Security researchers at ESET have released their latest research into the notorious Sednit cyberespionage group, which has targeted over 1000 high profile individuals with phishing attacks and zero-day exploits in their attempts to steal confidential information.
The Sednit gang, also known sometimes as APT28, Fancy Bear, Pawn Storm or Sofacy, are highly experienced. It has been engaged in criminal activity since at least 2004 and has developed sophisticated attacks that bypass the typical network security at compromised organizations.
ESET's researchers have been actively investigating the Sednit group's activities for the past two years, and are releasing their findings in three separate pieces of research this month.
In part one, entitled En Route with Sednit: Approaching the Target, ESET's researchers describe the typical targets of the Sednit group, and the usual techniques used to compromise targeted systems.
High-profile publicized examples of past attacks linked to the Sednit group include the US Democratic National Committee (DNC), the German Parliament and the French TV network TV5Monde. The recent high-profile data breach at WADA has also been attributed to Sednit.
However, Sednit's victims do not just end with organizations. ESET has uncovered attacks targeting high-profile figures in Eastern European politics, including Ukrainian leaders, NATO officials and Russian political dissidents.
So, what is notable about the attacks perpetrated by the Sednit group?
Stealing webmail account credentials
A common technique used by the Sednit group when targeting an organization is to attempt to steal users' webmail credentials. Targeted phishing emails, for instance, are sent to targets linking to fake login pages where users are tricked into entering their usernames and passwords.
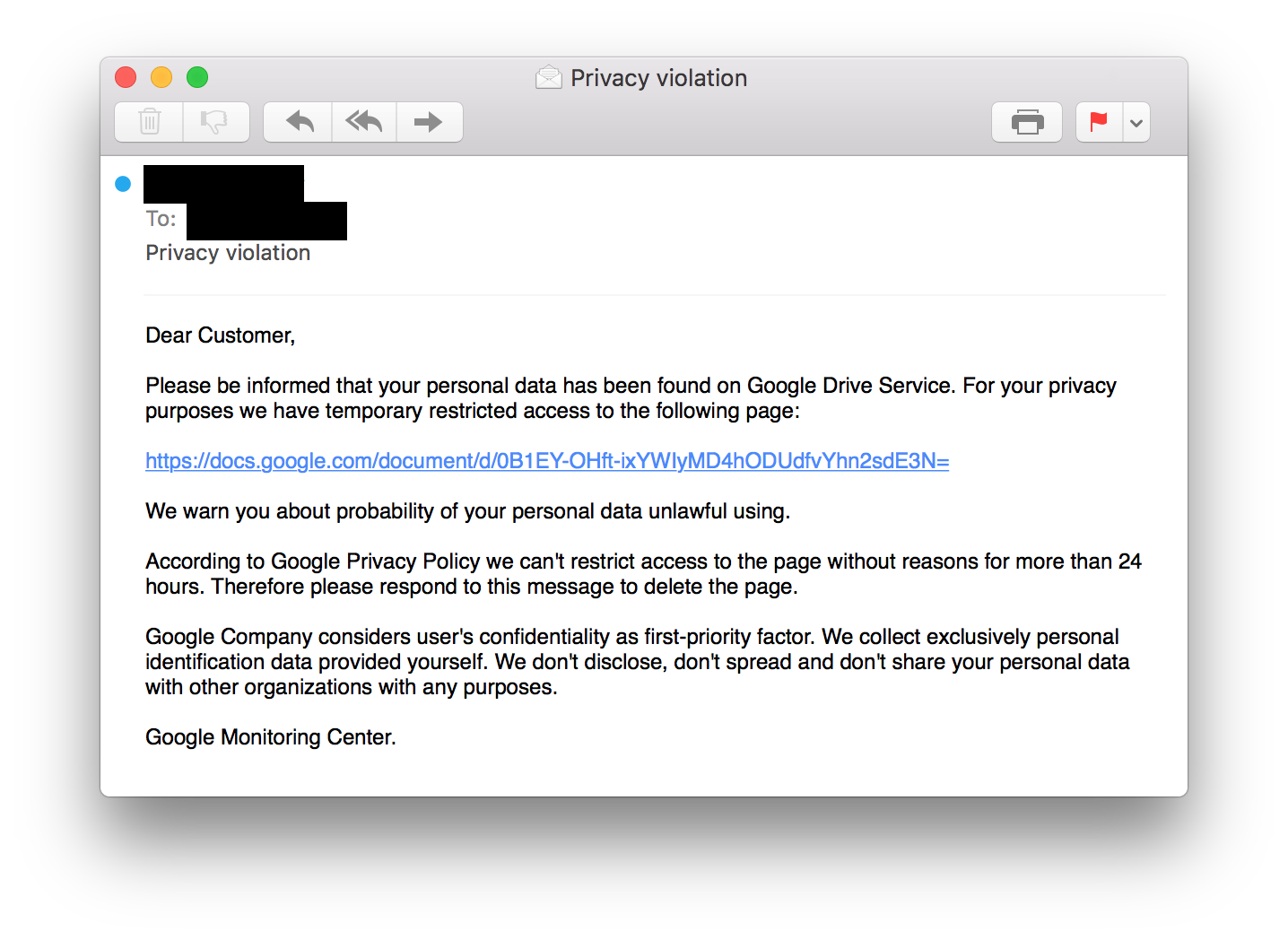
The emails use social engineering techniques to trick users into thinking that they urgently need to act upon the email, in the hope that targeted victims will click on a link in haste without thinking about the possible consequences of their actions.
