Ransomware is a growing problem for users of mobile devices. Lock-screen types and file-encrypting “crypto-ransomware”, both of which have been causing major financial and data losses for many years, have made their way to the Android platform. ESET has prepared a topical white paper on the growth of this insidious Android malware.
Like other types of Android malware – SMS trojans, for example – ransomware threats have been evolving over the past few years and malware writers have been adopting many of the same techniques that have proven to be effective in regular desktop malware.
Both on Windows and on Android, lock-screens are nowadays usually of the “police ransomware” kind, trying to scare the victims into paying up after (falsely) accusing them of harvesting illegal content on their devices. Likewise, as with the infamous Windows Cryptolocker ransomware family, crypto-ransomware on Android started using strong cryptography, which meant that affected users had no practical way of regaining the hijacked files. And because everyday data, such as photos, for example, are now kept on smartphones rather than PCs by so many people, the threat of losing this data is now greater than ever.
One interesting observation that we have made is that the attackers’ center of focus is no longer only Eastern European countries. A number of recent families, such as Android/Simplocker and Android/Lockerpin, for example, have been targeting victims mostly in the USA.
Types of Android ransomware
Ransomware, as the name suggests, is any type of malware that demands a sum of money from the infected user while promising to “release” a hijacked resource in exchange. There are two general categories of malware that fall under the ‘ransomware’ label:
- Lock-screen ransomware
- Crypto-ransomware
In lock-screen types of ransomware, the hijacked resource is access to the compromised system. In file-encrypting “crypto-ransomware” that hijacked resource is the user’s files.
Both types have been a very prevalent problem on the Windows platform since 2013, when ransomware started to increase in popularity among cybercriminals, even though it had been around for many years before. Ransomware infections have been causing trouble both to individuals and to businesses.
Since one of the most noticeable trends in regard to Android malware is that malware writers have been bringing to this platform malware techniques that have proven to be successful on Windows, the appearance of ransomware on the most popular mobile platform was logical and anticipated. As we can see on the trendline graph, detections of Android ransomware are growing.
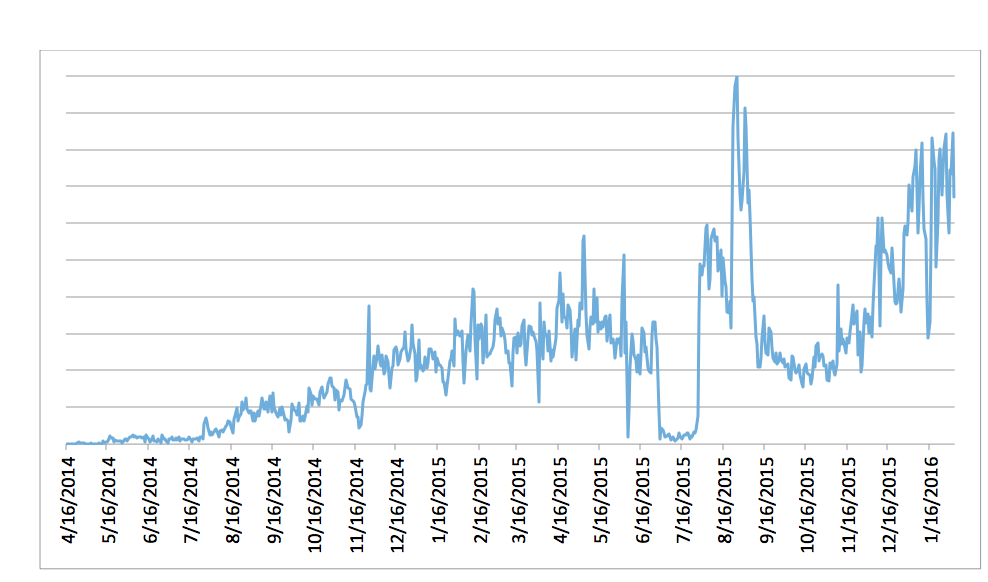
Android ransomware detection statistics, according to ESET LiveGrid®
With consumers switching more and more from PCs to mobile, more and more valuable data are being stored on these devices that devices, which leads to the fact that more and more valuable data is being stored on those devices that all of us carry around, Android ransomware is becoming ever more worthwhile for attackers.
How to keep safe
For users of Android devices it’s important to be aware of ransomware threats and to take preventive measures. Among the most important active measures to take are avoiding unofficial app stores and having a mobile security app installed and kept up to date. Additionally, it is important to have a functional backup of all of important data from the device.
Chances are that users who take appropriate measures against ransomware will never face any request for ransom. And even if they fall victim and – worst case scenario - see their data encrypted, having a backup turns such an experience into nothing more than a nuisance.
If users do manage to get infected by ransomware, they have several options for its removal, depending on the specific malware variant.
For most simple lock-screen ransomware families, booting the device into Safe Mode – so third-party applications (including the malware) will not load – will do the trick and the user can easily uninstall the malicious application. The steps for booting into Safe Mode can vary on different device models. (Consult your manual, or ask Google – the search engine.) In the event that the application has been granted Device Administrator privileges, these must first be revoked from the settings menu before the app can be uninstalled.
If ransomware with Device Administrator rights has locked the device using Android’s built-in PIN or password screen lock functionality, the situation gets more complicated. It should be possible to reset the lock using Google’s Android Device Manager or an alternate MDM solution. Rooted Android phones have even more options. A factory reset, which will delete all data on the device, can be used as the last resort in case no MDM solutions are available.
If files on the device have been encrypted by crypto-ransomware such as Android/Simplocker, we advise users to contact their security provider’s technical support. Depending on the specific ransomware variant, decrypting the files may or may not be possible.
We advise affected users against paying the requested ransom, for several reasons. While it is true that some established Windows crypto-ransomware gangs have reached the level of professionalism where users will usually get their files decrypted, that is not always the case. File-encrypting crypto-ransomware is extremely popular among malware writers and there are many different families of Windows Filecoders (the ESET detection name for the category). Many of them have jumped on to the ransomware bandwagon, hoping to copy the success of Cryptolocker and the like, but our technical analyses of all those families has shown that many of them are implemented poorly. For users, this means two things: Firstly, that even if they do pay up, their files may not get decrypted. Secondly, that it may be possible to decrypt their files without paying.
As far as ransomware on Android is concerned, we have seen several variants where the code for decrypting files or uninstalling the lock-screen was missing altogether, so paying would not have solved anything.
At the level of a single user or a business being a victim of crypto-ransomware and facing a loss of data, it boils down to a question of trust. Can the cybercriminals be trusted to keep their end of the bargain and decrypt the files after the ransom has been paid? Obviously, there are no guarantees. And even if the files are decrypted, there’s nothing stopping attackers (the same ones or others) from coming back for more.
Taking the wider view of the whole ransomware economy, giving in to the attackers’ demands only fuels the problem.
As mentioned above, prevention by adhering to basic security principles, using updated security software on Android, and backing up your data (not only on the device itself) is a much more sensible option. And with all of those precautions being readily available and easy to use, there really is no reason not to do so.
For detailed description of various types of Android ransomware, attack vectors and technical details, read ESET white paper The Rise of Android Ransomware.
This topic will be up for discussion of ESET at the Mobile World Congress. ESET will be located in Hall 5, Booth B05. The largest expo for the mobile industry starts on February 22 in Barcelona, Spain. For more information about ESET at the Mobile World Congress, check our special page.