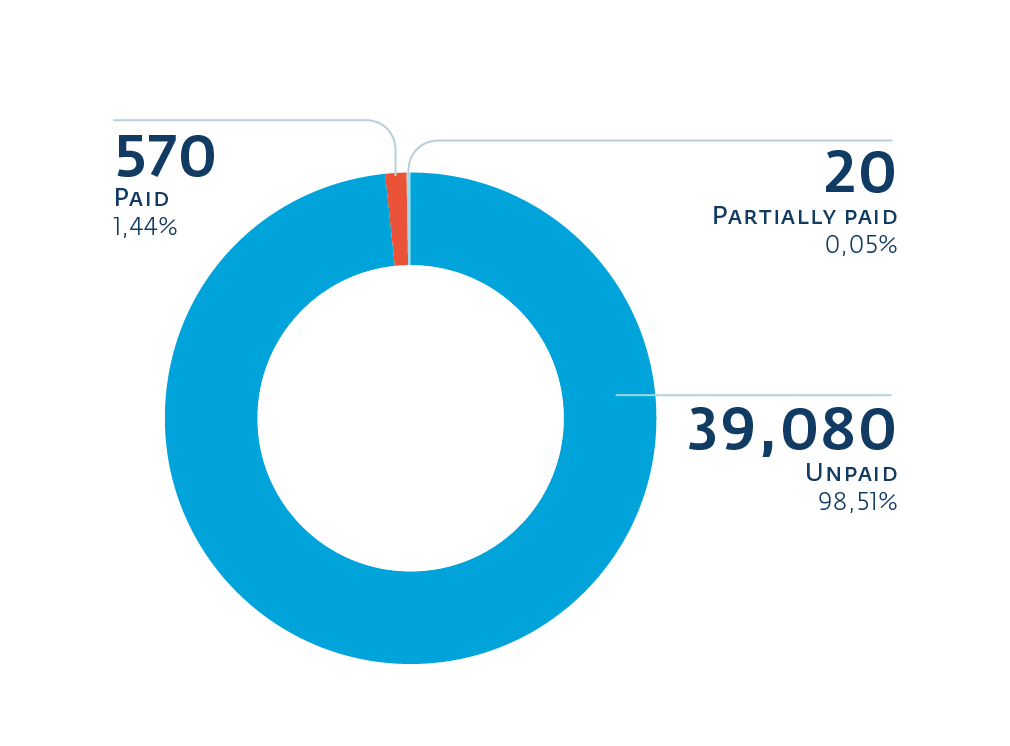
This information is drawn from 39,670 infections. It is hard to tell whether those infections happened in the last month, two months or three months. However, 2,766 happened during the four days immediately before we gathered the data, averaging out at an infection rate of 693 per day.
From those, 1.44% of victims ended up paying the ransom. The number is similar to the 1.3% found in CryptoLocker’s backup database after it was seized.
Recent variants of TorrentLocker use AES-256 in CBC mode to encrypt the files on the infected system, attached storage such as USB flash drives and any network drives they can enumerate. It also encrypts the randomly generated AES key with a 2048-bit RSA public key (hardcoded in the malware) before it is sent to the C&C server and appended to the encrypted file. We would have loved to create generic decryption software, but we did not find any weakness in the cryptography that would allow us to do so without having the private RSA key.
We also found clues that link TorrentLocker with a threat we previously documented: Hesperbot. In fact, it seems that this gang is authoring and operating both the TorrentLocker ransomware and the Hesperbot banking trojan.