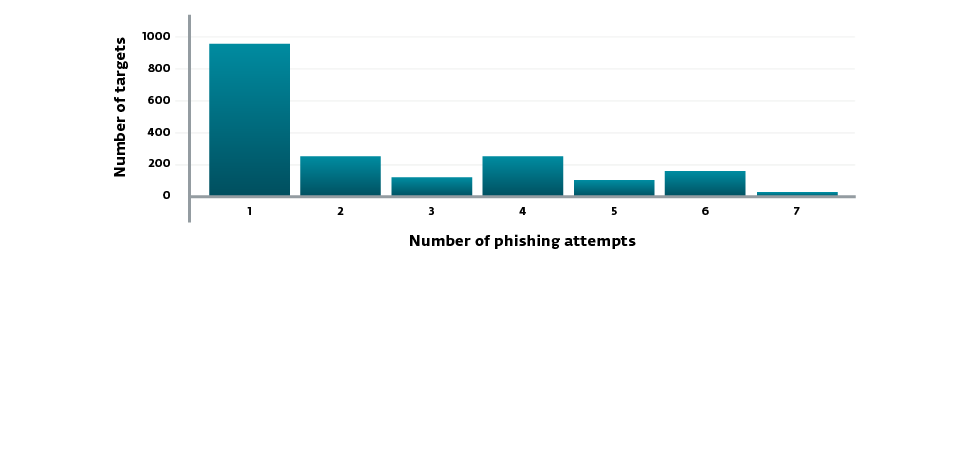
ESET's analysis uncovered at least 1,888 unique email addresses that were targeted between 16 March and 14 September 2015, with most attacks occurring on Mondays or Fridays.
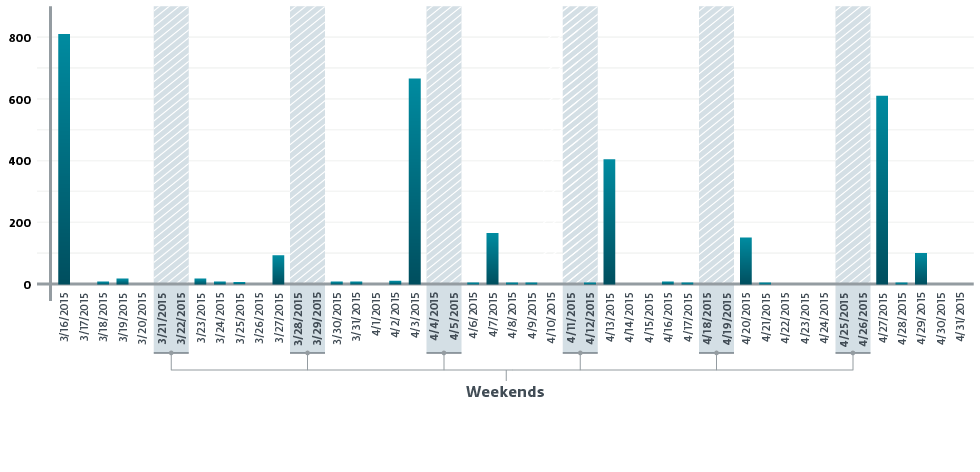
In the paper, ESET's researchers suggest that the regular peaks might correspond to the launch of new phishing campaigns.
Malicious emails
The Sednit gang is not shy of abusing email to infect target's computers - whether it be by attaching a malicious file or linking to a website containing a custom exploit kit.
In the case of malicious email attachment, the group has exploited vulnerabilities in Microsoft Word, Microsoft Excel, Adobe Flash and Adobe Reader.
In the following example, we see a malicious attachment claiming to come from the Ukrainian Academic Union in an email claiming to be about relations between Russia and the EU:
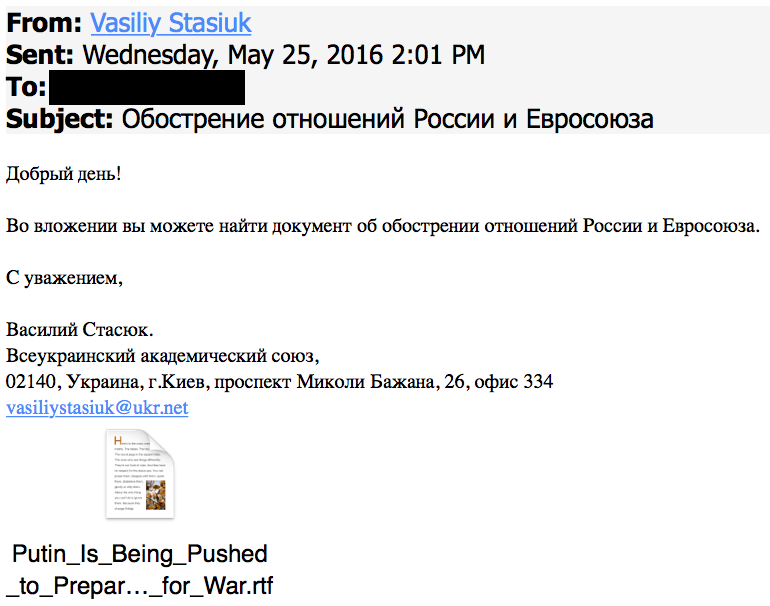
In this particular case, the attached RTF file exploits a vulnerability to drop additional malicious code onto the victim's computer.
