If you use Gmail as your ‘main’ email account - or rely on Google services such as Drive for work - it’s well worth revisiting Google’s Settings menus to give your Google security a boost.
While Google isn’t as keen on changing its security pages as Facebook, there are some additional security measures which long-term users may not be aware of.
For instance, two-step authentication is now built into Google security - and Google accounts offer a feature which allows users to instantly assess which apps and services have access to their data.
Google’s Dashboard, as ever, offers a great overview of the data you share with the search giant - but there are a few harder-to-find tricks and tweaks which can offer peace of mind about the data in your Gmail and Google accounts.
Google security: Check to see which apps and services can access your data
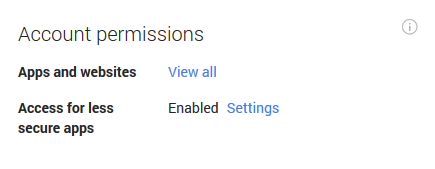
Google’s Account Settings page offers a very useful way to keep track of which apps and services have access to your Google Account data - and this can be quite a shocking visit.
Typically, mail clients, services such as Google Drive, and some Google apps will be able to access this data - but some online games tied to Google Accounts may also access it too.
The page should offer some details of what the apps are, and what data they need to access. If it’s an app you recognize, but no longer use - or worse, an app you don’t recognize, you can revoke its access direct from the page.
Make sure no one is signing into your account
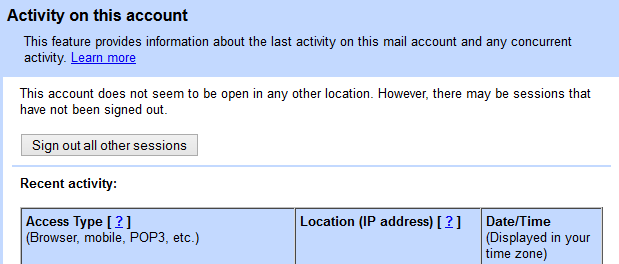
One of the best ‘peace of mind’ Google security features in Google Accounts is the ability to instantly see who is logging into your account, and from where.
The feature is accessible from the bottom left corner of the Gmail page in your internet browser - it opens a pop-up window with all the information you need.
If you’re worried that you’ve been hacked, or have had a device stolen, this page is a great first stop - you can instantly sign out all other sessions bar the computer you are on, and then change your password.
For anyone worried about Google security, you can also see where the IP addresses logging into your account are located - which helps track down any suspicions log-ins. The page also offers details of the type of login, length, and device - and whether it’s still active.
There’s a certain amount of ‘chaff’ here - the page shows each and every connected device which has access to your Gmail account - but it also offers a way to police email access on devices you might share, such as tablet PCs used by your family.
Set up two-step verification
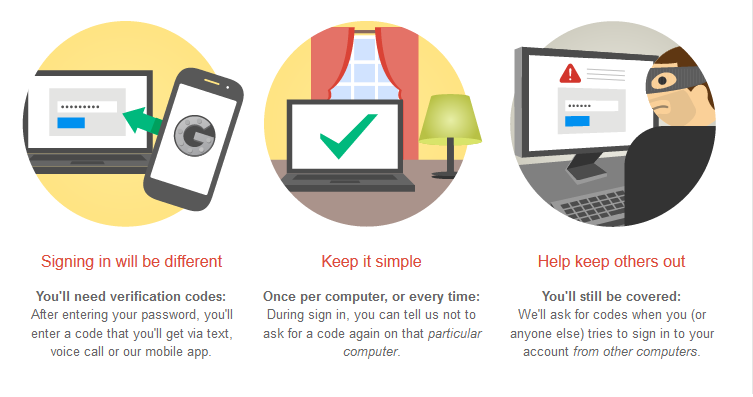
Google’s two-step verification offers a good second line of defense against account hacks - and there’s a welcome number of options to choose from, such as only requiring the second ‘step’’ when logging in from a new computer.
A detailed We Live Security blog post discussing the advantages of two-step verification systems can be found here.
Google’s system is typically all-inclusive - offering verification using a code delivered to a mobile phone via SMS message, or via automated call, or via a dedicated USB key.
Make sure you're not oversharing on Google+
Your Google+ page might not be your 'main' social network - but Google has built it to work as an anchor point for people searching for you, so it's worth revisiting your profile page to ensure you're presenting a good face to the world.
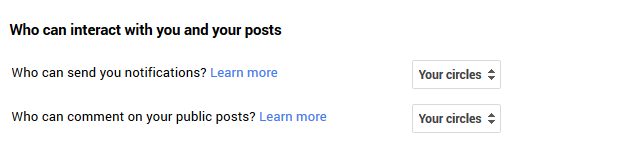
It's also worth controlling which Google+ users can contact you - if you lock it down to 'Your Circles' rather than the default, you'll be less vulnerable to spammers and other online undesirables.
Manage what Google stores about you
Google relies on storing information about you target the adverts delivered by Google ‘adwords’ - the text adverts that appear around searches and above Gmail’s Inbox - to the user.
This information is shared across Google services from YouTube to Search.
You can manage what information each Google service is storing, or has stored, about you, via Google Dashboard.
Some of the key ones to manage are location services, which can store a detailed history of where you have carried an Android device, and Chrome history (this is separate to web history, and will automatically open on any device you open the Chrome browser on while logged in.
Thankfully, Google itself offers a clear explanation of how this works - and lists tools web users may wish to use to prevent themselves being tracked.
antb / Shutterstock.com