Hackers, supportive of the Assad regime in Syria, have successfully compromised content displayed on the US Army's website, popping up messages to visitors:
"Your commanders admit they are training the people they have sent you to die fighting."
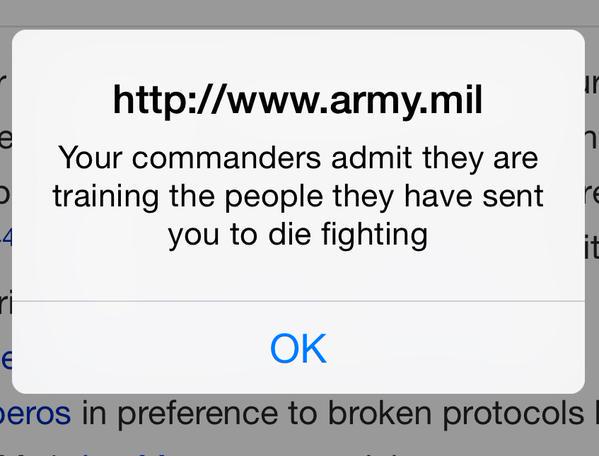
The notorious Syrian Electronic Army hacking outfit claimed responsibility for the attack which does not appear to have compromised any actual servers belonging to the US Army, but instead targeted the third-party content delivery network (CDN) used by the www.army.mil site.
A screenshot shared by the Syrian Electronic Army appears to show that they gained access to content displayed on the US Army's website through an admin panel at the Limelight Networks CDN.
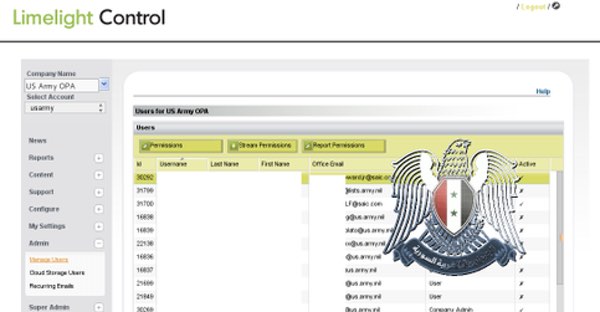
Fortunately, it appears that the hackers used the opportunity to display propagandist messages rather than attempt to infect visiting computers with malware.
In other words, people who surfed to www.usarmy.mil dodged a bullet.
Nonetheless, Fort Bragg, North Carolina, home of the US Army's airborne and special operations forces, posted a message on Facebook advising internet users not to visit the website until the issue was resolved.
Avoid using www.army.mil for the time being. The web site is currently down, reportedly from being hacked by the Syrian Electronic Army.
A spokesperson for Limelight Networks later gave a statement to Ars Technica saying that it takes security "extremely seriously" and is conducting a full investigation. Limelight's statement added that it did not currently believe that any customer data had been compromised.
The Syrian Electronic Army also posted a statement on its website, offering some clues as to how it succeeded in defacing the US Army website:
The hack was performerd (sic) after targeting the CDN service used by US Army website.The Syrian Electronic was able to intercept the content paths after discovering an exploit in the Contron Panel (sic) that provide the ability to edit the protected content paths.
The SEA posted on the hacked website several messages calling the US military to stop training terrorists in Turkey and Jordan.
Normally, the Syrian Electronic Army has used rudimentary phishing techniques to steal the passwords of media organisations and military outfits, but if they are to be be believed on this occasion they came across a vulnerability in the Limelight Networks CDN which allowed them to push unauthorised content onto the US Army's site.
If that is true - and that's a big if - then potentially the technique could be used to compromise other websites using the Limelight Networks CDN. I would be cautious about necessarily believing that to be a threat, because if it were the case you would have to wonder what benefit the hackers would have in offering clues as to how the defacement was perpetrated.
But whatever the precise mechanism, it's clear that all organisations - whether potential targets of the Syrian Electronic Army or not - have to consider not only the security of their own systems, but also of the third-party service providers that they rely upon.
When stories of defaced websites reach the mainstream media, as this XKCD cartoon famously illustrates, many less security-savvy people might believe that something much more serious has occurred.

There is a big difference between a website seemingly being defaced and databases being compromised and privacy being put at risk.
Nevertheless, make sure to ask your service providers the right questions about the security measures they have in place, use strong, unique hard-to-crack passwords, and where possible protect your accounts with two-factor authentication.
At the time of writing, www.army.mil has returned to normal working order. Let's hope it stays that way.




