As we have seen in previously published articles regarding ransomware, such as TorrentLocker targeting UK with Roya Mail phishing and ransomware in a country near you, these threats are appearing more frequently and in different regions.
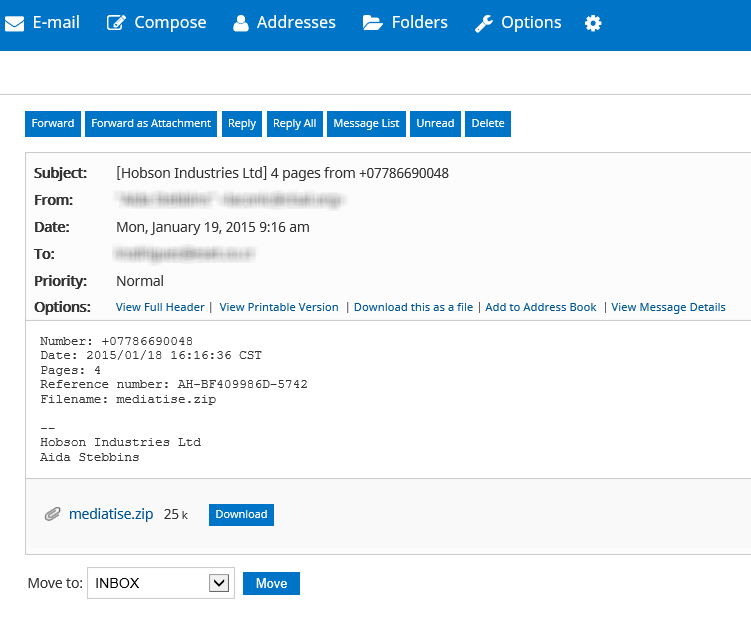
Starting a few days ago, we began receiving multiple reports of malware-spreading campaigns in various countries mostly in Latin America and Eastern Europe. A fake email purporting to contain a fax is in fact nothing more than a campaign to spread malicious code, of which the ultimate goal is to encrypt their victims’ files and then to extort a ransom in bitcoins for retrieval of the encrypted information.
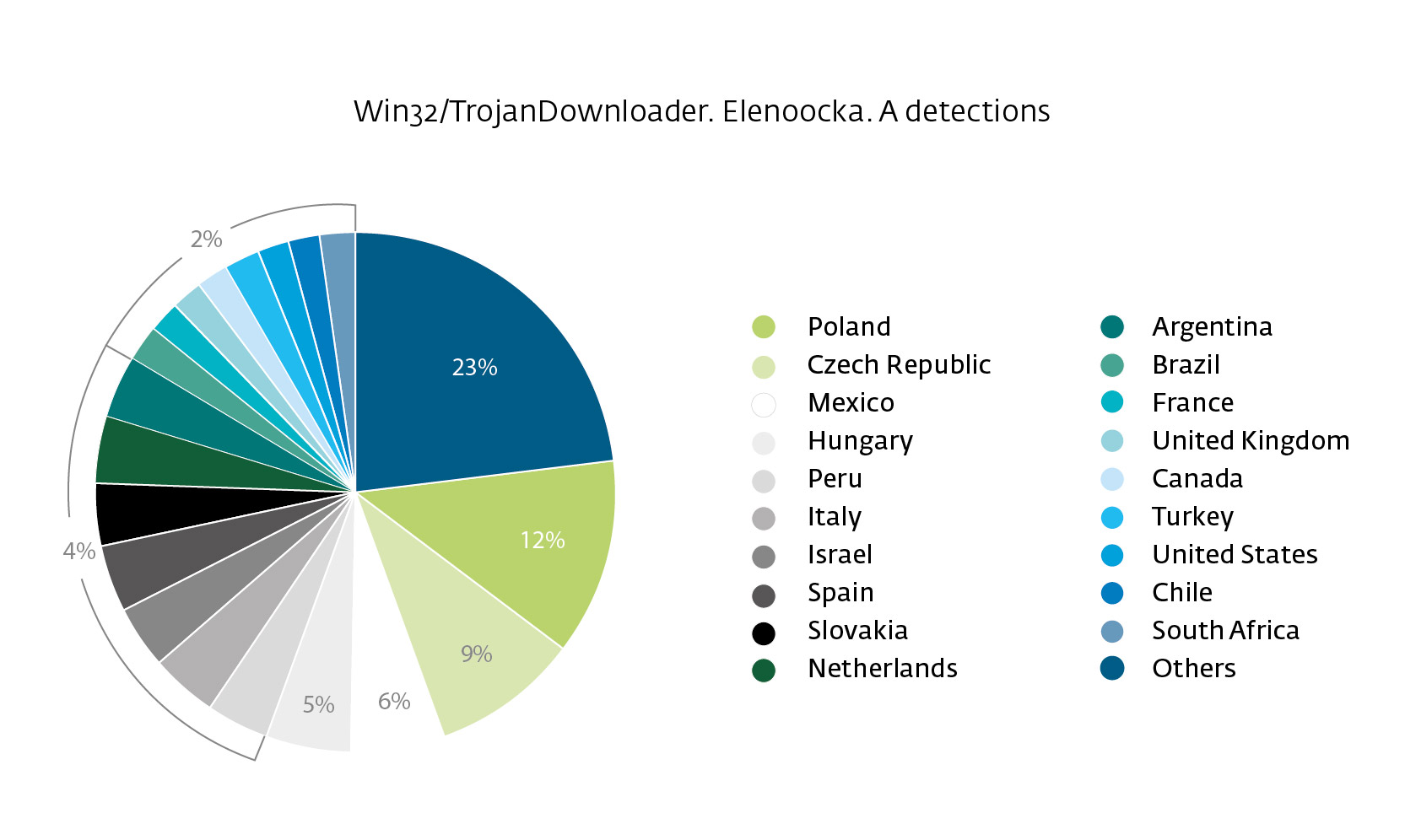
In this post we will see how these campaigns spread a new variant of CTB-Locker Ransomware, causing headaches for thousands of users. Poland, Czech Republic and Mexico are the most affected, as we can see in the following graphic comparing percentages by country:
This attack begins with a fake email arriving in the user's inbox. The subject of the email pretends that the attachment is a fax; the file is detected by ESET as Win32/TrojanDownloader.Elenoocka.A.If you open this attachment and your antivirus software does not protect you, a variant of Win32/FileCoder.DA will be downloaded to your system: all your files will be encrypted and you will lose them forever, unless you pay a ransom in bitcoins to retrieve your information.
