Last time we wrote about Android/Simplocker – the first ransomware for Android that actually encrypts user files – we discussed different variants of the malware and various distribution vectors that we’ve observed. What initially appeared as just a proof-of-concept – mainly because of Simplocker’s “not-exactly-NSA-grade” crypto implementation – has proven to be an actual threat in-the-wild in spite of its weaknesses. Also, the malware has been available for sale on underground forums.
Last week we spotted a variant of the ransomware that featured a few significant improvements.
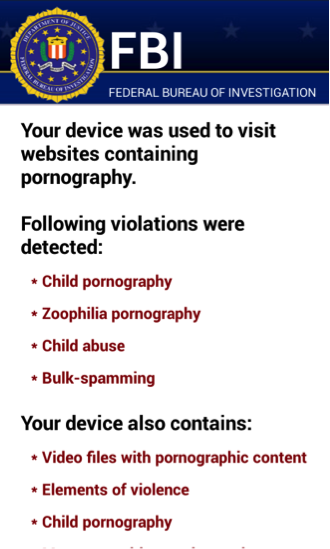
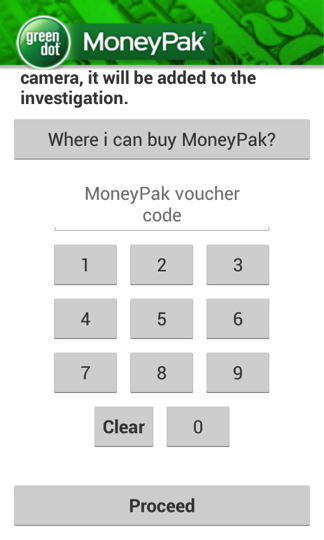
The first change that meets the eye in Android/Simplocker.I is that the ransom message is now in English rather than Russian. The victim is led to believe that the device was blocked by the FBI after detecting illegal activity – child pornography and so on – typical behavior of police ransomware that we’ve seen many times before. The demanded ransom is now 300 USD (as opposed to 260 UAH / 16 EUR / 21 USD) and the victim is instructed to pay it by a MoneyPak voucher. Like other previous Android/Simplocker variants, this one also uses the scareware tactic of displaying the camera feed from the device.
From a technical perspective, the file-encrypting functionality remains virtually unchanged, apart from using a different encryption key, but this recent Simplocker variant does contain two additional tricks to make the victim’s life more miserable.
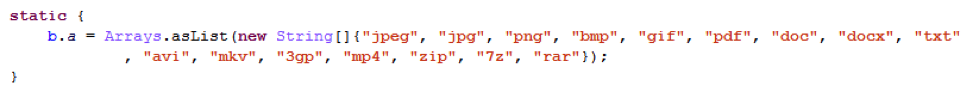
In addition to encrypting documents, images and videos on the device’s SD card, the trojan now also encrypts archive files: ZIP, 7z and RAR. This ‘upgrade’ can have very unpleasant consequences. Many Android file backup tools (which we strongly recommend, by the way) store the backups as archive files. In case the user has become infected with Android/Simplocker.I, these backups will be encrypted as well.
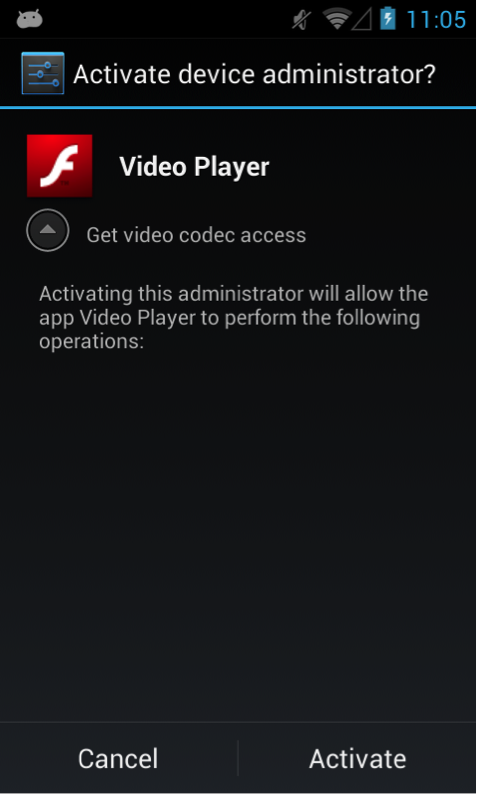
Secondly, the malware now asks to be installed as Device Administrator, which makes it a lot more difficult to remove. Legitimate Device Administrator applications use these extended permissions for various, mostly security-related reasons. For example, corporate Exchange administrators can enforce password policies, remotely wipe lost or stolen devices, and so on.
Android/Simplocker.I (and other Android ransomware in the past) only uses the functionality for its own protection, since the user must first revoke the application’s Device Administrator rights before uninstalling it. And that’s rather difficult to do when the ransomware is locking your screen.
As usual, the trojan will use social engineering to trick the user into installing it – in the screenshot to the left it’s masquerading as a Flash video player.
Our Android/Simplocker detection statistics until today don’t indicate the threat to be widespread in English-speaking countries.
In case your files have been encrypted as a result of an Android/Simplocker infection, you can use the updated ESET Simplocker Decryptor to restore them. But as always, we recommend focusing on prevention ;) Also, while you should be careful when installing any application on your device, be extra careful when the installed application asks for Device Administrator rights.
SHA1 Hash: 72ec80b52ad38417240801dba1a730ab9804a2f9