One of the surprises of last year for everyone working in IT security was, without a doubt, the hit TV show Mr. Robot. It is not just that the series tackles current issues, but rather that, to date, it boasts the most faithful representation of the cybersecurity world and of hacking techniques that we have ever seen on television (although we can naturally excuse a little poetic license).
This is why so many of us have been looking forward to the ‘official’ return of Elliot, the conflicted protagonist of Mr. Robot. We say official because, in a great marketing ploy, the TV channel itself screened the first episode of the second season a few days early, making out that it had fallen prey to a live attack from hacktivist group fsociety while showing interviews with the protagonists.
But let’s stop beating around the bush and see what season two, episode one has in store for us. We should note that from here on in we'll be talking about the plot of the episode, so if you haven't already seen it, do not read any further because there will be SPOILERS.
The Internet of Things and everything bad that can happen
One of the most significant things that happens in this episode is when one of the directors of Evil Corp has problems at home when she gets back from the gym. The alarm and the entertainment system, the lights, the air conditioning, and even the thermostat appear to have gone ‘mad’, forcing her to abandon her home because it is impossible to get any rest there.

This provides an opportunity for hacktivist group fsociety, led by Darlene, to occupy the house and convert it into their base of operations. If we move onto analyzing the possibilities of an attack of this type occurring, we’ll see that you have to take into account a number of factors. In the scene itself, we don't see how the attack is carried out, but we can get some kind of idea if we take into account the vulnerabilities of the Internet of Things in relation to smart homes.
Looking back at our chat with investigator Jesús Molina in the BlackHat and Defcon editions in 2014, he stayed at a hotel where a lot of the features available in his room were controlled by an iPad.
In Mr. Robot, the victim also uses a tablet and a touchscreen located in the receiver at her apartment to control various smart home features. Investigations carried out on the Internet of Things lead us to believe that the attack was performed by taking advantage of a Wi-Fi connection used by these devices to connect to the control panels.
In the event that an attacker gains access to the Wi-Fi in this apartment and identifies the home automation system used, or simply the devices that are connected, the attacker could seek out vulnerabilities in these devices and take advantage of them. This theory doesn't seem so absurd if we take into account the fact that many manufacturers of this type of device do not include any form of security and they remain vulnerable throughout their service life.
Ransomware comes into play
As Mr. Robot is a series that touches on topical themes, it was inevitable that ransomware would come along at some point. The first episode of this second season sees Darlene prepare an attack using a Cryptowall variant. To do this, she uses the SET (Social-Engineer Toolkit) which is included in Kali Linux.
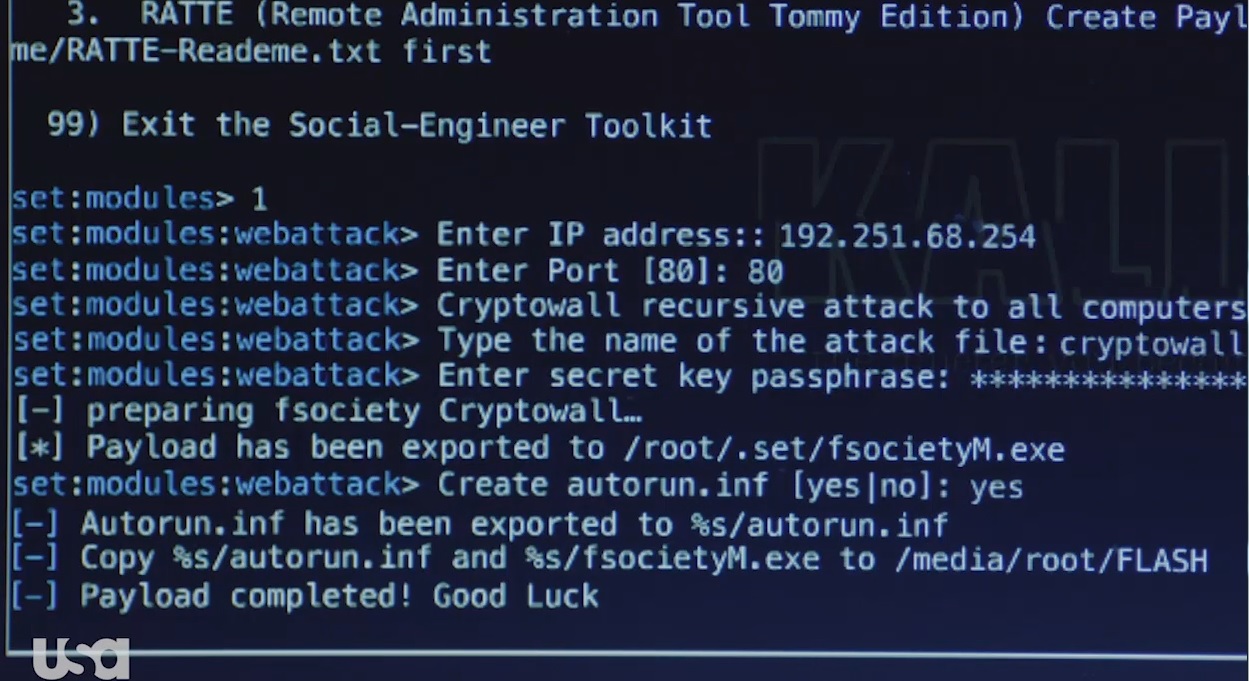
Looking at the entire attack preparation sequence, we see how she first prepares the payload that will execute the fsocietyM.exe file in the target system. This file contains the Cryptowall ransomware, one of which caused the most damage during 2015 in the US and other regions, and which is also prepared to spread itself over a network to affect all possible systems.