Some variants of Win32/TrojanDownloader.Elenoocka.A connect to a remote URL to download malware detected by ESET as Win32/FileCoder.DA and known as CTB‑locker. This family of ransomware encrypts all files in a similar way to CryptoLocker.The main difference is that this family of malware uses another encryption algorithm, from which its name derives.
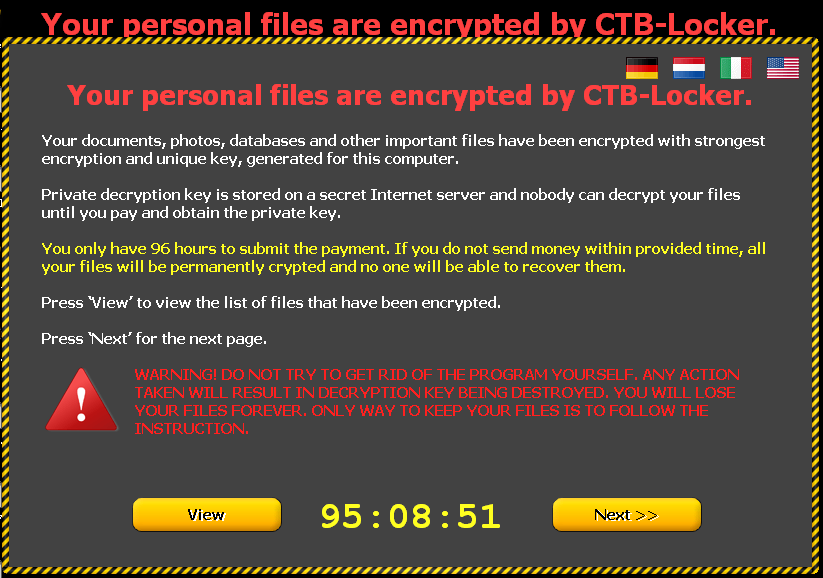
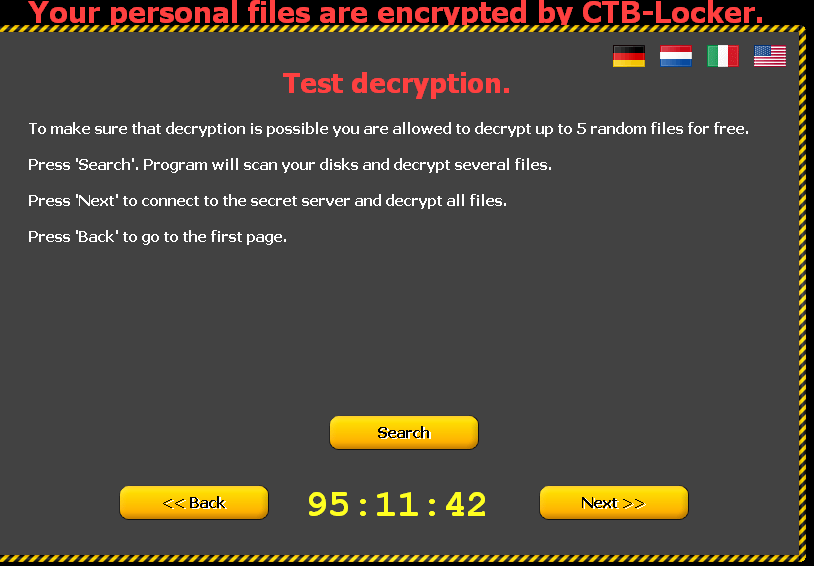
The result is similar to CryptoLocker or TorrentLocker, in that files with extensions such as mp4, .pem, .jpg, .doc, .cer, .db etc. are encrypted by a key, which makes it virtually impossible to recover the files.Once the malware has finished encrypting user information, it displays a warning and also changes the desktop background with a message similar to that seen in the image below:
The message will be displayed in German, Dutch, Italian and English, so adapting itself to many regions. Even though Spanish is not is one of the languages used to display the ransom message, we have seen many infections in Spanish-speaking countries.
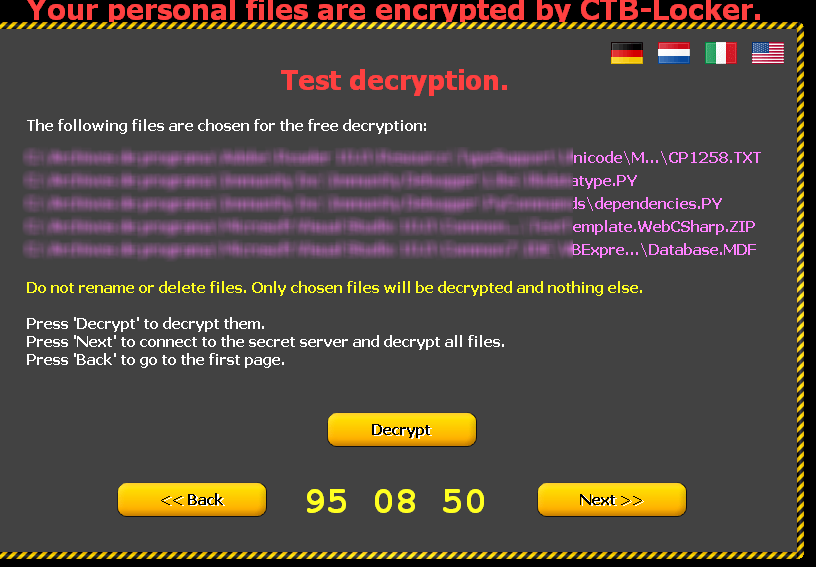
In order to reassure the users that they can recover their files once the payment is made, cybercriminals offer a demonstration of how it works, which you can see in the image below:
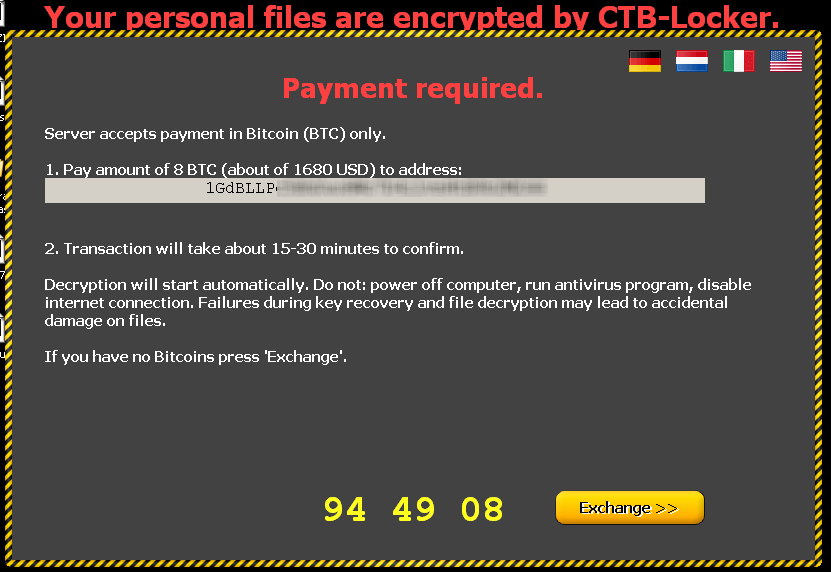
After the user views the demonstration, the attackers show how to unencrypt the files and where to send the bitcoins (BTC). They even offer a way to exchange bitcoins in case the user does not have them:
Another peculiar detail of CTB-Locker is this: not only is the message shown to the user in different languages but it also displays the currency appropriate to that language. If the user chooses to view the message in English the price is in US dollars, otherwise the value will be in Euros. The ransom is 8 Bitcoins, which today (20 January 2015) have a value of around 1,680 dollars.
From the technical point of view, Win32 / TrojanDownloader.Elenoocka.A it’s a small and simple threat. There are many different campaigns going on, like the one we mentioned above and we also spotted another one that had following attached samples invoice_%YEAR_%MONTH_%DAY-1%HOUR_%MIN.scr named eg. invoice_2015_01_20-15_33 .scr. We have seen that recent samples have a random word in from, eg. stride_invoice_2015_01_20-15_33.scr, tiger_invoice_2015_01_20-15_38.scr etc. Afterwards, it opens an RTF decoy document in Word. This document is found in a resource named "DATA" inside a CAB archive.
