Two Flash vulnerabilities that were fixed by Adobe 2 weeks ago are now being used in exploit kits. This is in addition to a third vulnerability, CVE-2014-0556, that was patched in September and that has also been added to Nuclear EK last week.
Before we get into the nitty-gritty detail, we strongly encourage you to take a moment to check that your Flash player is up to date, we have created a step-by-step guide explaining how to do so which you can read here.
The first exploit, CVE-2014-0569, is a vulnerability in the handling of the Alchemy opcode casi32. The Alchemy opcodes are a set of memory-access opcodes that are used by the CrossBridge SDK (see endnote).
This exploit has already been seen in Fiesta, SweetOrange and FlashPack so far. Alchemy has been the source of 2 other recent exploits (CVE-2013-5330, CVE-2014-0497) and is also seen in other exploits as it can be used to create straightforward read and write primitives.
The CVE of the second one has not yet been identified but the exploit structure is quite similar to CVE-2014-0515 and uses the method of corrupting the size attribute of a vector object to gain complete access to the memory space. It then also uses the Alchemy opcodes li32 and si32 to read or write at arbitrary addresses.
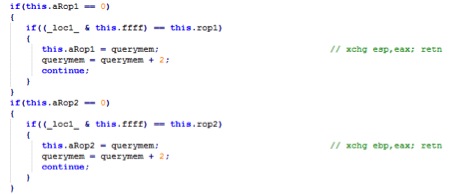
On 32-bit systems the exploit then dynamically searches for ROP (Return Oriented Programming) gadgets in the Flash module as shown below.
However, on 64-bit systems the ROP gadgets are obtained by computing a hash of the Flash version string and doing a lookup in a pre-computed table that is included with the exploit. This technique was also seen in CVE-2014-0497 but now supports 111 different versions of Flash, up from 20 in the earlier exploit. Whoever developed it went through a lot of effort to ensure it would work on as many systems as possible. This exploit has been seen in Angler and Astrum EK so far, and others will likely follow suit.
It seems quite clear that Flash has replaced Java as the target of choice for exploits on the Web : The last time a new Java exploit was added to exploit kits was more than a year ago. This is the 6th flaw in Flash being added to exploit kits in the last year, and there are other Flash vulnerabilities like CVE-2014-0502 that have not been added to kits but have been exploited in targeted attacks.
The exploitation love affair with Java ended not because of significant improvements to its security (Oracle fixed 8 severe vulnerabilities in July) but when browsers such as Firefox and Chrome started disabling the plugin by default and the latest versions of Java started displaying security prompts before launching applets. Perhaps it is time to consider applying a similar strategy for Flash. In the meantime, you can configure your browser to selectively load Flash objects on pages. You can see how to update Adobe Flash here.
For more details about Alchemy as well as in-depth analysis of some of the Flash vulnerabilities mentioned in this paper, I recommend the paper “Ubiquitous Flash, Ubiquitous Exploits, Ubiquitous Mitigation” by Chun Feng and Elia Florio which is now available on the Virus Bulletin website.