At the beginning of January 2013, we started tracking the interesting Win32/Redyms trojan family. Redyms is notable for changing search results from popular search engines on infected machines. This Trojan family is mostly spreading in the United States and Canada. It is in these regions that the cybercrime market pays the highest prices for redirection from popular search engines results to malicious ads/links. I’ve already published information about PPI (Pay-Per-Install) programs which distribute malware for BlackHat SEO (Cycbot: Ready to Ride).
Deeper analysis shows that Win32/Redyms has similar code functions and work activity to Win32/Agent.TJO (also known as part of the Olmarik/TDL4 family). Win32/Agent.TJO is a user-mode Trojan program, but based on clicker component functionality found in the TDL4 family (The Evolution of TDL: Conquering x64). TDL4, Win32/Agent.TJO and Win32/Redyms use similar techniques for network traffic manipulation in the active internet browser. So as to intercept and alter the data exchanged over the network the bot hooks several functions from Microsoft Windows Socket Provider (mswsock.dll):
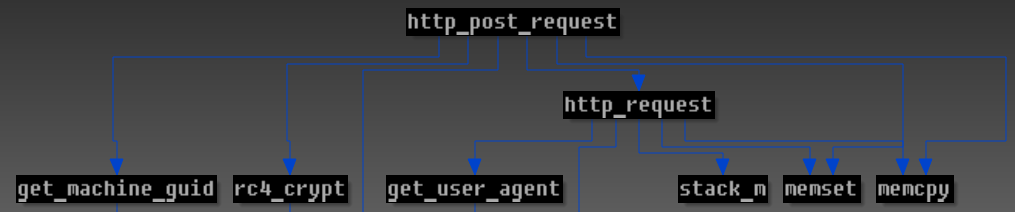
All three malware families use the same hooking technique and a communication protocol encrypted by RC4 stream cipher. The communication routine call graph in Win32/Redyms looks like this:
The next interesting finding in Win32/Redyms is the DGA (Domain Generation Algorithm) used to generate C&C domain names. This DGA is based on simple alphabetical permutations and changes according to the init state constant. Reconstructed algorithms in python and decompiled assembly code are shown in the following figures:
[python code]
[decompiled assembly code]
The list of C&C domain names generated looks like this:
The first domain names from the list were registered in the middle of December 2012 or at the beginning of January 2013. This indicates indirectly that Win32/Redyms was being distributed at the end of December.
Win32/Redyms injects malicious code into all active processes on the infected machine. If activity from the most popular browsers was detected, a malicious thread was injected into the browser process and functions from mswsock.dll were hooked.
The injected code intercepts network activity from the browser process and looks up search engines from the following list:
If search engine activity is detected, all search requests are redirected to the C&C and the URLs shown in the search results will be changed in accordance with the list received from the C&C. The URL checking engine is based on hooking the WSPSend() routine, which uses Adelson-Velsky/Landis (AVL) trees as data structure in order to manage the data. For operating with the AVL trees data structure the malware utilizes the structure RTL_GENERIC_TABLE from kernel32.dll. TDL4 uses the same ideas in the user-mode component cmd.dll.
Aleksandr Matrosov, Security Intelligence Team Lead
SHA1 hashes for analyzed samples:
Win32/Redyms.AB: 07e73ac58bee7bdc26d289bb2697d2588a6b7e64
Win32/Agent.TJO: 3777c3e98e5be549a7c73f6841c759a9f8a098c3