The plan of attack, even before we get to the next scene, is to execute this ransomware, with Darlene using the old trick of preparing an autorun.inf file enabling her to run any file she wants automatically through introducing extractable media—in this case a USB memory stick.
We find it rather strange that Darlene chose this technique, given that more modern versions of Windows have the option to deactivate autorun. However, she could be very familiar with the Evil Corp infrastructure she wants to attack, and knows that this option is still activated. In the real world, this type of ransomware is spread via email or through compromised websites, or prepared by attackers to execute malicious code, taking advantage of the vulnerabilities of users who visit such websites, and automating the process through exploit kits.
The next scene shows us Darlene providing another member of fsociety with the pen-drive set up to perform the infection. A little later, we see this person gain access to the system controlling the Evil Corp bank, showing that an attack via a USB memory stick is a real possibility.
The result can be seen a few minutes later, when an Evil Corp employee is serving a client. When they go to view something on the system, they see a lockscreen that should be familiar to anyone who has seen a ransomware infection before.

This screen shows a message stating that the files have been encrypted, and a ransom demanded. Unlike in real life (for various reasons), the ransom is a very large amount of money ($5.9 million) and has to be handed over in person at a specific place and at a specific time.
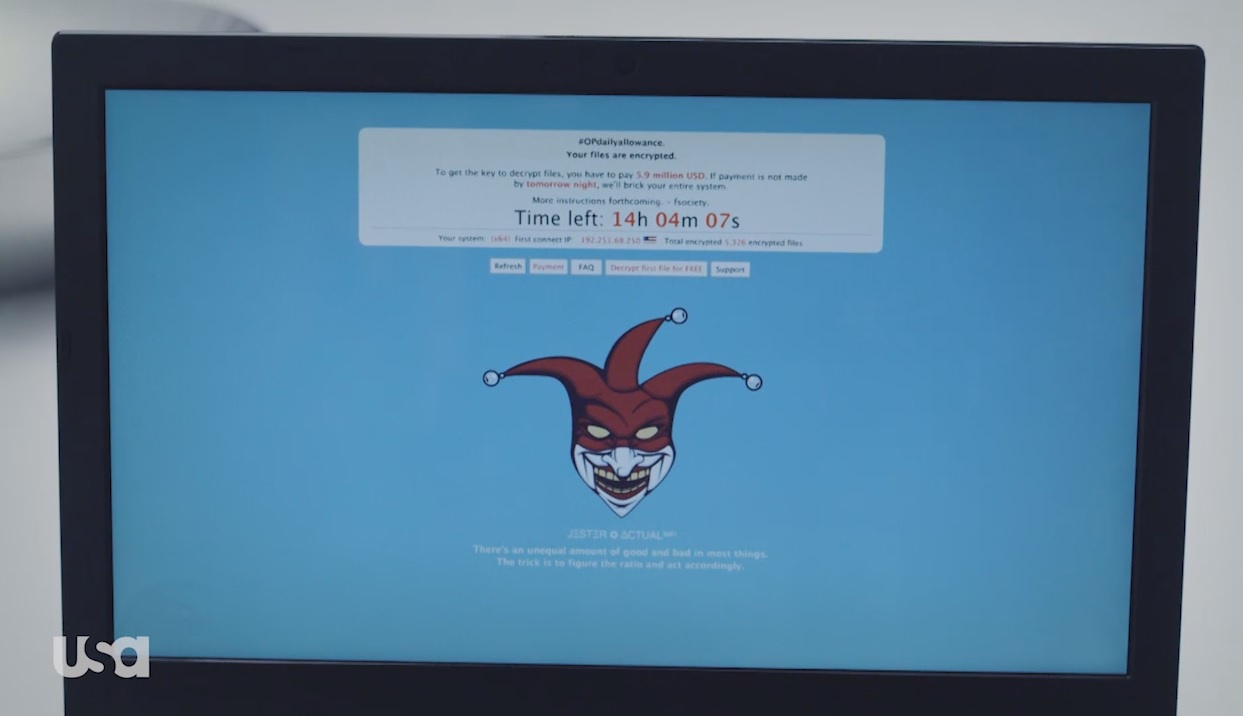
If it had been one of the ransomware types that we deal with on a daily basis, the usual thing would have been to demand a much smaller ransom to be paid in bitcoins according to the instructions stated on a website hosted on Tor but, it bears repeating, this is a fictional series and there are significant reasons for changing this behavior.
It is possible to take steps to combat ransomware in the real world, especially in a corporate setting. Prevention is something that must be considered and, to make users more aware of the issue, advice, several guides, and infographics are available that we can use as a starting point to prepare our defense strategy against this and other threats.
Conclusion
The first season of Mr. Robot was a revelation and provided a perfect example of how to talk about cyberattacks and their consequences without falling into the temptation of writing meaningless commands on futuristic interfaces that would serve no purpose at all. This second season has started off where the first left off.
We should not forget that hacking is just one way for people to reach an objective. Their own personal motivations and those of fsociety are many and varied. It would be very boring to make a series that just showed the daily working life of those of us who work in cybersecurity. Mr. Robot has been able to make a solid argument with current themes, using real attack tools to attract a general audience. We hope the show runs for a long time.
Image credits: ®USA Network




