Three weeks ago, iSIGHT Partners discovered a new Ransomware encrypting victims’ documents. They dubbed this new threat TorrentLocker. TorrentLocker propagates via spam messages containing a link to a phishing page where the user is asked to download and execute “package tracking information”. In August, only Australians were targeted with fake Australian Post package-tracking page.
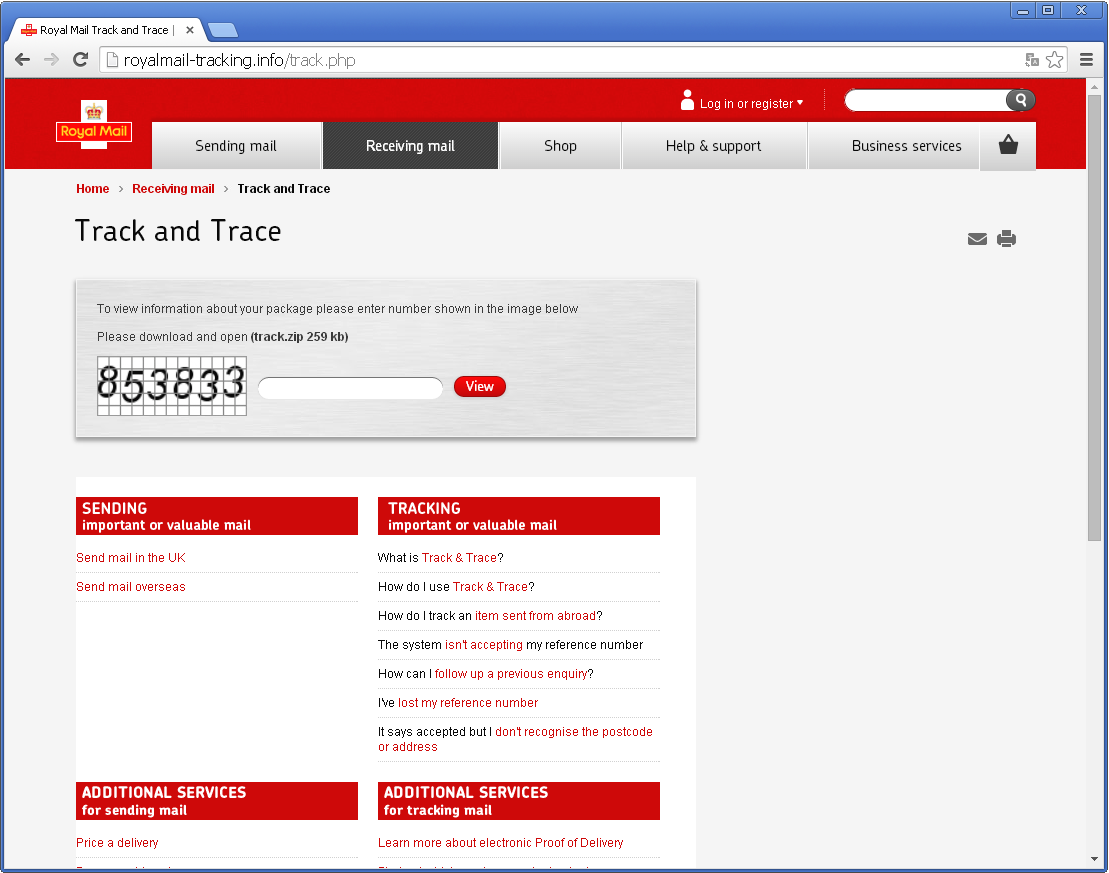
While tracking this new threat, ESET researchers found the malicious gang is targeting new victims. Internet users from the United Kingdom should be aware that fake Royal Mail package-tracking pages are online and distributing TorrentLocker.
The scheme is the same: you type a captcha then click to download a zip file containing the executable payload. It is interesting to note that the fake Royal Mail page will only show if the visitor is from the UK. Filtering seems to be based on the IP address of the request. If the request does not come from a UK IP address, the victim will be redirected to google.com. Three new domains are hosting the fake Royal Mail page:
- royalmail-tracking.info
- royalmail-tracking.biz
- royalmail-tracking.org
![]() royalmail-tracking.info registration information
royalmail-tracking.info registration information
As you can see, registration date for these domains is September 2nd so this campaign started very recently.
