A rootkit is a piece of malicious software which has the advanced capability of hiding itself on an infected system. This is usually done by hooking system functions. For example a rootkit could be used to hide files from the user by hooking functions responsible for listing the contents of a directory. Rootkits are frequently used in combination with other malware, which it hides from users and security products. The number of malware families that have rootkit capabilities and target Microsoft’s Windows systems is well into double figures.
We think that there could be rootkits targeting the OS X platform, but we have very limited visibility into that threat right now: We know that we don’t know. We do know that various websites and even paperback books [1, 2] document how rootkits can work under OS X. We have seen OS X malware using rootkit techniques in the past. The most notable example being OSX/Morcut also called Crisis by other vendors. This malware was used to steal information from infected Macs and loaded a kernel extension so as to hide its files from the victim.
Detecting a rootkit under OS X currently involves dumping and analyzing kernel memory. It requires time and knowledge. It is not something accessible to everyone.
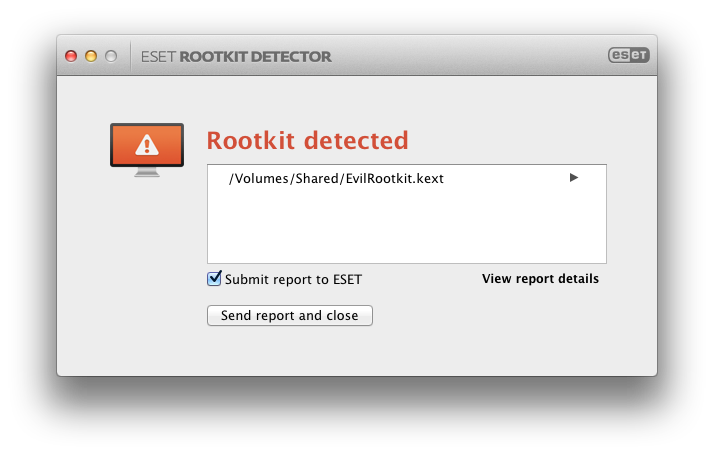 Today, ESET is releasing a simple tool to detect rootkits on OS X. This tool, named ESET Rootkit Detector, can be downloaded from the following URL: http://eset.com/int/support/rootkit-detector/. The tool aims to detect modifications in the OS X kernel memory that might indicate the presence of a rootkit. Its usage is very simple, a user only needs to download and run the application. Since a kernel extension is needed to detect modifications to kernel memory, the user will be prompted for Administrator privileges. After a couple of seconds of scanning, the result is displayed to the user.
Today, ESET is releasing a simple tool to detect rootkits on OS X. This tool, named ESET Rootkit Detector, can be downloaded from the following URL: http://eset.com/int/support/rootkit-detector/. The tool aims to detect modifications in the OS X kernel memory that might indicate the presence of a rootkit. Its usage is very simple, a user only needs to download and run the application. Since a kernel extension is needed to detect modifications to kernel memory, the user will be prompted for Administrator privileges. After a couple of seconds of scanning, the result is displayed to the user.
If a malicious module is found, you have the option to send a report to ESET and we would appreciate people doing that. We need your help to become better acquainted with what we don’t already know. Our team of reverse engineers will go through the submitted files and make sure users are properly protected if a new threat is discovered.
 Bear in mind that this tool is still in beta stage so we do not recommend running it on critical production equipment. On the other hand, we would love to have as many people as possible try it and work with it. This would allow us to see how well our new technology is working and, if something is found, this will be great research material to enable us to better track and document rootkits targeting the OS X platform. We always need to know more about the unknowns.
Bear in mind that this tool is still in beta stage so we do not recommend running it on critical production equipment. On the other hand, we would love to have as many people as possible try it and work with it. This would allow us to see how well our new technology is working and, if something is found, this will be great research material to enable us to better track and document rootkits targeting the OS X platform. We always need to know more about the unknowns.
[1] Charlie Miller, Dino Dai Zovi, The Mac Hacker’s Handbook, March 2009, ISBN: 0470395362
[2] Paul Baccas, Kevin Finisterre, Larry H., David Harley, Gary Porteous, OS X Exploits and Defense, Elsevier 2008, ISBN: 978-1-59749-254-6




