Power Loader is a special bot builder for making downloaders for other malware families and yet another example of specialization and modularity in malware production. The first time Power Loader was detected was in September 2012, using the family detection name Win32/Agent.UAW. This bot builder has been used for developing Win32/Gapz droppers (Win32/Gapz: steps of evolution) since October 2012. Starting from November 2012, the malware known as Win32/Redyms (What do Win32/Redyms and TDL4 have in common?) used Power Loader components in its own dropper. The price for Power Loader in the Russian cybercrime market is around $500 for one builder kit with C&C panel. (The image at the top of this post is the product logo used by the seller.)
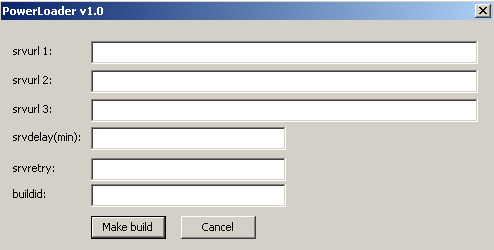
The first version of the Power Loader builder was compiled at the beginning of September 2012. The time stamp of the compiled file is presented here:
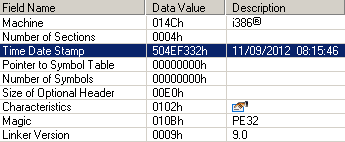
Power Loader uses one main C&C URL and two reserve URL’s. All configuration data is stored into the .cfg section of the executable file. Configuration information is stored in plain text format, not encrypted.
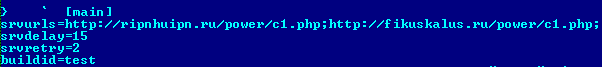
The bot identifier is based on the unique MachineGuid value, which is stored in the system registry using random alphabetical symbols. This bot identifier is used to create the mutex and identify infection status.
Different dropper families have different export tables after unpacking the original dropper executable. The first version of the Power Loader export table looks like this:
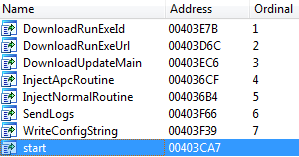
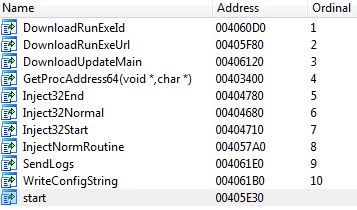
In the first version we didn't recognize the code injection method used to bypass HIPS used in Gapz. But the second version of Power Loader has special markers for the code injection method which is described at the beginning and the end of the shellcode. The export table is presented here:
In the case of Win32/Redyms the export table looks like this:
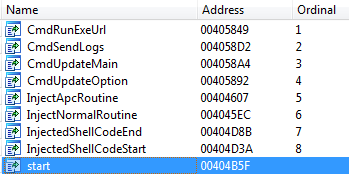
This method of injecting code into explorer.exe is used for bypassing HIPS detection and is based on a technique for injecting code into a trusted process. More details have already been published one of my previous blog posts (Win32/Gapz: steps of evolution) and French researcher Axel Souchet published the PoC code for this technique.
One more interesting fact is that Power Loader uses the open source disassembler “Hacker Disassembler Engine” (also known as HDE) for code injection. And the same engine is used by Win32/Gapz in one of the bootkit shellcode modules. This doesn't prove that the developer of Power Loader and Gapz is the same person, but is nevertheless an interesting finding.
We continue our research and will be back soon with more interesting information.
Aleksandr Matrosov, Security Intelligence Team Lead
SHA1 hashes for analyzed samples:
Power Loader v1 (builder) - a189ee99eff919b7bead989c6ca252b656b61137
Power Loader v1 (dropper) - 86f4e140d21c97d5acf9c315ef7cc2d8f11c8c94
Power Loader v2 (dropper) - 7f7017621c13065ebe687f46ea149cd8c582176d