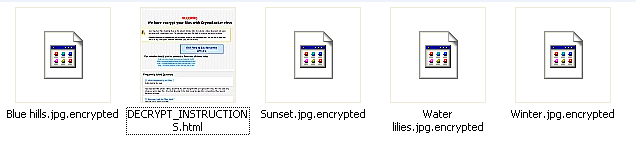 Encrypted files in users' pictures
Encrypted files in users' pictures
 Warning is shown upon execution of the malware
Warning is shown upon execution of the malware
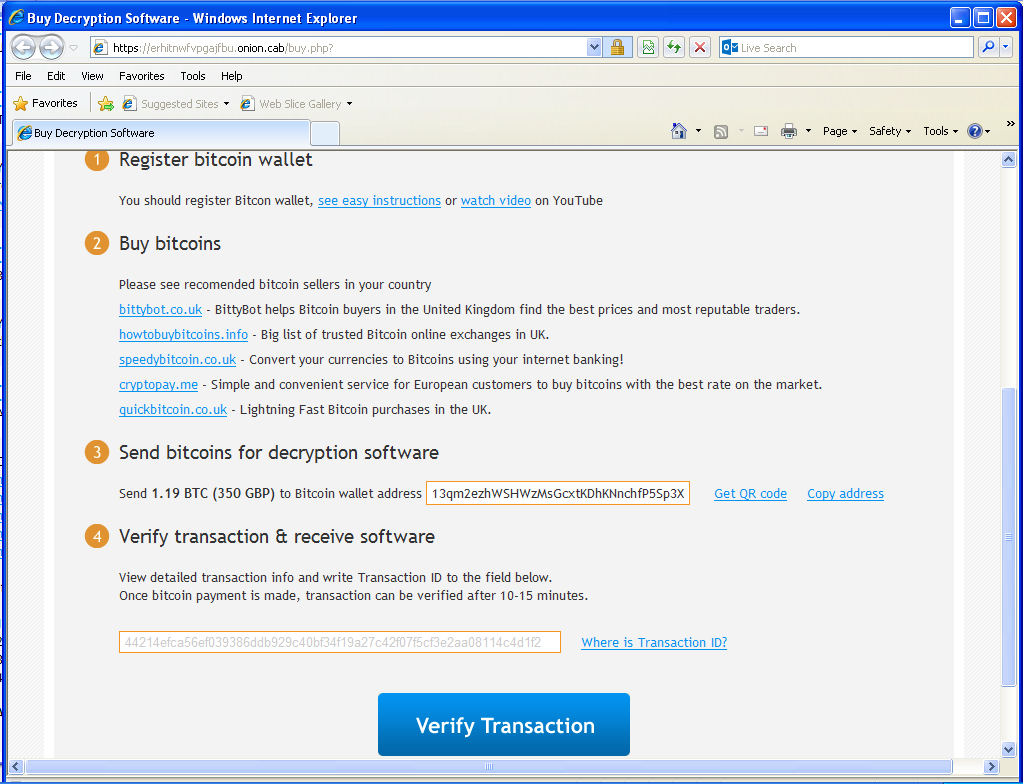
Once installed, victims’ documents are encrypted and they are being asked for a ransom of 350 GBP if paid within 72 hours or 700 GPB otherwise. Payment is done via Bitcoin transaction (1.19 BTC or 2.38 BTC). To hide their infrastructure, the web server is hosted on a .onion host on the Tor network.
To make it is easy for victims to access the web page, TorrentLocker is giving links to Tor2Web nodes so they don’t have to install additional software to reach the .onion website. Interestingly, door2tor.org, the domain name of one of the suggested Tor2Web node, was registered only 2 weeks ago. Perhaps its purpose is only to allow TorrrentLocker’s victims to contact the server selling the decryption software.
