Many malicious developers try to trick users into downloading their apps by creating the illusion of a useful application. They accomplish it by creating a very interesting app name and adding a bogus description that does not match the functionality of the application.
ESET has discovered eight fake applications on Google Play that (falsely) promise to boost the number of followers on users’ social network profiles. Our security software is detecting these as Android/Fasurke.
Available on the Google Play store for more than four months, these apps have gathered 250,000 – 1,000,000 downloads in total. Upon ESET’s notification, the Android security team removed all of these fakes from the Google Play store.
Even though these apps no longer pose a risk to Android users, it’s worth disclosing exactly how they worked, as sooner or later, similar malicious apps will likely appear on the market again and use the same techniques to dupe more users.

Figure 1: These applications were removed from Google Play on ESET’s notice
How did they work?
These eight fake applications mainly promised more followers, friends or views on social networking apps, but their true purpose is quite different – namely to lure the users into paying perpetual subscriptions, sharing their personal information, consenting to receiving marketing messages or the display of ads.
After launching the app, users were requested to enter their mobile device model, username and the number of followers they wished to gain. So, it's 500,000 new followers with just one click of a button, right? Wrong. After pressing the button “Start Generating”, the users were presented with another step called “human verification”.
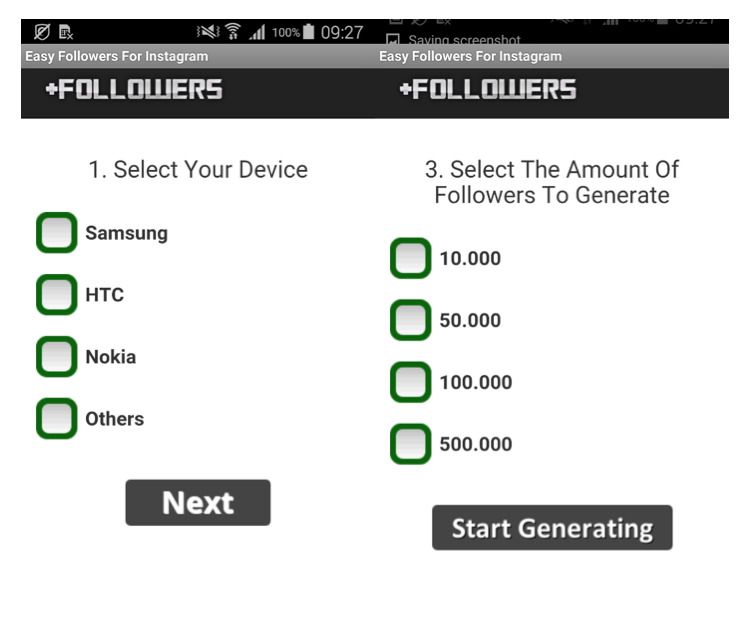
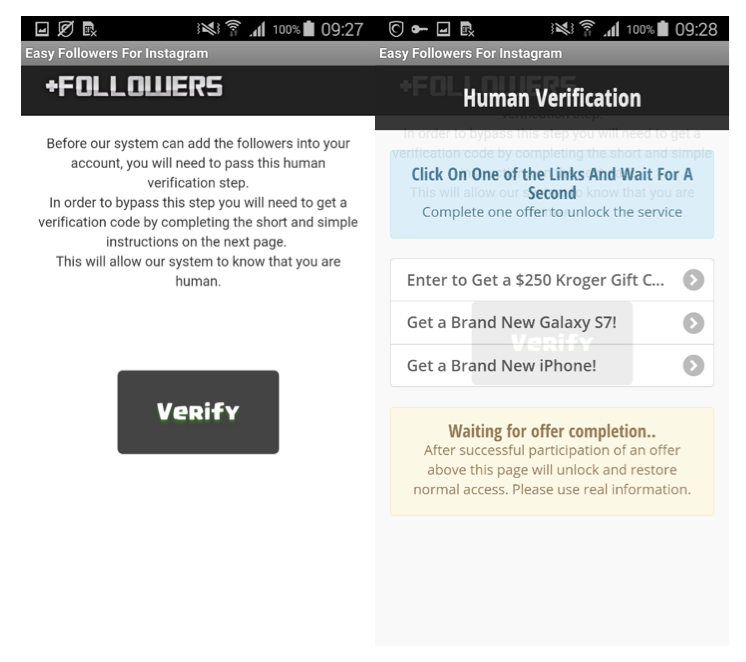
Figure 2: Application example
However, this “verification” was only a cover-up used to draw the victim into an endless set of offerings of gifts, coupons and free services, as well as to request their personal information including name, email, address, telephone, date of birth, and gender. Users were also asked to consent to receiving telesales calls and text messages, some of which were premium-rated SMS subscriptions costing approximately 4.8 EUR per week.
