ESET researchers recently came across a targeted attack against the Vietnamese government's Ministry of Natural Resources and Environment (MONRE). In this report, we will look at how the attackers targeted Vietnamese government employees, the behavior of the malware on MONRE's systems, and how the attackers attempted to exfiltrate data.
The Vietnamese Ministry of Natural Resources and Environment has been under targeted attacks according to a recent article by ThreatConnect. Although the attack we discuss in this article may not be related to the threat campaign detailed in ThreatConnect's research, it does show the interest attackers have in this Vietnamese government agency.
Getting in: The phishing component
Vietnamese government employees at MONRE received email with a Microsoft Word document attachment. MONRE uses webmail as a means of providing email access to its staff, so employees would have to download the Word document—as opposed to just previewing it in their web browser—in order for it to infect their computers.
When opened in Microsoft Word, the document exploits a vulnerability to drop one executable file, named "payload.exe", onto the computer. This Trojan dropper file contains three additional executables in it, which we will describe below in further detail.
Malware Behavior
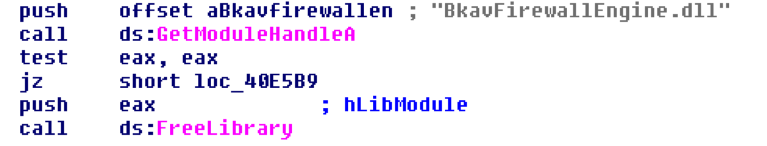
When run, the malware will check to see whether Bach Khoa Anti-Virus (BKAV) is present. This is done to circumvent BKAV's protections. If found, the payload.exe Trojan dropper unloads BKAV's "BkavFirewallEngine.dll" from memory using the FreeLibrary Function as shown in the code below:
The three files dropped are named Framework.dll, StartExe.exe and W7e1.tmp and are saved into the %temp% directory. All these files are now detected by ESET as Win32/Agent.VXU. Also of interest is that the timestamps in the PE file headers are probably relatively recent, dated April 24, 2014. While this data could be falsified, we do not believe this to be the case.
1 BKAV is a Vietnamese antivirus program developed by Bach Khoa Internet Security Center (BKIS), a joint venture between the company and the Hanoi University of Science and Technology.
A Glitch in the Matrix
It was observed that the main dropper file, payload.exe, does not successfully execute its dropped files on Windows XP or earlier versions of Windows. This appeared to be a bug in its code, where it tries to execute them using startexe.dll instead of startexe.exe.
SHELLEXECUTEINFO.lpVerb = "open"
SHELLEXECUTEINFO.lpFile = "%temp%\startexe.dll" ← bug
SHELLEXECUTEINFO.lpParameters = "-a a"
However, under Windows Vista and newer versions of Windows, the dropped files are successfully executed via code injection into explorer.exe.
Data Exfiltration
Framework.dll, which runs as a service named “Framework”, connects to 31.170.167.168:443 (USA) or www.google.zzux.com:443, a server located in South Korea. It was observed that a connection to the zzux.com domain was tried only if the IP address for the host is different from the IP address 31.170.167.168.
This is a simple backdoor that sends the local IP address, as well as starting a Windows command shell “%system%\cmd.exe” with input/output redirected to the command-and-control (C&C) server.
Going for the MONRE shot
At this point, we are unable to share any further intelligence about the perpetrators behind this campaign. While a Vietnamese environmental administration may not seem at first glance to be a high-value target, it is worth noting that any government's environmental agency is going to have a great deal of confidential information of national economic and strategic concern. Interest in the South China Sea is at an all-time high now, and data such as maps, surveys, studies and reports are likely to be of interest both to regional superpowers and to corporations operating in the area.
Conclusion
This threat, like many others, is a good reminder that where there is valuable information; there are cybercriminals who will want to steal it.
When faced with targeted attacks exploiting vulnerabilities, it is critical to ensure that security patches to a system are up-to-date and applied in a timely manner. That includes operating systems, applications, and browser plug-ins. No less important is security awareness education. Some simple but effective practices to teach include:
1. Never open unsolicited attachments or click on links in email, even when they appear to come from those you know and trust.
2. If you feel you *must* open or click, first consider the following questions:
- Are your operating system, applications software, and security software(e.g. anti-malware) fully updated?
- Can you contact the sender using a different means than email alone (phone, text, in person, etc.) to authenticate the email or content received, before opening or clicking?
- Do you have a clear understanding of what the attachment or link is?
- Is there some level of attribution as to the source of the link if something goes wrong?
3. Encourage employees to report to the appropriate IT staff any suspicious computer activity, connection requests, email, or behavior.
Analysed Sample Hashes
Kudos to Miroslav Babis for analysis of this threat.
| Filename | SHA-1 hash |
| payload.exe | ffddea36e153372ef4efade503fd7d9217a8344d |
| StartExe.exe | ab7e06327c309752c007cf56315caa785cbf06b4 |
| Framework.dll | 1d91c56ebe24c3b88fb1ba88ea1377739b8f0360 |
| w7e1.tmp | c8cbd43698cdd852d779252f3afb5731fe2437e7 |