Are you a Facebook user?
If so, be on your guard if you see a screen like the following popping up on your screen:
VerificationWelcome back
Due to a rising number of attempts in order to gain unlawful access to the personal information of our users and to prevent corrupted page data to spread Facebook administration introduces new extra safety protection system. It's free and it keeps you safe. Our IT specialists developed unique software tool for safe and secure authorization. With this software you don't need any extra account profile or password all you need is to install it and everytime you log in you will input an access code generated by the software on your personal phone. We care for our users, protection of their private information is one of the priorities. Meanwhile application might not be available for some operating systems.
[Prompt for mobile phone number]
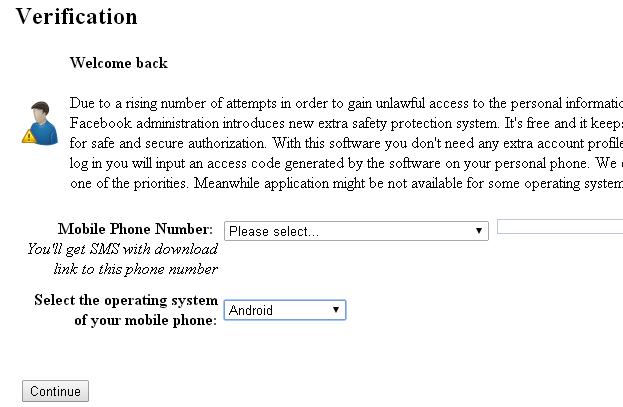
Hopefully the poor grammar is enough to trigger your alarm bells, and prevent you from entering your mobile phone number.
But if it's not, there is a risk that malicious hackers could soon be listening in to the calls made on your Android smartphone, intercepting your SMS text messages, and even listening in to any private conversations you are having in the vicinity of your phone.
And, if the hackers can read your SMS messages, they can potentially break into your online bank accounts too.
ESET threat researcher Jean-Ian Boutin detailed the latest incarnation of this threat last week, in a blog post on We Live Security.
Here is how the attack works.
The message you have seen pop up while you are logged in to Facebook isn't from Facebook itself, but it's not the case that Facebook's website has been hacked either.
Hackers are using a notorious banking Trojan horse called Win32/Qadars to display the bogus message from Facebook, in an aggressive attempt to infect Android smartphones.
The Windows-based malware is being used to inject the message into your web browser via JavaScript - making it appear, to all intents and purposes, as if Facebook's website is serving up the form.
If you make the mistake of giving the form your mobile phone number, you are prompted to download an app onto your Android smartphone.
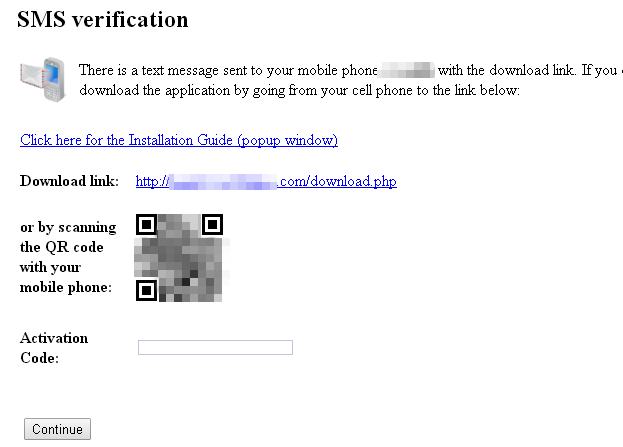
Regular readers of We Live Security won't be surprised to see that the app download is hosted on a third-party site, rather than the more trusted official Google Play store, meaning that you may have to change your Android settings to permit the installation:
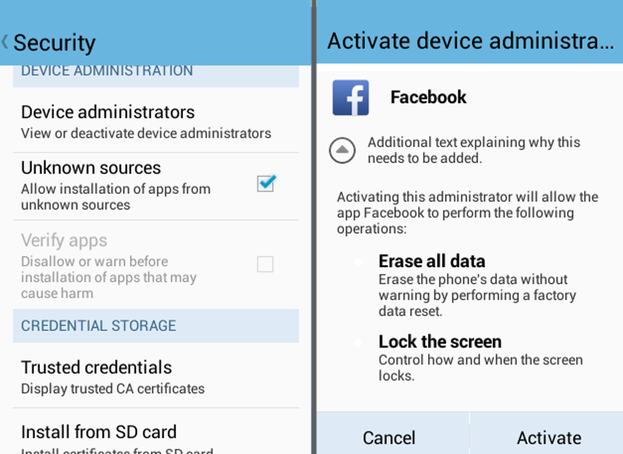
This should be, of course, another opportunity for alarm bells to ring in your head. If Facebook was rolling out a new security feature, that required the installation of a new app on your Android phone, wouldn't they use the regular Android app store to distribute it?
And why would the app need God-like admin powers over your smartphone which mean it could, if it wished, completely wipe all of the data on your device?
The truth is, of course, that the attack is trying to dupe you into installing an Android Trojan horse called iBanking (detected by ESET security products as Android/Spy.Agent.AF) onto your smartphone.
Once in place, the Android Trojan can spy on the phone's activities, including private voice calls, stealing SMS messages, contact lists and call logs, recording audio captured by the Android devices's microphone even when it's not making a call, and grabbing the device's GPS co-ordinates.
In the past, the iBanking malware has been used to bypass two-factor authentication systems, intercepting the mTANs (mobile transaction authorization numbers) sent via SMS by many online banks, as well as popular internet services such as Google, Twitter and - indeed - Facebook itself.
Clearly the online criminals recognise that more and more people are recognising the value of enabling two-factor authentication on their online accounts, and evolving their malware to try to waltz around it.
Although the malware can be used to steal two-factor authentication tokens for a variety of websites, including social networks, it seems likely that the principal targets for this kind of malware will still be online bank accounts for some time to come.
After all, that's where the big money is.
Further reading:




