ESET researchers have found 343 malicious porn clicker trojans, which ESET detects as Android/Clicker, on Google Play over the last seven months – and their numbers keep rising. In one of the largest malware campaigns on the Google Play Store yet, criminals continue to upload further variants of these malicious apps to the official app store for the Android mobile platform.
“There have been many malware campaigns on Google Play, but none of the others have lasted so long or achieved such huge numbers of successful infiltrations,” explains Lukáš Štefanko, a malware researcher at ESET, who specializes in Android malware.
"There have been many malware campaigns on Google Play, but none of the others have lasted so long or achieved such huge numbers of successful infiltrations."
On average, ten new porn clickers a week bypassed Google’s security checks during this campaign. These porn clickers not only made it into the store, but they also successfully compromised user devices. To get a sense of the scale, porn clickers on Google Play have on average, been downloaded 3600 times each.
Porn clickers are nothing new; the current family has threatened Google Play users since February 3rd, 2015, and ESET researchers continue to follow them closely, having warned about them in the past (see related articles on We Live Security from May 2015 and July 2015).
Unsurprisingly, the creators of these trojans ride the wave of interest in popular applications, notably in games. After installation, they generate fake clicks on advertisements to generate revenue for their operators, robbing advertisers and harming advertising platforms. From the user’s point of view, these trojans generate a lot of internet traffic, which might have negative consequences for users on metered data plans.
Weak mechanisms, negligent users
Considering how widespread porn clickers are on the Google Play Store, it is clear that neither the Google Bouncer filter, nor Google’s human review process can keep malicious apps completely out of the store.
“If an application has more negative comments than positive, it should be a warning for users to reconsider their interest in that app."
“These trojans have been repackaged repeatedly. Newer versions are always slightly modified and have their code obfuscated to hide their true purpose,” comments Mr. Štefanko.
Also, Google’s ‘Verify apps’ setting, which blocks installation of apps that may cause harm often fails to provide protection: this system often only detects malicious apps after they have been removed from the Play Store.
However, Google provides its customers with another tool for protection from bad apps: the review system. In the case of porn clickers, this security system works well: these fake apps typically have very poor ratings so users have a fair chance of avoiding them. Unfortunately, the huge numbers of downloads show many users often don’t care about ratings.
“If an application has more negative comments than positive, it should be a warning for users to reconsider their interest in that app," explains Mr.Štefanko. "In any case, we advise all users to have up-to-date security solutions. A good security product should stop this threat from installing on the device.”
Details about the porn clicker campaign, including Google Play data, hashes and remote servers can be found in the malware researcher's analysis. The expert has also taken time out of his busy schedule to sit down with We Live Security for a detailed chat.
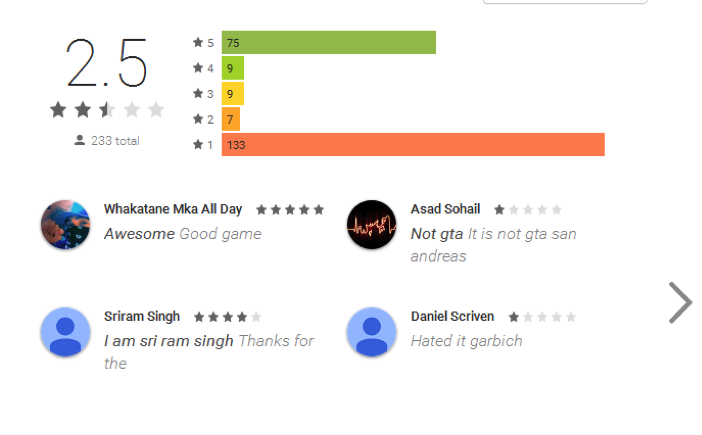
Picture: Users often download fake apps despite of their negative ratings.
Tell us your experience:
[socialpoll id="2336419"]





