Not even a week has passed since ESET warned users worldwide about an active Ray-Ban scam campaign on Facebook, which tricks users into sending their payment card details to the attackers. Today we bring you information on yet another malicious activity targeting the world’s largest social network.
This time, malicious links are disguised as a post on a timeline you were tagged in, or as a message sent to you via Messenger by a friend. Using one of the titles “My first video”, “My video”, “Private video” or a string of randomly generated characters, it tags various people from a victim’s friend list and lures them into clicking on it.
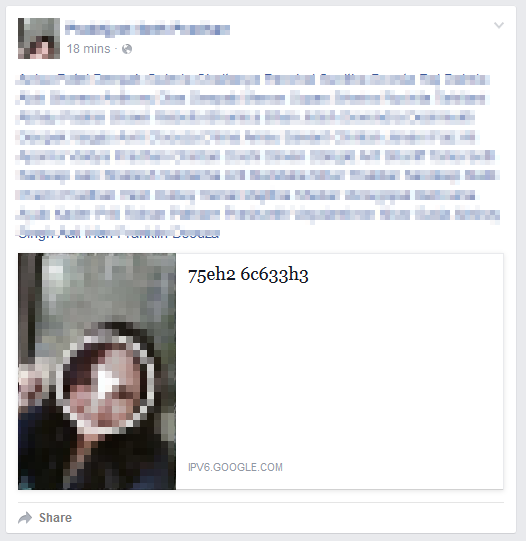
Figure 1 - Malicious video link with tagged friends
If an unsuspecting user falls for the scam, the post redirects him/her to a fake YouTube website. After what pretends to be an unsuccessful attempt to load the content, he/she is requested to install an additional extension using the following message:
Sorry, if you don't install Video Play plugin, you will not be able to watch the video!
Click 'Add Extension' to watch the video
If the victim installs the malicious plug-in, his/her browser becomes infected and carries the infiltration further. As described above, his/her Facebook wall becomes flooded with fake video posts tagging multiple friends from the victim’s friend list and, subsequently, all online friends will receive an identical message via Messenger with the same harmful contents.
ESET detects this threat as JS/Kilim.SO and JS/Kilim.RG. At this point, the infiltration only targets Chrome users, but there is no guarantee that it will not spread to other browsers in the future.
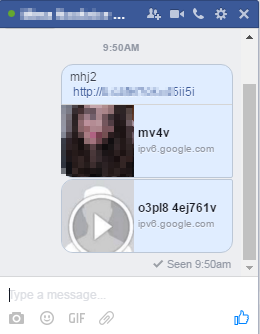
Figure 2 - Malicious video links sent to friends
How does it work?
After clicking on “Add Extension” at the fake YouTube site, malicious code installs a trojan plug-in (containing malicious Java Script code) into the Chrome browser. This is disguised as a legitimate “Make a GIF” plug-in, but comes from a different developer - namely “freechatfor.org”.
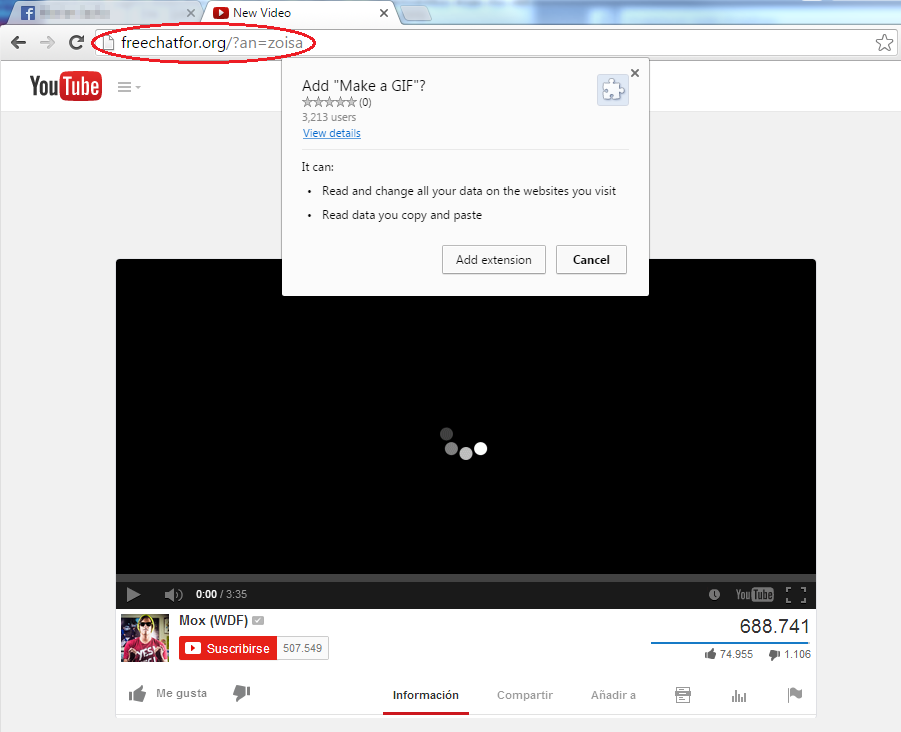
Figure 3 - Video link redirection
The infected version of the app comes with an additional malicious functionality, allowing it to infect Facebook accounts and spread immediately after installation. Yet, the scale of its capabilities is wider than just that.
