Stop me if you’ve heard this before...
While I was in London recently for the InfoSec exhibition and some other meetings, my wife received a call from a lady with a heavy Indian accent, who told her that she had errors on her computer caused by viruses, and offering to remove them for her. For a fee, of course…
Nothing novel about that, you might think, if you’ve followed some of the many articles we’ve posted on the topic of fake support calls – except that it was actually the first of these scam calls we’ve received in months, whereas at one time we might get similar calls two or three times a day. That evidently doesn’t mean the problem has gone away, though. Nor does it mean that the scam isn’t continuing to evolve.
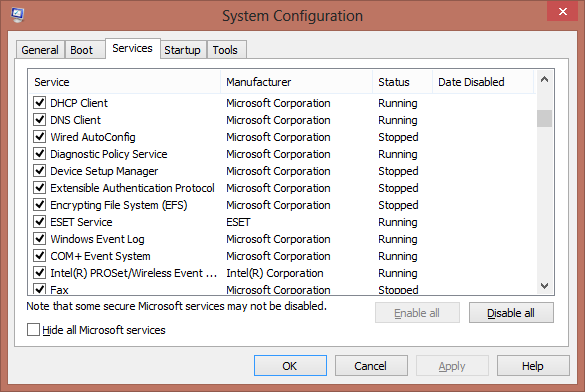
A recent post by Jerome Segura describes how he received such a call and played along to see how far it would go. Much of the process he describes may be familiar to you: for example, the use of Event Viewer and Prefetch to convince the victim that there are problems on his Windows PC that need addressing. However, Segura also describes a trick along the same lines, but that I haven’t seen used before, using the system utility MSCONFIG. The following graphic shows the sort of result that can be seen under the services tab. (The screenshot shows the Windows 8 version: if you're using an earlier version, it may look a little different.)
The story here seems to be that each service shown as “Stopped” in the Status column is symptomatic of a system problem or of malware. In fact, while the System Configuration utility can certainly be used to help with troubleshooting, the fact that a service is shown as “Stopped” simply means that it isn’t running. It certainly doesn’t prove the existence of a problem. Different utility, same kind of misrepresentation.
A further interesting feature mentioned in Segura’s account is that while the scammers were eager to ‘prove’ to him that his system was under threat by running (and misusing) no less than three system utilities, they seem to have been insistent that they could not ‘help’ him until he actually asked them to do so. Segura suggests that ‘I think this might be another technique used to cover themselves, as in I willingly asked them to help me‘ and I think he’s probably right. That suggests that even if recent legal countermeasures aren't by themselves driving the scammers off the scene, they are at least being more cautious, in the hope of mitigating any later accusations of actively fraudulent behavior.
However, once the ‘technician’ had been allowed access to Segura’s system using Team Viewer, the tech seems to have reacted angrily when he realized that the payment he expected via PayPal wasn’t going to happen, deleting files and trashing the ethernet driver, effectively trashing the Internet connection. (Not permanently, though: naturally, Segura was using a virtual machine, not a ‘real’ system.) Segura observes that “I wasn’t going to play tricks on them or make fun of them. I just wanted to see for myself how the scam was conducted and learn more about it.” I think it’s likely, though, that the scammer simply assumed that Segura was deliberately wasting his time (as so many people have taken to doing), and wanted to punish him, though if the scammer had given it more than a moment’s thought, he’d probably have realized that the machine he was vindictively trashing was in fact a virtual machine and that he was throwing away any future legal or moral defense in return for inflicting a minor inconvenience.
Segura made an audio recording of the conversation and posted it on YouTube, so if you find his blog interesting, you might want to check that out too.
The moral there would seem to be: if you are going to do a little scammer-baiting, make sure you do it on a virtual machine so that if you do give the scammer access to your machine, he won’t be able to do any real damage: it’s usually quick and easy to restore the system.
While the backroom boys in Kolkata still seem to be researching simpleminded ways to misuse system utilities to mislead potential victims, there are indications that some convergence between active malware and support scam social engineering may be underway. If you read a recent post by Jean-Ian Boutin you’ll be aware of an attempt to combine the use of unequivocal malware (a program that combines fake AV functionality with a basic screenlocking capability à la ransomware) with support scamming, by driving the victim to contact a ‘helpline’. Once the victim makes the call, the con is much the same as in the cold-calling scams we're already so familiar with, but now the scammer can say that the victim called asking for the service, thus sidestepping legal countermeasures based on legislation that proscribes unsolicited cold-calling. Whether this lateral arabesque would stand up to close judicial scrutiny remains to be seen, but it’s clear that someone is putting some serious effort into prolonging the scam’s lifecycle. (If you haven’t read Jean-Ian’s post yet, I heartily recommend it.)
Meanwhile, Virus Bulletin’s Martijn Grooten, with whom I’ve had many a productive chat on matters relating to support scams, recently drew my attention to what might just be another variation on the theme. For Ars Technica, Jon Brodkin reported on The spammer who logged into my PC and installed Microsoft Office, hinting at a possible connection with support scams. To me this reads less like a call centre scam than a lone operator trying to make a few bucks by installing Office, using a keygen to sidestep Microsoft’s licensing process, but it does suggest both an alternative support (black) market and an alternative solicitation approach – “Itman Kool2” looks for customers using SMS spam and a Yahoo mail account. It's consistent with the new 'you called us, we didn't call you' approach, and it’s consistent with the common support scammer practice of charging for installing an evaluation version of security software. Will we see them making more use of these channels to get the victim to come to them? I don’t know, but I’ll be keeping an eye open.
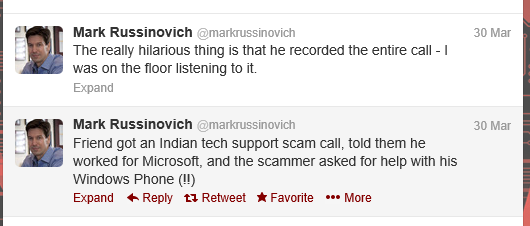
And finally, a further hat tip to Martijn (nice to talk with you at InfoSec, by the way!) for drawing my attention to this amusing little anecdote from Mark Russinovich via Twitter:
I wonder if they got the opportunity to trash his phone remotely. I guess not: that would be unethical.
Here are a couple of the papers Martijn and I, together with Steve Burn and Craig Johnston, put together last year for the 2012 Virus Bulletin and CFET conferences: between them, they offer a pretty comprehensive view of the support scam issue, at least as we understood it at the time.
- FUD and Blunder: Tracking PC Support Scams
- My PC has 32,539 errors: how telephone support scams really work
And another hat tip to Safetica’s Lyle Frink, with whom I also had an interesting chat at InfoSec. Some support scam-related topics came up in that conversation that I may well follow up on in the near future. In my copious free time…
David Harley CITP FBCS CISSP
ESET Senior Research Fellow