UPDATE: Our developers have created ESET Simplocker Decryptor, an easy-to-use tool to decrypt files that have been encrypted by Simplocker.
To install the application, please download it from Virus Radar with your device or scan the QR code below. To install the app, you must allow installation from Unknown Sources (Settings -> Security -> Unknown Sources).
A detailed ESET KnowledgeBase guide to dealing with the malware offers guidelines on how to spot and get rid of the malware on Android handsets.
Since our initial discovery of Android/Simplocker we have observed several different variants. The differences between them are mostly in:
- Tor usage – some use a Tor .onion domain, whereas others use a more conventional C&C domain.
- Different ways of receiving the “decrypt” command, indicating that the ransom has been paid.
- Different nag screens, different ransoms (and different currencies as well – we’ve seen Ukrainian hryvnias as well as Russian rubles).
- Use of imagery – some display a photo of the victim taken with the phone’s camera to increase the scareware factor.

Figure 1 - Android/Simplocker.B nag screen with victim's photo and Russian rubles instead of Ukrainian hryvnias
The simplistic encryption approach using AES with a hard-coded password is still present in most samples seen in the wild and some variants don’t contain the filecoder functionality at all, and act as ransomware of the lockscreen type.
As mentioned in our previous posts, the threat is mostly concentrated in Ukraine and Russia. While the malware may display traits of a proof-of-concept, it is indeed spreading in the wild and can cause headaches for infected users.
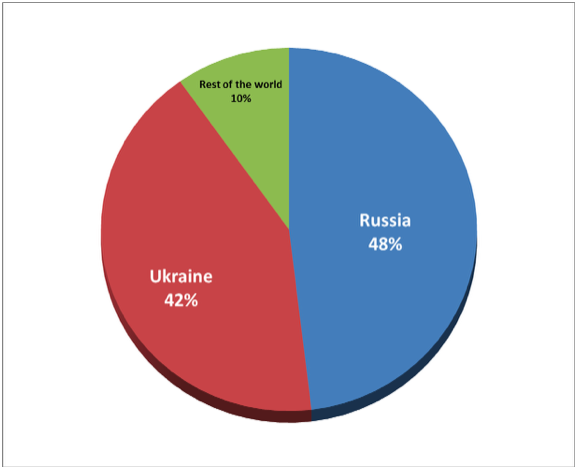
Figure 2 - ESET LiveGrid(R) regional telemetry for Android/Simplocker
One of the most important questions when a piece of malware is discovered concerns the infection vector – or vectors – that is, in what ways can it get into a victim’s device? ESET LiveGrid® telemetry has indicated several infection vectors used by Android/Simplocker. The “typical” ones revolve around internet porn – some malicious apps pretended to be an adult video, an app for viewing adult videos, etc. – or popular games like Grand Theft Auto: San Andreas, and so on.
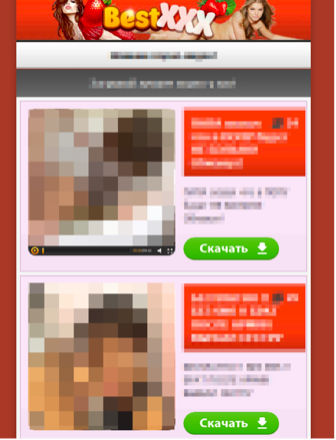
Figure 3 - Adult website serving Android/Simplocker

Figure 4 - Fake GTA San Andreas icon
We have, however, noticed a different dissemination trick that’s worth mentioning – the use of a trojan-downloader component. Using trojan-downloaders to “dynamically” download additional malware into an infected system is common practice in the Windows malware world – and while this is not the first case we’ve seen – it is still noteworthy on Android.
Using a trojan-downloader is a somewhat different strategy for smuggling malware into an Android device, compared to traditional social engineering (e.g. by using porn, as in the example above) or more sophisticated techniques relying on exploitation of software vulnerabilities.
One trojan-downloader (detected by ESET as Android/TrojanDownloader.FakeApp) we’ve analyzed was attempting to trick the user into downloading a fake video player – which, as you might have guessed, was the Android/Simplocker trojan. The reason why the trojan-downloader strategy has a greater chance of slipping under the radar of Android market application scanning (such as Bouncer on the official Google Play, for example) or even escaping the notice of a more careful Android user is because:
- All the application does is open a URL outside the app – this does not, in itself, qualify as malicious behavior and
- The downloader has practically no “potentially harmful” application permissions – so even a user who scrutinizes app permissions at installation may allow this one
Furthermore, in the example we’ve analyzed, the URL contained within the app didn’t point to the malicious Simplocker APK package directly. Instead, the trojan was served after a redirect from the server under the attacker’s control. This technique is something to watch out for.
The described trojan-downloader was masquerading as a legitimate app called USSDDualWidget.
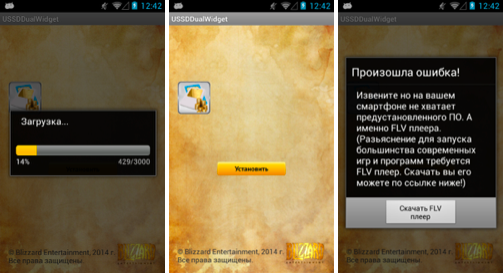
Figure 5 - Trojan-downloader posing as legitimate USSDDualWidget appSHA1 hash
Android/TrojanDownloader.FakeApp: 979020806f6fcb8a46a03bb4a4dcefcf26fa6e4c
Further reading:
ESET Analyzes First Android File-Encrypting, TOR-enabled Ransomware
Ransomware 101: FAQ for computer users and smartphone owners
Android malware: how to keep your device safe from filecoders (and everything else)
securehoney.net | How To Dissect Android Simplelocker Ransomware





