In our previous post on Operation Hangover, we revealed the existence of an attack group, apparently operating from within India, who were mainly targeting systems in Pakistan. In this post, we will analyze the Mac OS X samples that have been linked to this group and will provide new evidence that the Mac and Windows spywares are related.
F-Secure reported on May 16 the discovery of a Mac spyware on an African activist’s computer attending the Oslo Freedom Forum. Four days later, on May 20 Norman revealed the existence of a link between this incident and Operation Hangover by identifying that a Command & Control domain used by the Mac spyware was part of the operation’s network infrastructure.
These Mac spyware programs were signed by Apple Developer ID “Rajinder Kumar”. F-Secure reported that at least two malware families, OSX/KitM and OSX/Hackback, had samples signed by this developer.
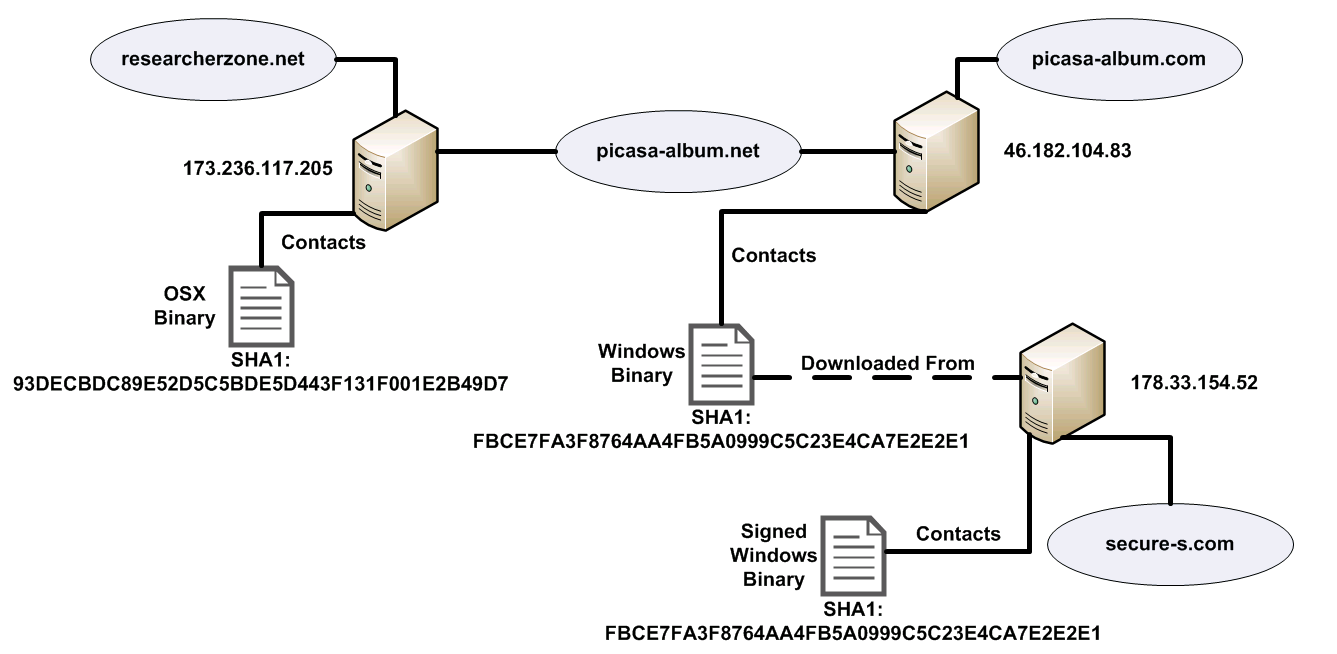
We can confirm that the Oslo Freedom Forum incident and operation Hangover are indeed related. We found other domain names that were used by both Mac and Windows spyware variants. Using passive DNS information, it was possible to link wreckmove.org and torqspot.org as they were once hosted on the same IP. It was also possible to link in a similar manner researcherzone.net, picasa-album.net, picasa-album.com and secure-s.com. The first domain was found in an OSX/Hackback.A sample while the last three were found in different Windows spyware. The last domain, secure-s.com, was used in one signed binary that we found during our initial research. The following diagram better explains the relationship:
We also found that one of the dump zones, where exfiltrated data is uploaded, contains the string “yash” as part of its path:
hXXp://researcherzone.net/yash/upload.php
This is rather interesting as this string also appears in the project paths embedded in numerous Windows binaries used in Operation Hangover:
“D:\YASH\PRO\MY\DELIVERED\2012\KEYLOGGERS\English Only\new\without_Logfile\ProLocalKilr.vbp”
As pointed out earlier, the OS X malware linked to Operation Hangover have been classified in two different families: OSX/Hackback and OSX/KitM. After analysis of the samples, we have determined that the same developer is behind both families, relied on the same code base and that the only difference between the two file stealers is the screen shot feature used in OSX/KitM.
Evidence identified in the Mac samples shows that the same network infrastructure has been used for both Windows and Mac spyware. We also found evidence of the malware writer’s name or nickname appearing in both a URL used by the Mac malware and in the project data embedded in the Windows malware. Since the Oslo incident seems to be totally unrelated to this group’s other activities, we might be witnessing a case of espionage as a service.
Special thanks to Marc-Étienne Léveillé who analyzed the Mac samples.