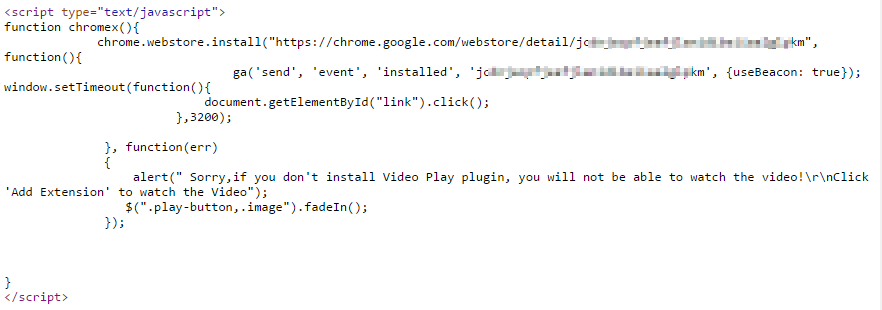
Figure 4 - Request to install Chrome extension
This trojan can add friends, create Facebook pages, share, edit or hide posts, or unfollow them. At the time of writing, these functions are not yet active, but we cannot rule out that this won’t happen in the future.
Do people fall for it?
Yes. Just last week, ESET detected this threat more than 10,000 times. The scam spreads malicious code and infects Facebook users in the US, Canada, Australia, the UK, New Zealand, Russia, Slovakia, the Czech Republic, Germany, Switzerland, Poland, India, Dubai, Singapore, Norway, Greece, Hungary, the Republic of the Philippines, Turkey, Israel, Peru, Thailand, Argentina and many other regions.
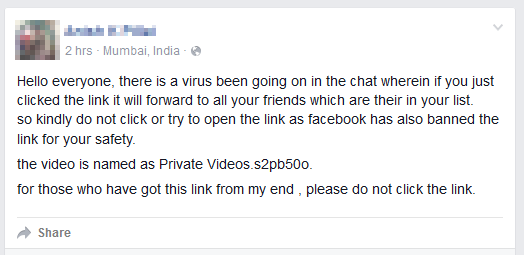
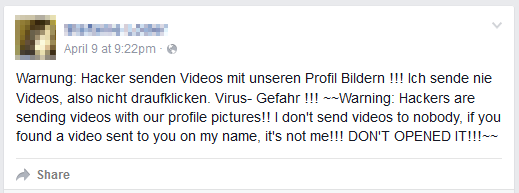
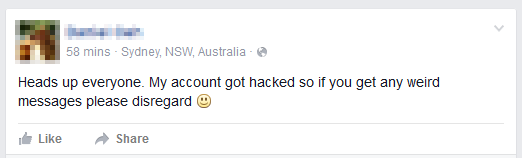
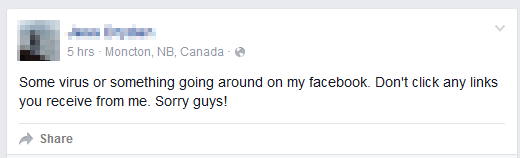 Figure 5 - Some of the victims’ reactions
Figure 5 - Some of the victims’ reactions
How to get rid of it?
1) Immediately remove “Make a GIF” extension from your Chrome browser.
Either type “chrome://extensions/” into the address bar or go to Customize and control Google Chrome -> More tools -> Extensions -> Make a GIF -> Remove from Chrome …
If you also use the legitimate “Make a GIF” extension, use the pictures below to distinguish the original version from the infected one.