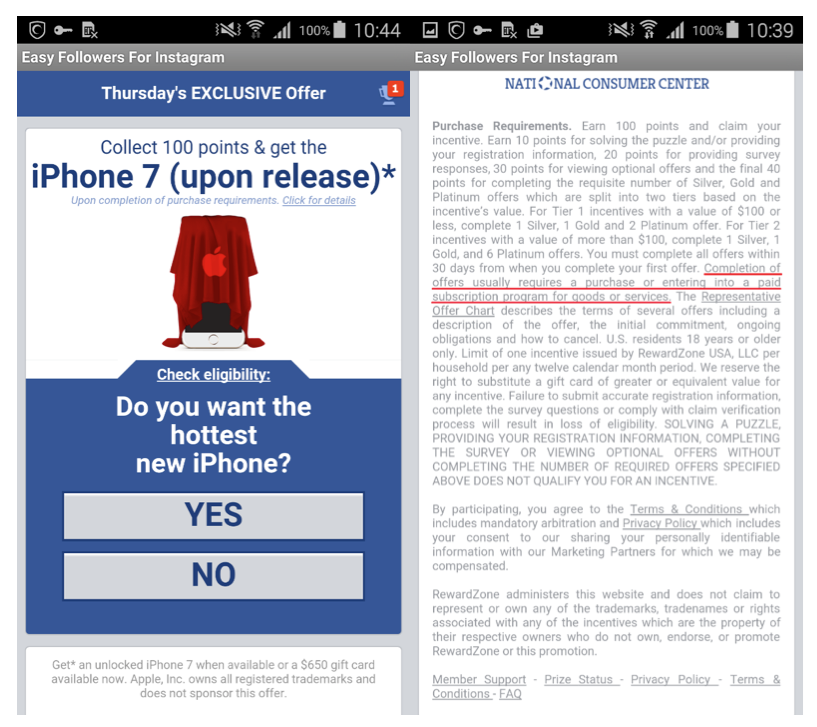
Figure 3: One of the offers that lure the user into a paid subscription
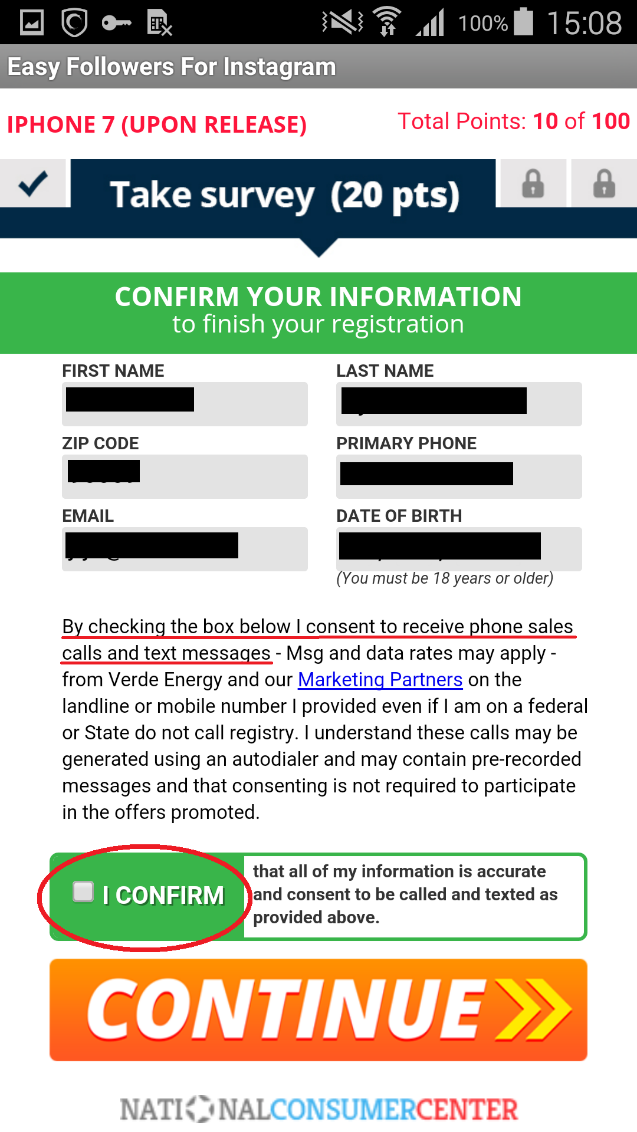
Figure 4: Example of an offer that lures the user into consenting to receiving marketing communication
In fact, this “verification step” is an endless spiral. The only purpose of all those surveys, ads, offers, rewards, prizes, gift coupons and other cheap marketing tricks is to milk as much information and money from “follower-hungry” users as possible.