It is true that the encryption technique used by CTB-Locker makes it impossible to recover files by analyzing the payload. However, there are certain safety measures that are recommended for users and companies:
- If you have a security solution for mail servers, enable filtering by extension. This will help by allowing you to block malicious files with extensions such as .scr, as used by Win32 / TrojanDownloader.Elenoocka.A.
- Avoid opening attachments in emails of dubious origin where the sender has not been identified.
- Delete emails or mark them as spam to prevent other users or company employees being affected by these threats.
- Keep security solutions updated to detect the latest threats that are spreading and keep ESET LiveGrid technology On.
- Perform up-to-date backups of your information.
Mitigating such attacks is no simple task, and you need to take a proactive stance by supporting security technology with awareness and education. Following the tips above could help you and your company avoid this and similar threats.
Hashes:
- 81F68349B12F22BEB8D4CF50EA54D854EAA39C89 Win32/FileCoder.DA
- 0D4B6401EB5F89FF3A2CF7262872F6B3D903B737 Win32/FileCoder.DA
- 1DA7B3538A1D8B89179E17E91C7061B19932BBC8 Win32/TrojanDownloader.Elenoocka.A
- FE565E5589D496B838E037E99AA59E931129B7DA Win32/TrojanDownloader.Elenoocka.A
- 576BCD87B7EC38DE302201EC460DB9C0819B473A Win32/TrojanDownloader.Elenoocka.A