September 23, 2013 is a date to note if your organization handles health-related information. You might be a medical clinic, or a company that does IT work for a clinic. You might not think of yourself as being a medical professional. You could be a data storage provider or an IT consultant who does some work for a company that sometimes helps out hospitals. The point being: Now is the time to make sure you are aware of the implications of September 23.
So what happens on September 23, 2013? That's the deadline for compliance with new HIPAA regulations. If you're thinking HIPAA is "so last decade" then you need to think again, as in HIPAA 2.0. In January of this year, the U.S. government published new regulations that extend the reach of federal healthcare privacy and security laws, embracing a whole new range of companies that service the healthcare industry.
The new rules, codified as the "omnibus regulations," also known as the “Final Rule,” include significant changes to the privacy, security, enforcement, and breach notification rules that were promulgated under the Health Insurance Portability and Accountability Act of 1996 (HIPAA) and the Health Information Technology for Economic and Clinical Health (HITECH) Act. According to the Head of the Office of Civil Rights (OCR) at the Department of Health and Human Services (HHS):
This final omnibus rule marks the most sweeping changes to the HIPAA Privacy and Security Rules since they were first implemented. These changes not only greatly enhance a patient’s privacy rights and protections, but also strengthen the ability of my office to vigorously enforce the HIPAA privacy and security protections, regardless of whether the information is being held by a health plan, a health care provider, or one of their business associates.
The Final Rule became effective on March 26, 2013, and compliance is generally required by September 23, a little over 40 days from now. While the enforcement body, the OCR, did not immediately begin investigating and fining organizations after the original HIPAA rules went into effect, I would not bet my business on there being a "grace period" with the new rules. After all, PHI breaches are currently running at an average of 17,000 per day, based on the HHS breach data. You have to assume reducing that unhappy privacy statistic is a priority for OCR.
PHI and Business Associates
Practically every business that processes, stores or otherwise handles protected health information (PHI) is required to comply with privacy and security controls. PHI is individually identifiable health information, in other words, health information which can be linked to a particular person. Specifically, this information can relate to:
- The individual's past, present or future physical or mental health or condition,
- The provision of health care to the individual, or,
- The past, present, or future payment for the provision of health care to the individual.
Clinics and hospitals and health insurance companies may be the first things to come to mind when you read those bullets and these are generally considered "covered entities" under HIPAA. But the structure of the healthcare industry in America is such that a vast array of organizations and individuals currently service the industry. HIPAA refers to these service providers as "business associates" which are generally defined as: "a person or entity that creates, receives, maintains, or transmits protected health information (PHI) in fulfilling certain functions or activities for a HIPAA-covered entity." (Godfrey & Kahn, S.C.)
(Let me say right now that I am not qualified to give you a legal opinion as to whether or not you or your company constitute a business associate under HIPAA 2.0. One area where this determination gets pretty tricky is the cloud and what are formally known as MTDCs or multi-tenant data-centers. Fortunately, some cloud providers offer very helpful information on this topic, like this AIS article about HIPAA and MTDCs.)
OCR to "vigorously enforce the HIPAA privacy and security protections"Under HIPAA 1.0 a covered entity was supposed to impose privacy and security requirements on the business associates with whom they did business by means of contractual agreements (BAAs or Business Associate Agreements). However, when the mandatory reporting of breaches of unsecured protected health information began in 2009, it quickly became clear that business associates were going to be a problem. So far, 57% of breaches involving 500 or more individuals have been from business associates, impacting five times as many individuals as breaches from covered entities. Now, under HIPAA 2.0, both the HIPAA Security Rule and the HIPAA Privacy Rule apply directly to business associates, making them potentially liable for civil and criminal penalties for any non-compliance with the HIPAA regulations.
Serious insecurity consequences
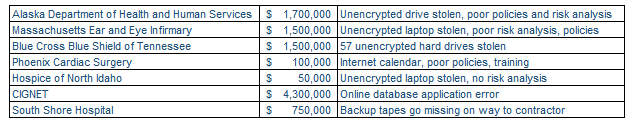
What sort of penalties are we talking about when HIPAA violations come to light? Consider this table of amounts levied in 2012, totaling almost $10 million:
Clearly, HHS does not like people storing unencrypted PHI on mobile devices. And when OCR comes to investigate, you will be in trouble if you don't have well-documented risk analysis, policy, and controls. You can find more HIPAA enforcement cases online. What you won't see yet are fines levied against business associates. I predict we will see the first of these towards the end of next year, with possible headlines like this:
Cloudy with a chance of lawsuits: Data center dinged over medical record handling
Tip trip trashes clinic reputation: Record management firm faces five figure fine over health data flub!
Apart from the excessive alliteration, such stories are entirely feasible in the wake of September 23, 2013. Now is the time to ask if your organization needs to revisit HIPAA compliance. Remember, not every PHI breach ends in a fine. If you can show your organization has made a reasonable effort to comply with HIPAA 2.0 you may not be dinged (as in subject to a fine and subject of a national press release).
I have recorded a webcast on the new HIPAA that you can watch. If you would like a copy of the slides that I used in the webcast please email a request to askeset [at] eset [dot] com. Also check out ESET Solutions for Healthcare for more helpful resources.
Stephen Cobb, CISSP
Senior Security Researcher