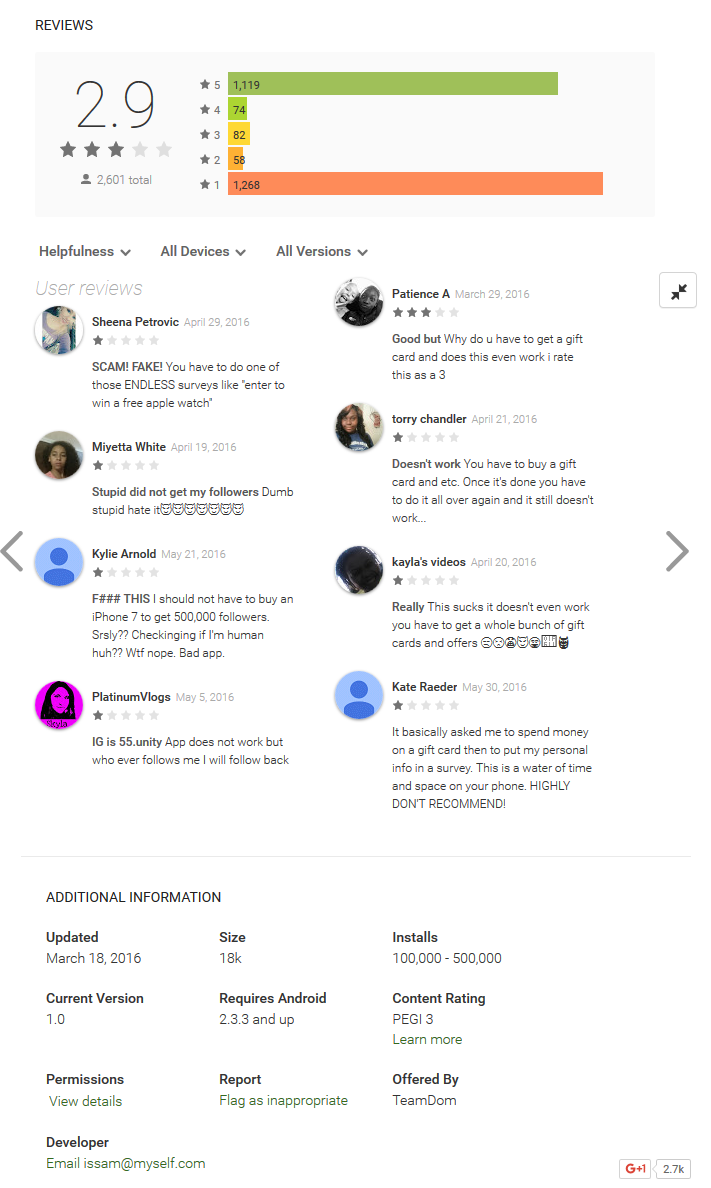
Figure 5: Example of one of the bogus app reviews
All the bogus apps had a high proportion of low ratings and many extremely negative comments. Despite that, they reached hundreds of thousands of installations.
Conclusion
The bogus apps that ESET discovered at Google Play promised something they could not deliver – namely a boost in the number of followers on the victim’s social network profile. Instead, they brought users an endless set of subsequent offers, each of them simply being the next opportunity to trick users into sharing their personal information, consenting to marketing activities or even subscribing to a premium-rate SMS. Apps seen by ESET were removed from the Google Play app store, but users should continue to follow security best practice as similar apps may appear on Google Play again.
ESET recommendations in connection with malicious Android apps:
- If possible, stick with Google Play or other reputable app stores. These markets might not be completely free from malicious apps but you have a fair chance of avoiding them.
- Prior to installing any app, check its ratings and reviews. Focus on the negative ones, as they often come from legitimate users while positive feedback may be crafted by the attackers.
- Facing sensational offers, keep in mind the golden rule: "If it seems too good to be true, it probably is." If they offer you half a million followers for free, with a single click - or after completing a survey - they will probably not be able to deliver.
- Think twice when entering your personal information, giving consent to something or ordering goods or services. Be sure absolutely sure about what you receive in exchange.
- Invest a small amount of effort in getting to know who you are about to do business with.
- Use a quality and reputable mobile security solution to protect your device.