In other malware attacks perpetrated by the Sednit group, fake websites hosting malware have been created, luring readers with the headlines of legitimate news articles.
For instance,
- "West’s military advantage is being eroded, report warns"
- "Despite ISIS Attacks, North Korea Remains the `Varsity` of Global Threats"
- "Taking War Seriously: a Russia-NATO Showdown Is No Longer Just Fiction"
- "Russia warns Turkey over Aegean warship incident"
- "Iraq warns of attacks before Paris assault"
Who is being attacked?
Most of the targets uncovered by ESET's research have Gmail addresses, the majority of which belong to individuals.
However, the following organizations that use Gmail were found in the list:
- Embassies belonging to Algeria, Brazil, Colombia, Djibouti, India, Iraq, North Korea, Kyrgyzstan, Lebanon, Myanmar, Pakistan, South Africa, Turkmenistan, United Arab Emirates, Uzbekistan and Zambia.
- Ministries of Defense in Argentina, Bangladesh, South Korea, Turkey and Ukraine.
Furthermore, individual targets included political leaders and heads of police of Ukraine, members of NATO institutions, members of the People’s Freedom Party, Russia's People's Freedom Party, Russian political dissidents, "Shaltay Boltai" -- an anonymous Russian group known to release private emails of Russian politicians -- journalists based in Eastern Europe, academics visiting Russian universities, and Chechen organizations.
Use of zero-day vulnerabilities
Firstly, there is the gang's use of brand new zero-day vulnerabilities - increasing their chances of successful compromise of a target's system with the minimum of user involvement.
As ESET's researchers document, in 2015 alone the group exploited no fewer than six zero-day vulnerabilities in the likes of Windows, Adobe Flash and Java.
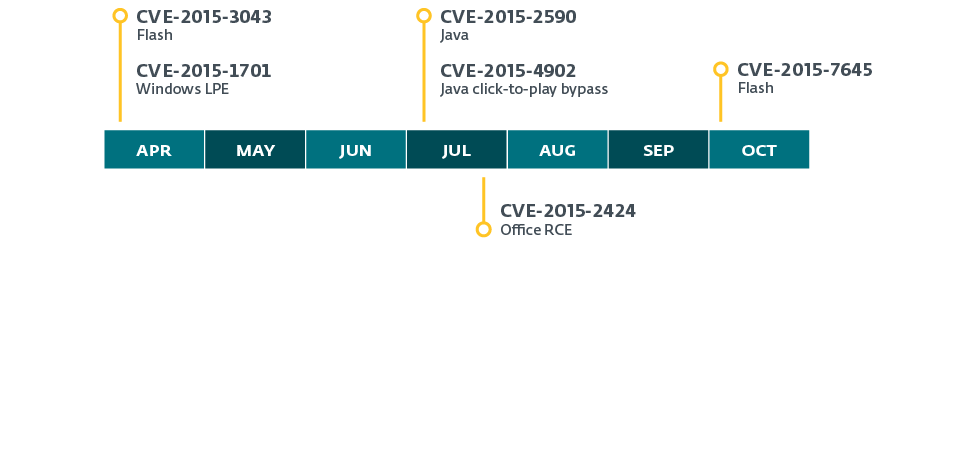
A run-of-the-mill criminal gang would be unlikely to make use of quite so many previously unknown, unpatched vulnerabilities because of the significant skill, time and resources required to properly uncover and exploit them.
Furthermore, as will described in the forthcoming second and third parts of ESET's research into Sednit, the gang created dozens of custom programs, modular backdoors, bootkits, and rootkits to assist them in their spying.
Attribution
The level of sophistication shown by Sednit underlines the common belief that it is a state-sponsored hacking group.
Curiously, the investigation determined the time of day that the attackers appeared to be operating:
"Interestingly, the distribution of the hours matches the working hours from 9AM to 5PM in UTC+3 time zone, with sometimes some activity in the evening."
Some have directly attributed the Sednit group to some Russian entities.
Users would be wise to read the paper and make their own determination about who the likely perpetrators are, and read up on the indicators of compromise that will help them determine if they themselves might have fallen foul of the Sednit group.
For more information, read the paper from ESET’s team: En Route with Sednit: Approaching the Target and check Sednit-related IOCs on ESET’s Github account.
For any inquiries related to the whitepaper, contact its authors at: threatintel@eset.com




