Could distributed denial of service (DDoS) malware be evolving to defeat anti-DDoS security measures like CloudFlare? We do not usually see a lot of innovative denial-of-service malware in our day-to-day work. What we do see usually boils down to the basic flooding techniques: TCP Syn, UDP and ping floods, and sometimes HTTP-oriented floods.
Of course, many products and services are available to webmasters who want to defend against such DDoS attacks. CloudFlare is one of them. When we analyzed a new piece of malicious software that looked suspiciously like yet another DoS tool, we did not expect to find anything particularly interesting. However, it turns out that the malware dubbed Win32/DoS.OutFlare.A implements a technique we have not seen before: a routine intended specifically to defeat the very popular CloudFlare anti-DoS service.
Win32/DoS.OutFlare.A modus operandi
On execution, the malware will attempt to create a mutex with the string "Global\sad_day". If it succeeds, it will copy itself to %APPDATA%, add a registry entry to start itself at boot, and relaunch itself. The new process will then launch iexplore.exe in suspended mode and inject its payload into it. The payload is obfuscated with API call redirection. The callflow is also obfuscated in the sense that every major function is called within a CreateThread call.
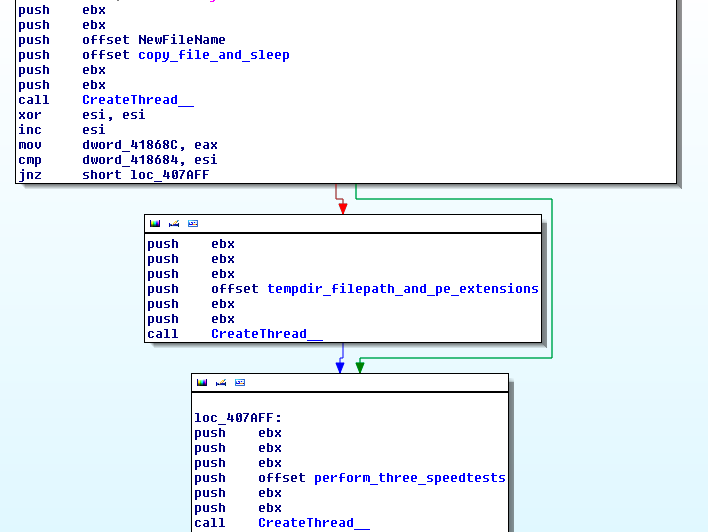
Before even connecting to its C&C, OutFlare will perform three upload speed tests, using a public service from www.speakeasy.net, and store the results in memory.
Once completed, the bot will connect to an IRC server on the domain 7.[redacted].lt (7.nnn.nnn.nnn at time of analysis) on port tcp/9835 and join the channel #main.
At this stage, the bot will sit idle in the channel, waiting for a specific command. Most of these commands are related to various DoS techniques. The one labelled 'cf' is particularly interesting.

This consists of a special routine made specifically to bypass the CloudFlare client-side DoS detection mechanism. To fully understand the bypass mechanism, a little knowledge about how CloudFlare works is required.
CloudFlare - how does it work?
CloudFlare is a very popular service that adds speed, reliability and some level of protection to websites. Taken from their website:
CloudFlare protects and accelerates any website online. Once your website is a part of the CloudFlare community, its web traffic is routed through our intelligent global network. We automatically optimize the delivery of your web pages so your visitors get the fastest page load times and best performance. We also block threats and limit abusive bots and crawlers from wasting your bandwidth and server resources.
One of the techniques used to protect CloudFlare's clients is to validate that the requests are coming from a legitimate browser. They implemented a simple but clever way to do this by forcing the client to evaluate Javascript in order to solve a mathematical challenge on the CloudFlare infrastructure. The client's request will make it to the real webserver only if the correct answer is provided.
Here is an example. On its initial visit to a CloudFlare-protected website, the client's browser is presented with a special Challenge web page.

This page contains a special hidden POST form to be used in order to submit the answer to the challenge.

Right below this form is a small Javascript snippet that computes a simple math operation and performs a POST on the previous form.

Normal web browsers will interpret the Javascript and produce an HTTP POST request similar to this one, which contains the response to the challenge.

If the answer is correct, the CloudFlare infrastructure will reply to the POST with a clearance cookie. Presenting this cookie along with any further HTTP requests will bypass the challenge and allow the request to reach the real webserver directly.
![]()
Bypassing the Javascript test
Of course, this looks like a trivial job for a typical web browser, but not for a dumb DoS script. And that's where the Win32/DoS.OutFlare.A is innovative, implementing some functionality to parse the challenge parameters, then compute and send the expression in order to obtain the clearance cookie which is necessary to perform an effective DoS against the real web server.

Extracting the challenge operation.

Computing the challenge.
Conclusion
The administrators at the domain being abused by this malware have been contacted (2013-02-08) regarding what seems to be a rogue subdomain registered without their knowledge. We have also spoken with CloudFlare. The company indicated that defensive measures were already in place to defeat this type of attack and of course they are continually enhancing the techniques used to thwart DDoS attacks on their customers.
Given the popularity of CloudFlare and similar services, it makes sense for the DoS malware out there to evolve techniques--such as we have seen in our analysis of Win32/DoS.OutFlare.A--to help them perform their nefarious operations more efficiently. However, services like CloudFlare are also evolving. Improvements to the technology are rolled out all the time.
While the code we see in Win32/DoS.OutFlare.A suggests that we might be at the beginning of an arms race between anti-DDoS services and commodity DoS malware, continued cooperation between security vendors and researchers will hopefully keep blunting the effectiveness of this particular type of malware.
CloudFlare's very interesting take on these developments can be found on the CloudFlare blog posted by CEO, Matthew Prince.
MD5 of the analyzed file: c0ea1a1b5a0cca645a5e06791784b279