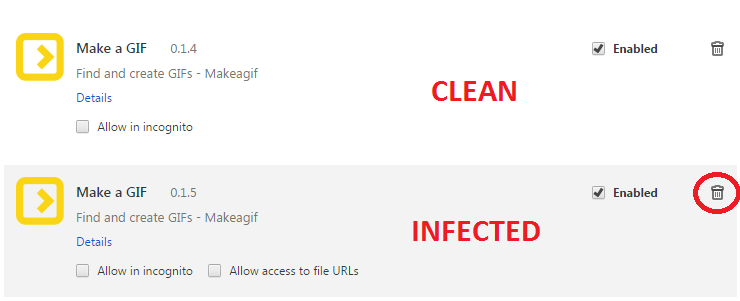
Figure 6 - Infected and not infected extension
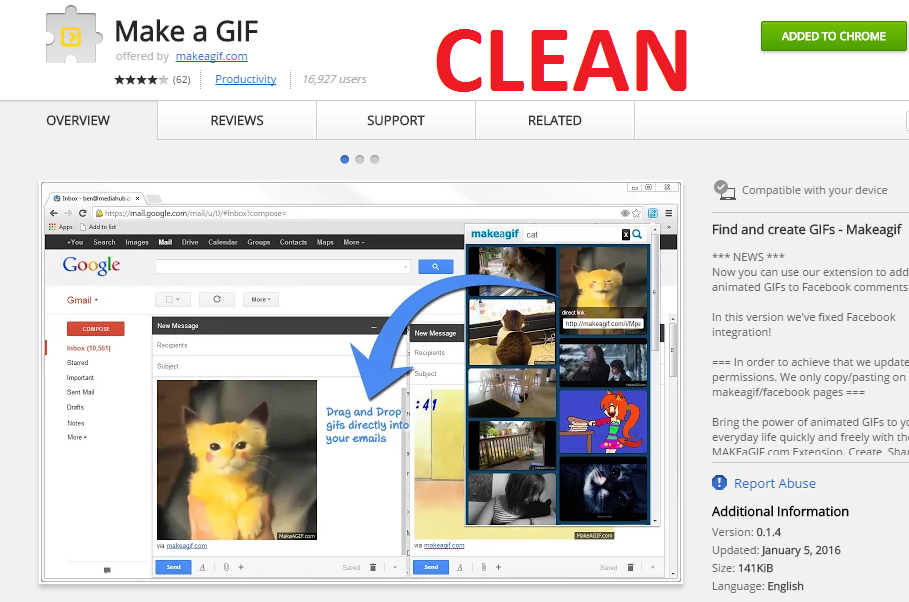
Figure 7 - Clean variant of Make a GIF
If you click on Details -> View in store, you will see details about extension.
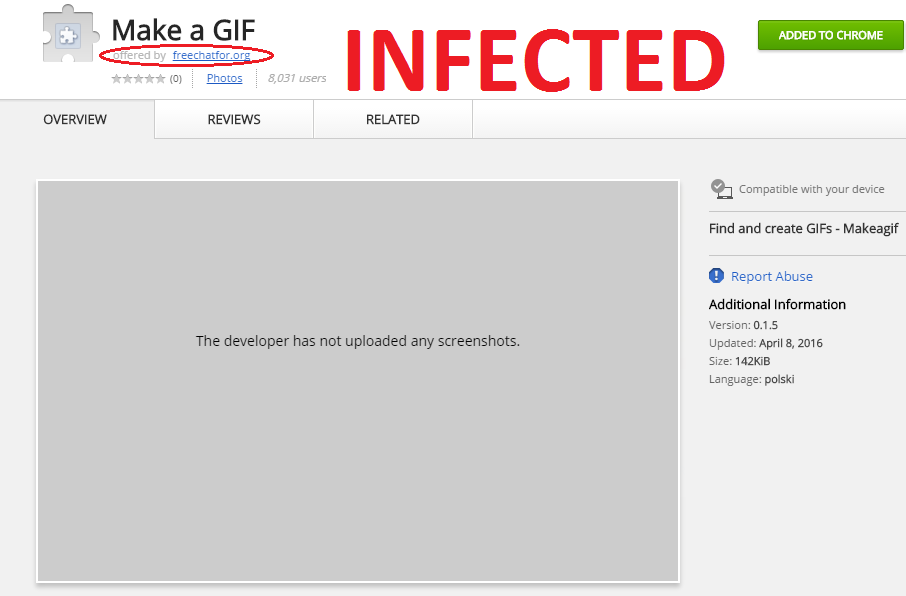
Figure 8 - Infected Make a GIF
2) Scan your computer with a reliable antivirus software. If you don’t have any security software installed on your personal computer, you can use our free solution ESET Online Scanner.
Consequences
At this very moment, the malicious campaign is spreading spam messages and infecting Facebook accounts with a very high rate of success. However, it has potential to become more dangerous in the future, spreading other, more powerful malware with new capabilities.
Therefore, we advise users to be very careful when clicking on any links that appear suspicious (using different or imperfect language, tagging friends for no reason, originating from an unexpected friend or other unknown source, etc), and while attempting to watch YouTube videos do not download any additional Flash player or similar plugins.