A group of hackers claim to have stolen the personal details of some 650,000 pizza lovers, and have threatened to release them to the world if Domino's Pizza doesn't cough up a hefty ransom.
The hacking group, which is calling itself Rex Mundi, claims to have breached the network of Domino's Pizza in France and Belgium, grabbing customers' full names and addresses, phone numbers, email addresses and the passwords.
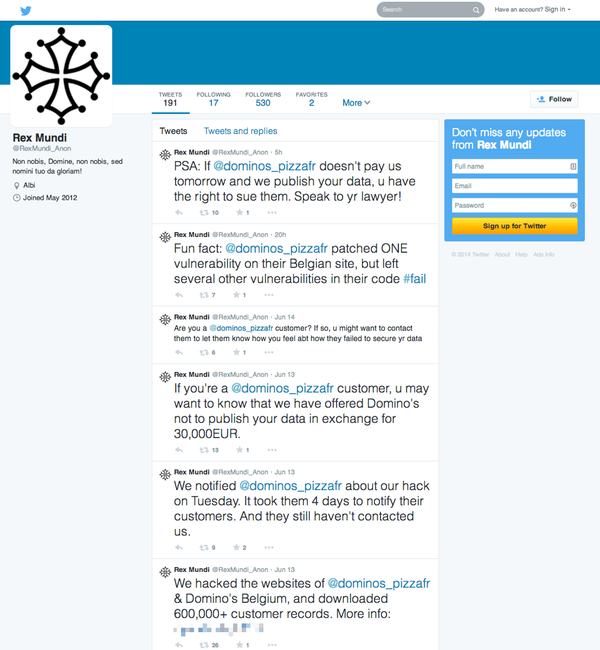
Via their Twitter account (now suspended) the hackers posted a link to a statement about the breach:
Dear friends and foes,Earlier this week, we hacked our way into the servers of Domino's Pizza France and Belgium, who happen to share the same vulnerable database. And boy, did we find some juicy stuff in there! We downloaded over 592,000 customer records (including passwords) from French customers and over 58,000 records from Belgian ones. That's over six hundred thousand records, which include the customers' full names, addresses, phone numbers, email addresses, passwords and delivery instructions. (Oh, and their favorite pizza topping as well, because why not).
Fortunately, there is no indication that payment information has fallen into the hands of the hackers - but there's clearly still plenty to be concerned about for those Domino's customers who have had their personal information exposed.
Domino's France responded to the security breach with a series of tweets, claiming that although it used "cryptage" (encryption), the company believed the hackers to be experienced criminals, and it was deemed likedly that passwords would be cracked:
Domino’s Pizza utilise un système de cryptage des données commerciales. Toutefois les hackers dont nous avons été victimes sont des professionnels aguerris et il est probable qu’ils aient pu décoder le système de cryptage comprenant les mots de passe. C’est la raison pour laquelle nous vous recommandons de modifier votre mot de passe, par mesure de sécurité. Nous regrettons fortement cette situation et prenons cet accès illégitime très au sérieux.
Sadly, there's no mention of whether the sensitive information was salted and hashed.
 André ten Wolde, who heads up Domino's Pizza in the Netherlands, told De Standaard that there were clearly security problems with the firm's server.
André ten Wolde, who heads up Domino's Pizza in the Netherlands, told De Standaard that there were clearly security problems with the firm's server.
At the same time he confirmed that the company would not be paying any ransom of the hackers.
Good for him, and good for Domino's Pizza.
Clearly any hack is very bad news - both for the thousands of potential innocent victims, and for the corporation which has been hit by a criminal hack.
It's easy to point the finger of blame at the corporation for not protecting its customers data properly, and there are no doubt a lot of angry people in France and Belgium writing now ordering an Indian takeaway as a form of protest.
But we have to make a stand against criminals who attempt to blackmail and extort money out of the corporations they are attacking via the internet. We saw a fine stand made by Feedly the other day when hackers attempted to extort money, and I'm pleased to see Domino's Pizza not bowing to the hackers' demands either.
If companies cave in and pay ransoms to internet attackers the only thing that is certain is that there will be more internet attacks.
I asked ESET security expert David Harley whether he felt the Feedly and Domino's attacks were the sign of a new era of cyber-extortion.
Here's what he had to say:
The Feedly story appears to have been just a DDoS attack, not a credentials breach. There’s nothing new at all about that: even in the early 2000s, UK agencies were quietly cooperating with private companies to deal with extortion attacks based on "pay up or we’ll keep on DDoS-ing you".Historically, online casinos and similar sites have been persistently targeted, but there’s no reason why an attacker wouldn’t consider any site dependent on keeping its online services available a likely target for extortion.
Extortion based on the threat of data release is a little more unusual, but not unknown.
Since stolen data can’t usually be ‘given back’ in such a way that you know the attacker can’t make further use of it, it makes sense to look at other means of mitigation rather than relying on the attacker’s ‘good faith’. I.e., alerting customers, advising them to change passwords, improving database security.
Similarly, it’s almost a given that paying up under threat of DDoS is unlikely to be a permanent solution.
So, the message is clear.
If you're the victim of cyber-extortionists, don't give in to the blackmailer's demands.
Even though you might be at risk of personal or commercial embarrassment, or potential financial loss, it's always better to contact the crime-fighting authorities than get into bed with the criminals. Of course, you should also put some serious resources into exploring what security holes might exist in your company's operations - and making sure you are better defended in the future.
And, if you're a customer of Domino's and fear that your details may have been exposed by this attack, make sure that you are not using your pizza-ordering password anywhere else on the net.
After all, if the hackers manage to extract your password from Domino's database they might attempt to use it to unlock your other online accounts too.
It's good practice to always use different passwords that are hard-to-crack for different websites. Reusing passwords is a recipe for disaster. Anything less than proper password practices could end up with hackers getting their hands on your hard-earned dough.




