Thinking of spending some time perusing Japanese porn websites before you do your online banking?
You might want to think again.
Security researchers at ESET have published a detailed analysis of an organised malware campaign that stole the login credentials of online banking customers after infecting PCs that had visited X-rated Japanese websites.
ESET's team of experts have taken a close look at the Win32/Aibatook malware that targets users of Internet Explorer who are customers of Japanese banks, and in particular visitors to some of the country's most popular pornographic websites:
sokuhabo.net
www.uravidata.com
ppv.xxxurabi.com
mywife.cc
Upon visiting any of the above compromised sites, users can be redirected to an exploit page that attempts to take advantage of Java vulnerability CVE-2013-2465.
Of course, it's important to point out that any website can potentially be compromised, and be running malicious code designed to infect a visiting computer. It's not the case that an adult website is necessarily more dangerous to your computer's health than, say, the website belonging to a major American television network or a website devoted to a programming language.
But criminals eager to break into bank accounts certainly have no qualms about hacking porn websites, in the knowledge that they are likely to receive lots of traffic (and hence guaranteed to generate more victims).
It is perhaps unusual, however, to see only one single vulnerability exploited - rather than the more common approach used by cybercriminals today to use an exploit kit to attempt a battery of attacks against visiting computers, hoping to find one which hits the bullseye.
Regardless, the criminals clearly think that their approach works well enough, and an unassauming 404 error message is displayed when the user's browser is redirected to a third-party website.
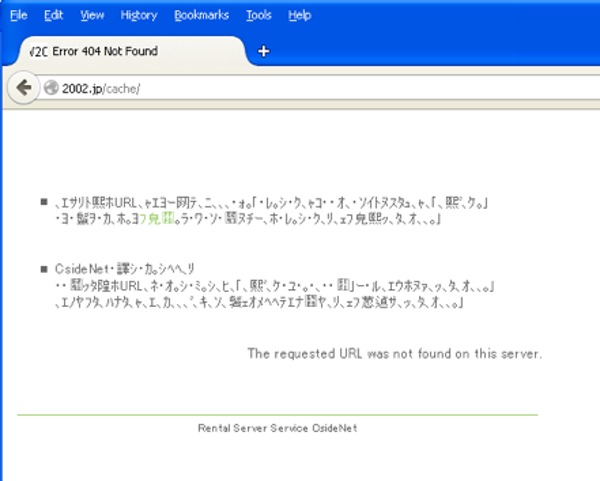
The 404 "Page not found" error message may seem unassuming enough to the casual observer, but a quick look at the webpage's source code reveals that is more than a simple error page - and secretly harbours code to run a malicious Java applet.
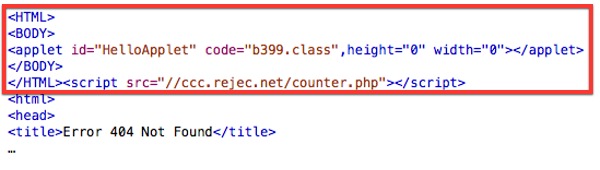
In a seeming attempt to avoid detection, the code contains a counter which appears to be designed to only insert the snippet of HTML for a limited number of victims each day.
With the malware now in place, it can begin to do the rest of its dirty work - waiting for victims to log into online banks with Internet Explorer (the most widely-used browser in Japan) and inject bogus forms into the process.
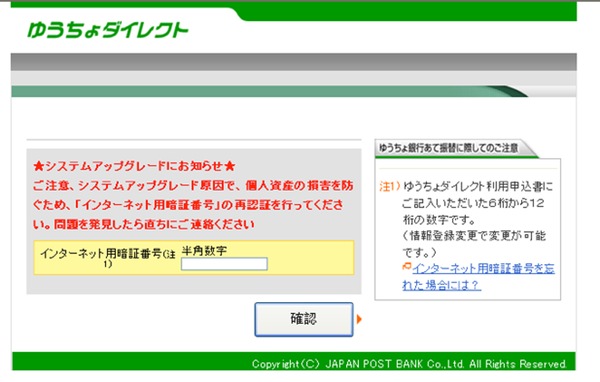
In the above example, the Aibatook malware has silently injected a false login page as a user visits the Japan Post bank, requesting that they fill in their personal details because of a system upgrade.
Stolen data is then sent to the criminals via a C&C (Comamnd and Control) server.
Craftily, if the user visits a page on the Japan Post website designed to warn customers of the dangers of phishing attacks they are redirected back to the login page before they have a chance to see any security advice.
In recent months, those responsible for the Aibatook attack have created new versions of the malware, capable of stealing credentials from users of web-hosting services and domain resellers, and switching from Delphi to C++ as their programming language of choice.
In all, customers of over 90 websites are thought to be being targeted by the information-stealing criminals.
Java vulnerability to blame
The Java vulnerability exploited by the attacks was patched by Oracle back in June 2013.
In an ideal world you would hope that because a fix was available for the vulnerability, no one would have still been falling foul of the attack in the months since. However, it's clear that many computer users are not protecting their computers with the latest security patches - giving online criminals a larger window of opportunity to infect PCs and steal money from online accounts than they could hope for in their wildest dreams.
The simple truth is that when computer users fail to keep their systems updated with security patches they are exposing themselves to greater risk, and making life easier for malicious hackers.
Computer users should also consider carefully what other steps they are taking to minimise the attack surface.
Just about every piece of software you run on your computer has vulnerabilities - whether they be known or unknown. Most, hopefully, are not serious and cannot be easily exploited by hackers.
But every additional piece of code or functionality that you enable on a PC increases the potential risk. A smaller attack surface makes the exploitation of vulnerabilities more difficult, and so will help mitigate risk.
With that in mind, all computer users should ask themselves: Do I need to run Java in my web browser?
 Java is probably the most targeted development platform for exploit attacks, and some reports have suggested that a gob-smacking 50% of all exploits target Java.
Java is probably the most targeted development platform for exploit attacks, and some reports have suggested that a gob-smacking 50% of all exploits target Java.
Over the last few years, it has become increasingly common to find cybercriminal gangs exploiting Java vulnerabilities - as it is so commonly installed, and has a poor history when it comes to security holes.
As a result, and you might have guessed this, Java is not my favourite cup of tea.
Although it's true that there are some specific applications that need Java, my suspicion is that most computer users could get by just fine without having it enabled in their browser. Even if they do need it for one or two specific sites or applications, it might be better - from the security point of view - to disable Java in the browser and use a *different* browser when you need to access those sites.
If you're not sure if you need Java enabled, ask your IT support desk or turn it off on your home computer and see if anything stops working. If you don't notice any difference in your day-to-day browsing of the web, chances are that you never needed it turned on at all.
Congratulations - you've just made your computer a whole lot safer.
Not that I'm recommending, of course, that you now visit Japanese porn websites...