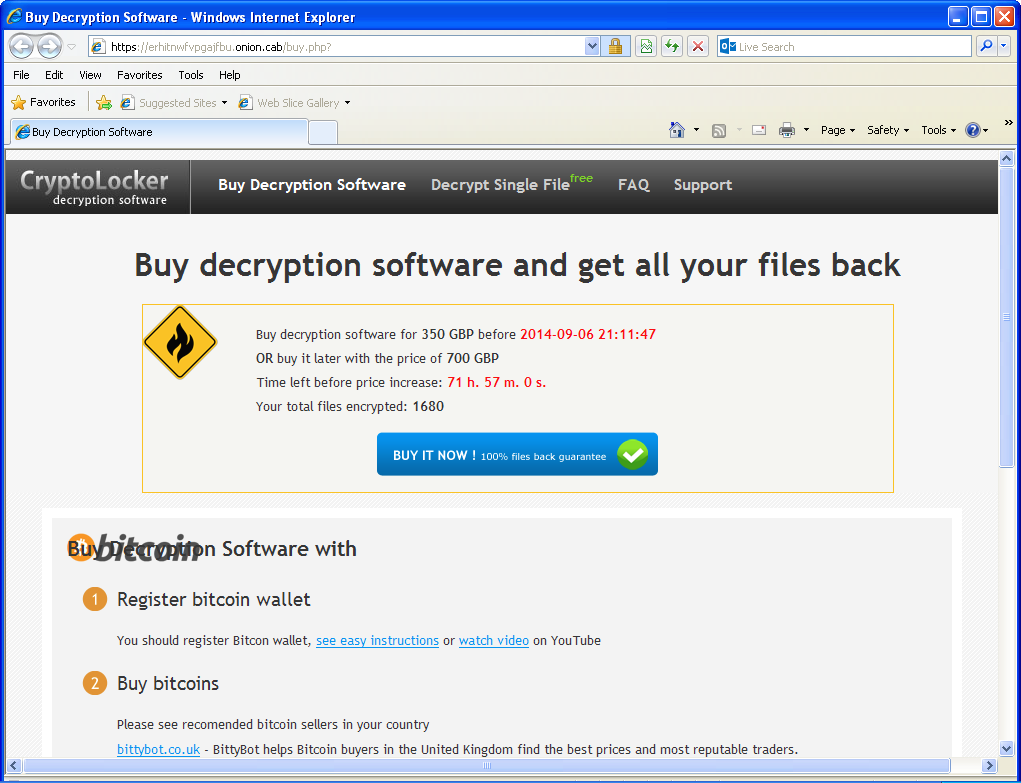 "Decryption software" sold on the Tor network
"Decryption software" sold on the Tor network
This threat caries the TorrentLocker name because it use the “Bit Torrent Application” Windows registry key to store its settings. It is unrelated to the BitTorrent protocol.
The Bitcoin trail
As discovered by iSIGHT Partners, the Australian variant they analyzed asked for Bitcoins to be sent to 15aBFwoT5epvRK69Zyq7Z7HMPS7kvBN8Fg. In our case, the Bitcoin address changed to 13qm2ezhWSHWzMsGcxtKDhKNnchfP5Sp3X. If you look at the transactions on both wallets, the Bitcoins are then transferred to 17gH1u6VJwhVD9cWR59jfeinLMzag2GZ43.
Since March 2014, this Bitcoin wallet has transferred over 82 272 BTC. With 1 BTC currently valued at US$480, the total transactions are roughly equal to 40 millions US$. This wallet has been associated with other scams in the past, including wallet stealing and selling fake mining hardware. We do not know if this account is owner by the TorrentLocker gang or it is some kind of exchange service used by different groups.
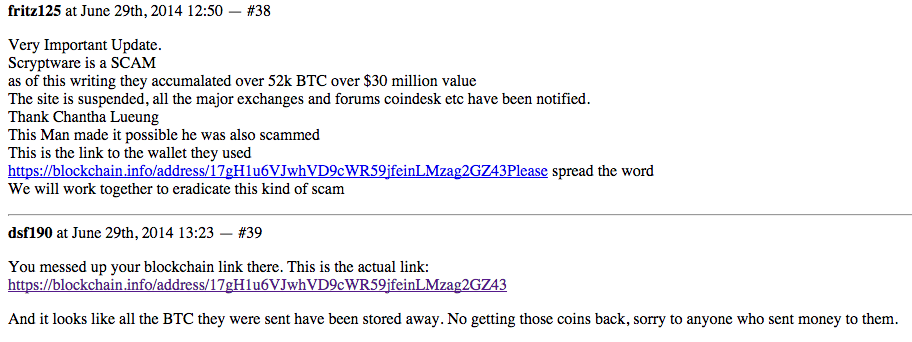 Screenshot of a discussion on Hashtalk (now offline, retrieved from Google Cache)
Screenshot of a discussion on Hashtalk (now offline, retrieved from Google Cache)
ESET products detect this threat as Win32/Filecoder.NCC or Win32/Injector.
SHA-1 hashes
- 491C8276667074B502BD98B98C74E4515A32189B (exe)
- 46A2426D7E062E76D49707B58A5DF28547CBC0F4 (zip)
- 7C62651C5F4CB1C780C8E9C4692F3BF24208A61E (exe)