Yesterday, security researcher Jonathan Hall, of a company called Future South Technologies, accused Yahoo of having suffered a serious security breach via the recently discovered Shellshock vulnerability in Bash.
In a blog post, entitled "Yahoo! Shellshocked Like Ninja Turtles!", replete with Yahoo-style exclamation marks, Hall accused the firm of gross negligence:
Yahoo! Has been HACKED, and all your information with them is now in danger! All stemming from them not keeping up with technology and failing to patch a world-known vulnerability!
This breach affects ALL of us in one way or another, and it’s crucial that this problem be resolved with haste. The FBI took the information down and went on their way. Yahoo! has not responded at all. I’ve attempted to email them, call them, and resorted to contacting Marissa Mayer directly via both email and Twitter, neither to which I have received a response as of yet. The ignoring of this issue is grossly negligent and even almost criminal.
That sounds pretty troubling. After all, Yahoo has hundreds of millions of users that could potentially be impacted.
And, as researcher Jonathan Hall clearly expresses, he is less than impressed by the internet giant's response - claiming that it failed to act quickly enough after he reported the breach. According to Hall, a member of Yahoo's security response team only finally responding after he sent an email directly to CEO Marissa Mayer (which he helpfully cc'd to the New Orleans branch of the FBI):
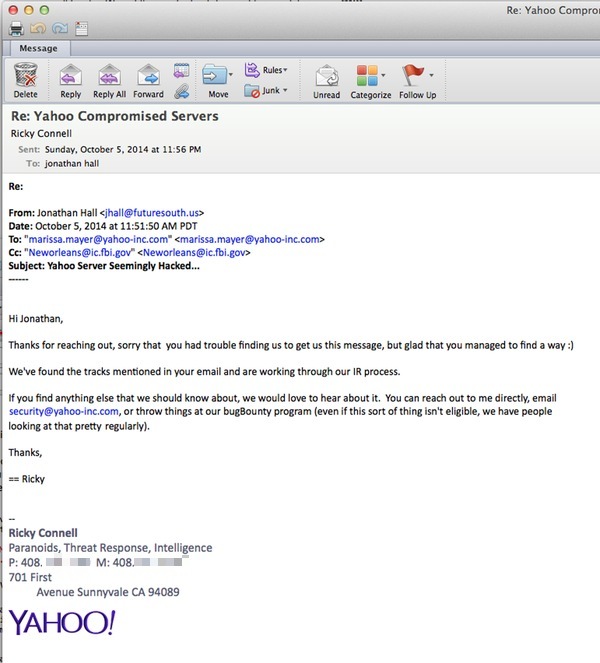
This and the fact that last year, Yahoo! rewarded a security firm's researchers with a Yahoo t-shirt after they found cross-site scripting (XSS) bugs that could compromise *any* yahoo.com email account is not helping to prove the firma's commitment with security.
Understandably, Yahoo was keen to address Jonathan Hall's claims before users were panicked by claims that "all your information with them is now in danger".
In a statement posted online by Yahoo CISO Alex Stamos, the company said that early on Monday it identified several servers that it had been informed were vulnerable to compromise via the Shellshock Bash bug.
However, the company said, although a "handful of servers" were impacted by a security flaw - and malicious code run upon them - they "were in fact not affected by Shellshock."
Three of our Sports API servers had malicious code executed on them this weekend by attackers looking for vulnerable Shellshock servers. These attackers had mutated their exploit, likely with the goal of bypassing IDS/IDP or WAF filters. This mutation happened to exactly fit a command injection bug in a monitoring script our Sports team was using at that moment to parse and debug their web logs.
Regardless of the cause our course of action remained the same: to isolate the servers at risk and protect our users' data. The affected API servers are used to provide live game streaming data to our Sports front-end and do not store user data. At this time we have found no evidence that the attackers compromised any other machines or that any user data was affected. This flaw was specific to a small number of machines and has been fixed, and we have added this pattern to our CI/CD code scanners to catch future issues.
As you can imagine this episode caused some confusion in our team, since the servers in question had been successfully patched (twice!!) immediately after the Bash issue became public. Once we ensured that the impacted servers were isolated from the network, we conducted a comprehensive trace of the attack code through our entire stack which revealed the root cause: not Shellshock. Let this be a lesson to defenders and attackers alike: just because exploit code works doesn’t mean it triggered the bug you expected!
Importantly, for millions of Yahoo users, the company found no evidence that users' data had been impacted and that the servers concerned did not store user data.
 Yahoo's Alex Stamos went on to remind researchers that the best way to contact the company should not need to be by dropping the CEO a line, but instead to visit its Bug Bounty webpage or email security@yahoo.com.
Yahoo's Alex Stamos went on to remind researchers that the best way to contact the company should not need to be by dropping the CEO a line, but instead to visit its Bug Bounty webpage or email security@yahoo.com.
For what it's worth, Yahoo realised last year that it had goofed by just offering a free t-shirt to those who uncovered its security holes.
One person who wasn't reassured by the Yahoo CISO's response was, perhaps unsurprisingly, the researcher who alerted them to the breach in the first place.
In a follow-up post to the Future South site, Jonathan Hall claimed that Yahoo's analysis of the issue didn't make much sense, and didn't mince his words when he described how he felt Yahoo was handling the problem:
At this point, I’m not convinced the problem is contained, nor am I convinced the users data is secure… And I am flat out accusing Stamos, and Yahoo!, of being dishonest and inaccurate in their reports of this breach, as well as being grossly negligent to their users and shareholders by releasing inaccurate and misleading information. You guys may want to go ahead and pull your pants up now.
Unfortunately for Hall, any serious concerns raised by his vulnerability discoveries are probably overshadowed by the passionate way in which he expresses them. A case of too much fury drowning out the science, in my opinion.
Yahoo, however, seems confident that its users don't have anything to fear. In an additional statement the company attempted to reassure its users:
"After investigating the situation fully, it turns out that the servers were in fact not affected directly by Shellshock, but by a minor bug in a parsing script... After a comprehensive investigation, we have found no evidence that user information was affected by this incident."
By the way, according to the researcher, it wasn't just Yahoo that was suffering as a result of the Shellshock Bash bug. He claims Lycos and WinZip had also been compromised.
Further reading: What does the Shellshock Bash bug mean for you?




