Updated 3rd April, 2016: Independent security analyst Graham Cluley reported in February that Google had released its latest security update for Nexus devices running Android, adding that one of the most serious flaws found could result in remote code execution: "For instance, the bug in Mediaserver could mean that simply opening an email, browsing a website or receiving a media file via MMS could [result in] malicious code being run on your device. If this sounds familiar then chances are you remember Stagefright, one of the biggest Android security scares of last year."
Updated October 5th: It has been reported that Google, in partnership with manufacturers and carriers, will release a patch today to resolve newly identified vulnerabilities, after Zimperium Lab revealed last week that a sequel to Stagefright had been found. The bug could now compromise as many as a billion Android users.
In a blog, Zimperium Lab stated: "The first vulnerability (in libutils) impacts almost every Android device since version 1.0 released in 2008. We found methods to trigger that vulnerability in devices running version 5.0 and up using the second vulnerability (in libstagefright). Google assigned CVE-2015-6602 to vulnerability in libutils. We plan to share CVE information for the second vulnerability as soon as it is available."
Updated September 10th: An exploit is made available by Zimperium Labs for testing purposes. The python script creates an MP4 that exploits the CVE-2015-1538 vulnerability, one of the most critical flaws of Stagefright. However, according to the author, this isn't a generic exploit as it has only been tested on one device: Nexus running Android 4.0.4.
Updated August 18th: In order to make it even more easier for you to detect whether your Android device is vulnerable or not to Stagefright, we have launched an app that you can download directly from Google Play. Although no new announcements have been provided by Google to confirm when a new patch will be rolled out, it is anticipated that this will take place in September.
Also, it is worth noting Trend Micro published an article on 17th August about a MediaServer flaw, another vulnerability in Android that does not presently appear to be related to Stagefright. However, this has since been fixed by Google via its Android Open Source Project (AOSP).
One week before Black Hat and DEF CON, security researcher Joshua Drake published his findings about a vulnerability in the heart of Android that could allow attackers to steal information from Android devices through remotely executed code via a maliciously crafted MMS. According to the Zimperium zLabs researcher, up to 950 million devices could be vulnerable.
Since this was dubbed one of the biggest vulnerabilities ever, we’re summing up a quick FAQ about it in order to better understand this vulnerability, as well as highlight how you can find out if your Android device is vulnerable.
Is it really the worst of all Android vulnerabilities?
It is difficult to label a vulnerability as being the worst, because the basis for this attribution varies.For instance, factors including the number of devices affected, ease of compromising and the number of exploits in the wild, all of these have varying influences on the severity of a vulnerability. However, with 950 million users of Android devices potentially affected and after one failed attempted by Google to fix it, we should take this a bit more seriously than other, more commonplace vulnerabilities.
How does this vulnerability work and why is it called Stagefright?
Among the thousands of lines in the source code of Android, there is a media library called Stagefright that is in charge of managing multimedia formats that allow you to playback videos and music on your Android devices. An attacker could exploit this vulnerability by crafting a MMS with an exploit and send it to the victim. In this case, this could be a targeted attack based uniquely on the victim’s telephone number, which is the only information needed to send the crafted MMS. It depends on what application you use to visualize the MMS, as with regular Messenger the exploit will be executed only after seeing the MMS without playing the media. Using Hangouts could be even worse, since the device would be compromised almost automatically even before you are able to see the notification.
What versions are vulnerable?
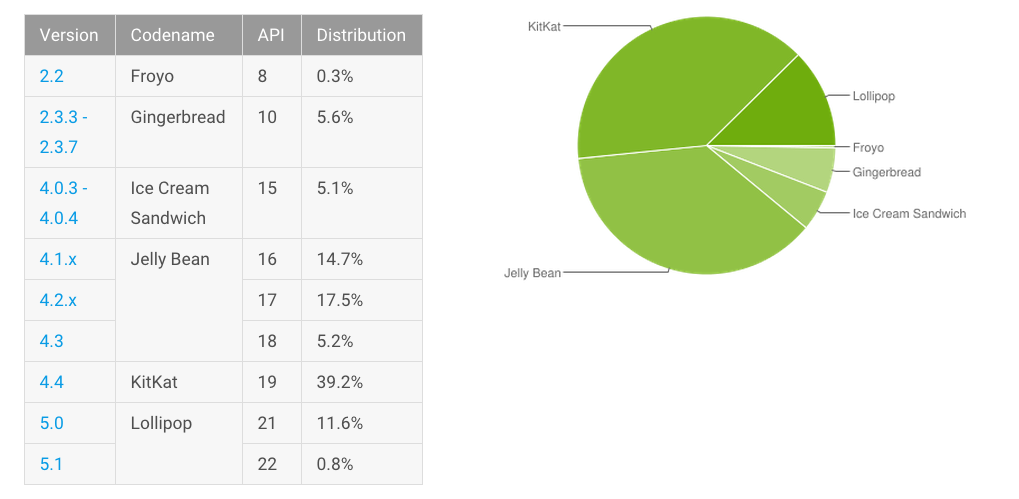
According to the investigation, all versions from Froyo (2.2) inclusive are vulnerable, which means 95 per cent of Android devices – or about 950 million users worldwide. In addition, versions prior to Jelly Bean are at higher risk, since they do not incorporate appropriate mitigations.
Additionally, keep in mind that Stagefright is actually composed of seven different vulnerabilities (plus one more reported on the first attempt to patch) that have been reported at this time. Google already released a first patch but researchers from Exodus already found a bug within the patch. This week Google released another patch to mitigate the vulnerabilities and confirmed that Nexus 4, 5, 6, 7, 9, 10 and Player will receive the new monthly security update in September.
However, there is a major problem with this - who will, for example, receive these patches? Users of devices such as the smartphone Nexus 6 can be sure that this update will be published as Google confirmed. The point is that other vendors may launch the patch only for their latest devices, but still leave most users without patches because neither vendors nor the operators are going to bother to release this update for devices considered obsolete.
Is your Android still vulnerable? Here's what you can do
We recommend you to check with your vendor whether you already have a patch for your Android device. However, as we have seen this past week, even the patch could contain an additional bug. Therefore, we suggest you to check whether your device is vulnerable with the ESET Stagefright Detector App, stay alert for new information and if necessary request updates from your vendor to fix this issue.
Finally, we also recommend you to deactivate auto retrieve either under Advanced Settings in case of using Messenger or in Settings / SMS / Auto retrieve in case of Hangouts.
Image credits: © Kham Tram / flickr




